(in)Secure digest: boredom motivated attacks, love to fines and ethical hack
17.10.2022
Back to blog listThe new fine turned up unexpectedly
Situation: Morgan Stanley bank holding was fined $35 million for 14 million clients’ personal data disclosure.
Case study: U.S. Securities and Exchange Commission (SEC) claimed that the holding failed to ensure secure disposal of hard drives and servers, containing clients’ data. According to the Commission statement, Morgan Stanley had hired third-party companies for data carriers transporting and disposal. However, it turned out, that the contractors were not "competent" in the issue and simply resold thousands of Morgan Stanley devices to third parties, which then put them for sale on the Internet. As a result, banking holding’s 42 servers, which possibly contained unencrypted confidential data have disappeared without a trace.
It should be noted, that it’s not the first time when Morgan Stanley is blamed for negligence in terms of ensuring clients’ personal data safety. In January the banking holding was forced to pay $ 60 million for clients’ data leaks.
Ethical hacking
Situation: Indian airline company Akasa Air disclosed passengers’ personal data on the first day of work.
Case study: The data leak was detected by a cyberexpert. He told, that data on users leaked because of profile registration system’s malfunction. Due to this incident the following data was exposed: names, email-addresses, phone numbers.
The cybersecurity expert, who detected the data leak, tried to get in touch with the airline company’s information security department experts, but he didn’t manage to find contacts, thus, he had to get in touch with journalists for help. After it, the company temporarily disabled the registration system. The researcher noticed, that Akasa Air had been fixing the issue during two weeks. He also hinted that he may be the only one who found the vulnerability and it is unlikely that intruders have obtained client data.
Later, company representatives claimed, that no data, related to clients’ travels or payment details has leaked. Despite the volume of the data leak is not clear yet, Akasa Air has notified affected users and informed them about the possibility of ongoing phishing attacks occurrence.
Devastating links?
Situation: The largest hotel chain InterContinental Hotels Group PLC has experienced a hacker attack.
Case study: On the 5th of September hackers attacked IHG Hotels&Resorts company. Their malicious actions has resulted into switching off a few IT-systems. In order to perform the investigation, IHG has addressed third party cyber companies and notified regulators. The company representatives stated that booking systems and some services had been badly damaged.
The hotel chain official representatives have not revealed the peculiarities of the attack, however, there was an assumption, that a ransomware program was used. According to Hudson Rock, cybercriminals have managed to compromise approximately 15 employees’ accounts and gained access to data of 4.000 InterContinental Hotels Group mobile app users’ data.
There was a mistake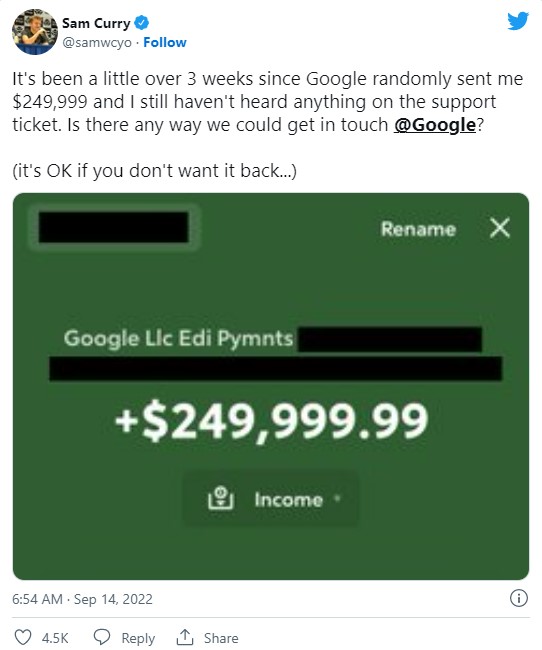
Situation: Google accidentally paid $250.000 as a ransom to the wrong person.
Case study: The mistake was obtained by Sam Curry, an engineer who searches for various vulnerabilities in companies’ infrastructures. He shared the fact, that Google mysteriously paid him nearly $250.000 via social network.
Later Google representative confirmed, that the company accidentally transferred money to Sam’s banking account. Although he could spend money as he saw fit, he saved them in case he got a reply from the company and even planned to transfer them to another account in order to avoid payment of taxes. Google representatives told that the recipient quickly notified them about the mistake, and that they are working on the issue.
Blame yourself
Situation: 18 y.o. person hacked Uber because the service wasn’t protected well enough.
Case study: The cybercriminal told The New York Times that he gained access to Uber email, cloud storage and code repository. Later the service representatives also confirmed the fact of service’s IT system hack and that they had to switch off some systems.
Cyber security specialist Sam Curry (yes, exactly that person, who accidentally received the $250.000 payment by Google) reported, that he’s still in touch with the alleged intruder. The hacker told Sam that he had the full access to Uber system.
Shortly before the service's system was turned off, some employees received a message from a hacker, in which he claimed that a data breach occurred and he proved that by sharing a list of a few databases he had managed to compromise. In his message the hacker also stated that that Uber drivers’ salary should be increased.
Company staff members revealed, that the person hacked an employee’s Slack account and used it to send the message. The cybercriminal himself explained The New York Times in details how exactly he hacked Uber.
It turned out, that he sent a message to a company’s employee and impersonated himself to be a corporate IT specialist. Later the hacker managed to persuade the employee to tell the password, which enabled him to access to Uber system.
Data lost
Situation: Employees of one medical structure lost the laptop, containing data on thousands of patients.
Case study: Basing on the investigation conducted, hospital specialists detected, that the notebook contained the following data on patients:
• names
• dates of birth
• medical chart numbers
• audiology tests’ results.
Although the laptop hasn’t been found yet, hospital representatives claimed, that currently they don’t have a reason to believe that the data was stolen and somehow used.
Easy come, easy go
Situation: Because of Coinbase third-party provider’s mistake, Georgia’s traders made a hundredfold profit.
Case study: According to blockworks, due to the Coinbase providers mistake, in the exchange rate of the dollar against the Georgian currency lari, the comma was shifted by two digits. Due to it, in seven hours $1 became equal to 290 lari instead of the proper 2.90. The company attributed the lost comma to a technical error, occurred at the side one of its partners. Supposedly the bug was used/exploited by approximately 900 people, and crypto-experts estimated Coinbase loses as of from $14 million to $140 million. Admittedly, it did not last long. Local banks tracked the suspicious transactions and blocked the accounts of the enterprising traders. Now Coinbase is trying to recover the illegally withdrawn funds.
