Any employee might do it – SearchInform revealed the most frequent security incidents within companies.
SearchInform analytics have summed up the most frequent incidents detected in client companies.
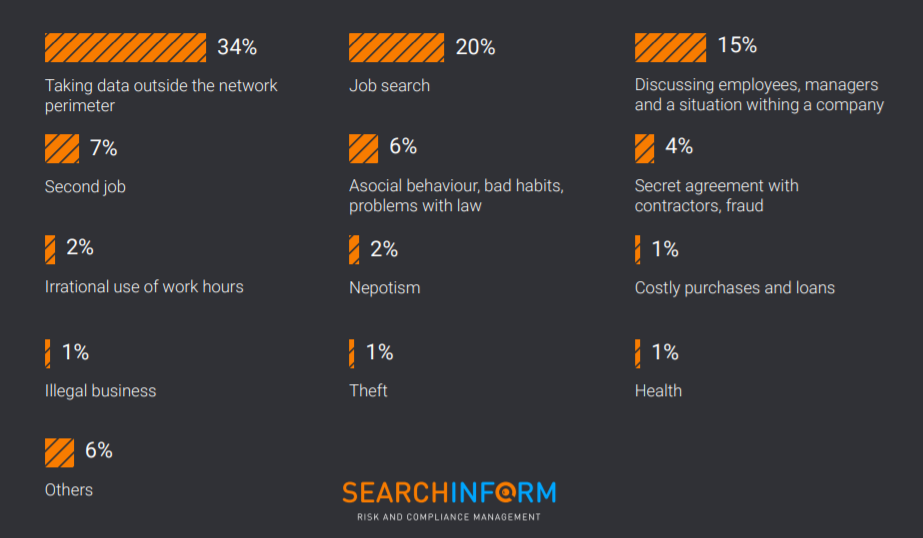
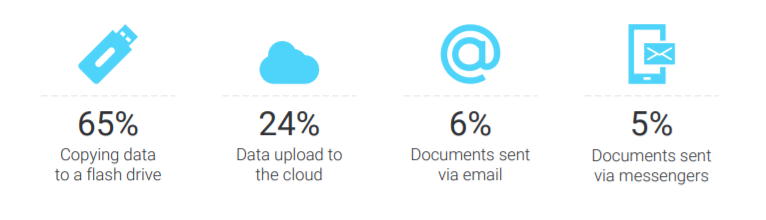
The most frequent violation which gets detected by risk management specialists is the leakage of information which constitutes nearly 1/3 of all incidents – they were detected by 100% companies. The documents are often uploaded to flash drives (65% of all data leaks) and to the cloud (24%).
Data leak channels
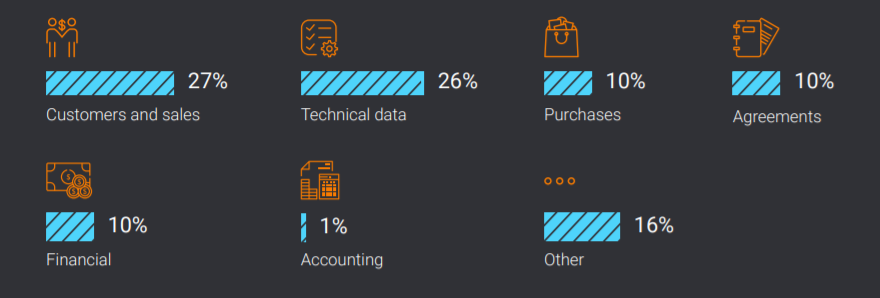
Data leakages compromise information about clients and deals (databases, personal data of VIP clients) and technical documentation – in 27% and 26% of cases respectively. 1% of data breaches is the leakage of accounting data, 10% - financial and 10% as well – tender documents, agreements.
What gets leaked?
The other two prevalent groups of incidents regard spreading negative opinion about the company and colleagues, and job search. They constitute 15% and 20% of all incidents respectively. They concern security as they are often accompanied with data loss risks including those in favor of competitors and reputation damage.
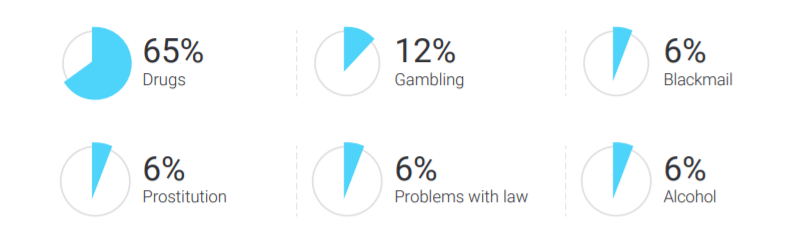
6% of incidents – identified asocial behavior of employees, risks concerning gambling, blackmail, drug addiction. Drugs account for the absolute majority of identified incidents within this group of violation types. During providing of the services analysts found correspondence in which purchasing and taking drugs were discussed as well as traces of visiting certain websites on the dark web.
Asocial employee behavior
Another group of incidents includes employee fraudulent scheming. These are various options for lobbying the interests of affiliated counterparties, conspiracies with contractors, side schemes, side jobs. They account for 4% of all detected violations in total. In particular, one of the companies discovered an illegal project within the corporate perimeter which showed three current and five former employees involved. These are the most dangerous incidents for financial wellbeing.
Irrational usage of work hours and sources constitute 2% of all incidents. But their detection allowed companies to optimise team work. Particularly, in one of the companies 300 out of 360 people were identified as “suspicious”. This let managers abolish not overloaded positions and allocate work among other employees.
Alexey Parfentiev, leading analyst at SearchInform:
We have analysed companies’ data from various industries: finance, logistics, retail, IT, manufacture, agriculture, services. The most unappealing fact is that 100% of organisations detected serious information security violations.
Our specialists detected not only insiders or those who received kickbacks. Risk mitigation professionals identified employees in groups of high violation risk, employees working for other companies during work hours or desperate gamblers who would indulge into their obsession every day. Companies get to data leakage prevention and reveal corporate fraud or managerial error. This proves the tendency that information security tasks are now something bigger than mere leakage prevention and are related to a much wider range of incidents.
Learn more about the situation within your company. Request a free 30-day trial of the services based on our internal threat mitigation platform.
SearchInform uses four types of cookies as described below. You can decide which categories of cookies you wish to accept to improve your experience on our website. To learn more about the cookies we use on our site, please read our Cookie Policy.
Necessary Cookies
Always active. These cookies are essential to our website working effectively.
Cookies does not collect personal information. You can disable the cookie files
record
on the Internet Settings tab in your browser.
Functional Cookies
These cookies allow SearchInform to provide enhanced functionality and personalization, such as remembering the language you choose to interact with the website.
Performance Cookies
These cookies enable SearchInform to understand what information is the most valuable to you, so we can improve our services and website.
Third-party Cookies
These cookies are created by other resources to allow our website to embed content from other websites, for example, images, ads, and text.
Please enable Functional Cookies
You have disabled the Functional Cookies.
To complete the form and get in touch with us, you need to enable Functional Cookies.
Otherwise the form cannot be sent to us.

Subscribe to our newsletter and receive a bright and useful tutorial Explaining Information Security in 4 steps!

Subscribe to our newsletter and receive case studies in comics!