FileAuditor
Ensures content based access rights distribution and makes sure
that everything is put in order in your corporate file system.
How does
SearchInform
FileAuditor work?
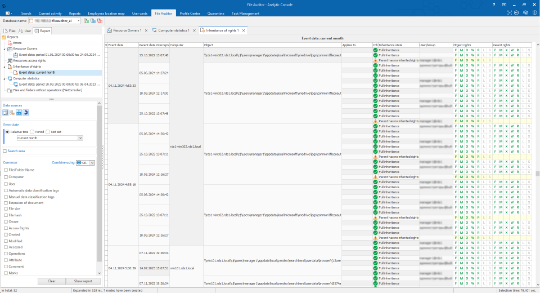
The system obtains the file
The file is checked against
the policies and is marked with
a special label
If necessary, the file is
copied to the vault
Blocking activities
and applications related
to marked files
All actions with files and
folders are logged
Permission for files
and folders are read
During subsequent checks,
the system scans only newly added
and changed files


Gartner introduced the Data-Centric Audit and
Protection (DCAP) approach as highly recommended
to mitigate threats and compliance issues to critical
data. DCAP strategies are replacing disparate siloed
data security governance approaches.
What tasks does
FileAuditor solve?
Data classification
Each document is labelled according
to the type of data it contains.
The automatic classification can be
complemented with manual for most
efficient protection.
Access rights audit
Controls access rights to information
(full access, editing, reading, writing,
reading and changing, print restriction etc.)
depending on the policies set.
Monitoring and blocking user actions
Audits user operations with the file
system. Reveals all data on the lifecycle
of a file. Blocks access to the file and
its transfer in any application.
Critical documents archiving
Makes shadow copies of critical files
found on the workstations, server or
in network folders, saves the history
of their revisions.
The FileAuditor performs content based data
protection, what ensures the highest standard of
data security, unavailable in any other solution
and helps to manage data efficiently.
Thus, regardless of:
- Change of attributes.
- The type of file, containing confidential data and whether confidential data is present in the form of a picture, a document or a document with a picture.
- Program used for opening a file.
-
With DLP
Enables to perform immediate and accurate blocking of data leakage attempts and significantly reduce the load on the infrastructure.
-
Huawei OceanStore and other SANs
Ensures protection of confidential documents kept in the corporate storages, as well as ensures control access to data, allows to trace changes done to files.
-
With SIEM system
Enhance of SIEM’s analytical and operational capabilities. Detailed data on files directly from an endpoint, provided by FileAuditor, helps to extend the list of policies and fine-tune them.
-
Microsoft MIP and other systems for data classification.
The FileAuditor is capable of reading labels, added to files by other solutions and takes them into consideration.

explore more about SearchInform
product modules and their capabilities
in a Module Comparison Table
Explore more

Start Your Free 30-day
Trial Now!
Reviews
Information Services

“With the SearchInform solution, we improved employees' performance by monitoring their daily behaviour. At first, the system seems complicated, but after you start working with it daily, you intuitively understand everything.
The system is transparent to the end user. With two clicks, you can track everything the user did with the information.”
Information Technology and Services

“The SearchInform risk monitoring is an awe-inspiring tool. I have never seen a tool that collects so many data from a computer and organizes it in a way to be clear about what was made in the hosts. It is pretty useful to collect evidence on actions of internal users from conversations, accesses, software that were used, the path from where a data was collected to where it was sent, and even capturing from webcam, microphone and displays.”
Computer & Network Security

“The next-gen DLP - Risk Monitor is such a comprehensive solution that has a function for every department in your business. This solution is the only solution we are familiar with that can reveal the fraud and empower risk managers and C-Level executives to protect organization's digital assets, and increase staff performance while at the same time prevent the wide range of risks.”
Industrial Automation

“SearchInform solutions give all you need to monitor your data, network, and hardware, so you can make necessary enhancements to your information security system and IT infrastructure as a whole.”
SearchInform uses four types of cookies as described below. You can decide which categories of cookies you wish to accept to improve your experience on our website. To learn more about the cookies we use on our site, please read our Cookie Policy.
Necessary Cookies
Always active. These cookies are essential to our website working effectively.
Cookies does not collect personal information. You can disable the cookie files
record
on the Internet Settings tab in your browser.
Functional Cookies
These cookies allow SearchInform to provide enhanced functionality and personalization, such as remembering the language you choose to interact with the website.
Performance Cookies
These cookies enable SearchInform to understand what information is the most valuable to you, so we can improve our services and website.
Third-party Cookies
These cookies are created by other resources to allow our website to embed content from other websites, for example, images, ads, and text.
Please enable Functional Cookies
You have disabled the Functional Cookies.
To complete the form and get in touch with us, you need to enable Functional Cookies.
Otherwise the form cannot be sent to us.

Subscribe to our newsletter and receive a bright and useful tutorial Explaining Information Security in 4 steps!

Subscribe to our newsletter and receive case studies in comics!