SearchInform solution
in the cloud
Data protection with no need to purchase a server.
Control of branch offices and remote employees.
SearchInform provides its customers with information security from the cloud. If you don’t prefer to make a one-time payment for software and hardware, you can get data protection on a subscription basis - as a service.
It means that you don’t need to acquire:
server (or allocating one in case a company has an assigned server)
software license
for each workstation
third-party software license
(MS SQL, etc.)
Who benefits from the cloud deployment model?
-
Small, medium and large enterprises without in-house
IT infrastructure (email servers, VPN, NAS, etc.) -
Companies that don't have full-time specialists for risk mitigation, system deployment and management, or their personnel is overwhelmed
-
Entities that prefer to pay for the service once per month, allocating their budget smartly
Cloud safety
Today, many IT product developers are looking for ways their systems can be implemented in the cloud. The most popular cloud providers comply with stringent regulatory requirements, offer access to additional security configurations, guarantee the confidentiality of client data, and as large companies they are better at protecting themselves from DDoS attacks than individual customers.
Learn how to protect your company with SearchInform cloud solution
virtual machine
virtual desktop
(+ installed
SearchInform
solution)
(+ installed
SearchInform
solution)
(integration)
(+ installed
SearchInform
solution)
Why Azure?
Multilevel protection
Inbuilt management elements
International regulatory compliance
Everyday analysis of 8 trillion threat signals
Large-scale intelligent analytics tools
Seamless data exchange between all the components of protected infrastructure
How does SearchInform solution work in the cloud?
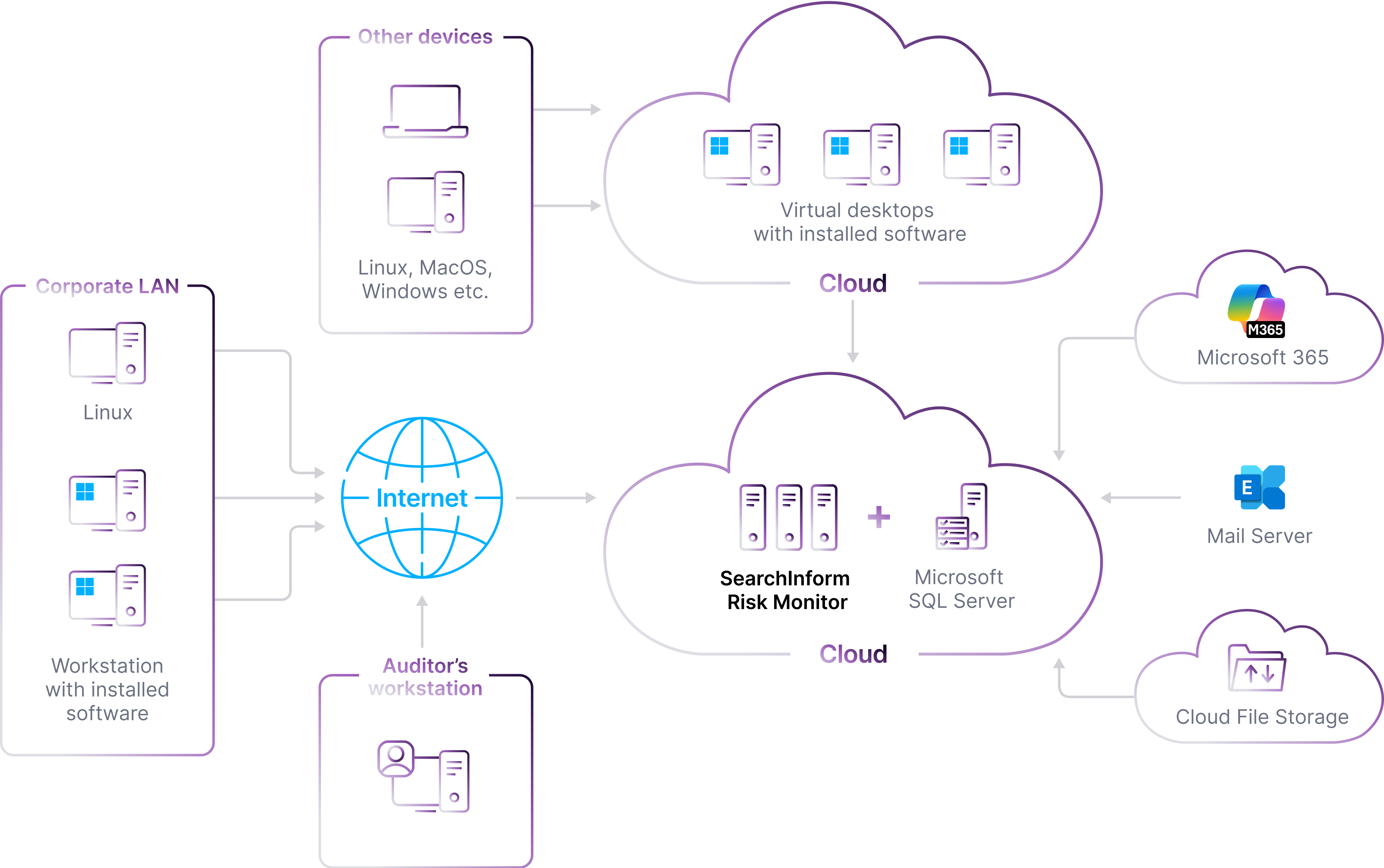
Cloud options
SearchInform cloud
We install all SearchInform solution components. Data is processed and stored on SearchInform servers.
Other cloud service
We deploy SearchInform components in the cloud chosen by the client. Data is processed and stored on the provider’s side.

Get in touch with our expert to know more about SearchInform solutions in the cloud.
SearchInform uses four types of cookies as described below. You can decide which categories of cookies you wish to accept to improve your experience on our website. To learn more about the cookies we use on our site, please read our Cookie Policy.
Necessary Cookies
Always active. These cookies are essential to our website working effectively.
Cookies does not collect personal information. You can disable the cookie files
record
on the Internet Settings tab in your browser.
Functional Cookies
These cookies allow SearchInform to provide enhanced functionality and personalization, such as remembering the language you choose to interact with the website.
Performance Cookies
These cookies enable SearchInform to understand what information is the most valuable to you, so we can improve our services and website.
Third-party Cookies
These cookies are created by other resources to allow our website to embed content from other websites, for example, images, ads, and text.
Please enable Functional Cookies
You have disabled the Functional Cookies.
To complete the form and get in touch with us, you need to enable Functional Cookies.
Otherwise the form cannot be sent to us.

Subscribe to our newsletter and receive a bright and useful tutorial Explaining Information Security in 4 steps!

Subscribe to our newsletter and receive case studies in comics!




















