By Sergio Bertoni, The senior analyst at SearchInform
Enhancing users’ computer literacy; cyber hygiene; basics of safe Internet usage, etc. These are all names, which stand for IS department employees’ most painful tasks. It usually turns out that regulations and job descriptions, despite their importance, aren’t sufficient. What’s more, it’s required to somehow train employees not to commit dangerous actions. Unfortunately, there isn’t a panacea. But I will share my personal experience and advice on how to enhance employees’ IS-related competencies.
Methods for enhancing users’ awareness
First of all, a few words about methods.
I suggest to consider the following activities as educational methods:
- Briefing
- Demonstration
- Trainings and games
- Full-scale cybertrainings.
When a briefing is organized, employees are passive. They just need to read/listen/look. For instance, examine the job description.
Visual demonstration is an advanced training. An employee still doesn’t participate in the process, however, there is a difference in the way the information is presented. Visual demonstration technique implementation has the following advantages:
- More practical examples
- More real life examples
- More demonstration.
This may be, for instance, a webinar, during which an expert shows screenshots, videos etc.
Trainings and games involve users in the process, and students become active participants: they get practical tasks and deal with them. Quite often, they also discuss the results.
Finally, cyber trainings. The main difference of this game is that the employee doesn’t know that he/she plays the game. Briefly speaking, first an employee is deceived with the simulation phishing email, then he/she receives a notification, then a link to a training course.
Each method can be implemented in different ways. For instance, the game maybe a text quest, quiz, browser game with battle royale elements etc.
The final choice depends on a few variables:
- Budget allocated
- Time available
- Knowledge.
The tricky moment is that if you really want to enhance your employees’ competencies, a single method implementation may be insufficient. People are different, each requires personalized approach. For instance, some people can easily get all the required information by reading a document, while others need the data to be presented in a form of video.
Below you may find a list with a few methods of explanation of rules for crypto-resistant passwords creation to different types of employees.
For impressionable employees
Quite often, online services show users, whether their password is really a reliable one when registering an account. Some reveal, whether the password is an appropriate one. Others visualize passwords’ crypto-resistance: depending on the password’s complexity, a user sees red, yellow or green indicator. Others show the approximate time, required for password brute-force.
So, different services may be used for explanation of the following basic ideas:
- Password, which seems to be a reliable one, may not be the reliable at all
- Passwords are cracked quicker than users usually think
- Services sometimes provide users with inaccurate data on their passwords crypto-resistance.
For impressionable, but curious employees
There is an illustrative scheme on the topic of brute force attacks.
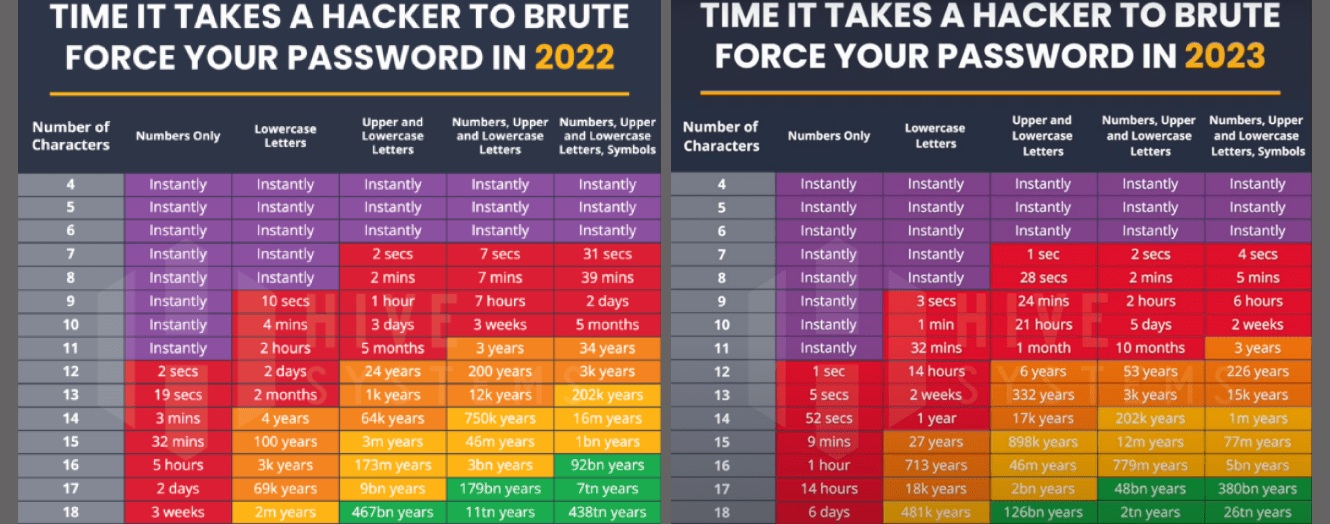 Note: please pay attention, how the numbers changed within a year.
Note: please pay attention, how the numbers changed within a year.
For those, who love to substantiate everything with numbers and formulas
There are always some employees, who aren’t be persuaded with such schemes/pictures. Such people tend to search for objectivity and ask such questions as: What was the methodology? Where are the specifics?
When working with such employees, I recommend to rely on research from more reputable organization: for instance, international and national research institutes and large IT-corporations, which have departments, responsible for development of password guidelines for the whole sphere.
Experts of such organizations consider the entropy, which is the numerical value of the so-called random combinations, which are contained in the code phrase. Entropy is calculated in bytes with the help of algorithms, which consider the length of password and the symbols contained.
In bytes the password reliability is calculated the following way:
- Passwords up to 28 bytes refer to the very weak category and it’s strongly advised not to protect anything valuable with such passwords
- 28-35 bytes passwords are weak ones. Such passwords can counter inexperienced hackers or simplest algorithms and may be implemented on desktops, on which no confidential and secret information is kept
- 36-59 bytes – such passwords may be used for protection of PCs within the corporate network
- More than 60 bytes – very crypto-reliable passwords
- More than 128 bytes – extremely crypto-reliable passwords, recommended by the NIST. It’s believed, that until the 2030, it will be impossible to crack such passwords.
For creative people
Creative people often fall victims to overestimating their fantasy power. For instance, there is a quite widely spread misbelief that if some standard password is complemented with a few atypical elements, it immediately turns into a reliable and crypto resistant password.
The same story is with graphical passwords. Psychologists (as well as malicious actors) are acknowledged about human beings’ craving for beauty, or for what people consider to be beautiful. (Research Visualizing keyboard pattern passwords. Authors: Dino Schweitzer, Jeff Boleng, Colin Hughes, Louis Murphy. US Naval Academy.I didn’t manage to quickly find the original of the research, however, below you may find the link to their presentation.
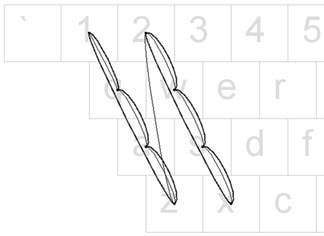
That’s why when using graphical passwords we tend to use symmetrical lines, or at least something well-known and easily recognized, e.g. lines in form of letters (Research Tell Me Who You Are and I Will Tell You Your Unlock Pattern, Marte Løge).
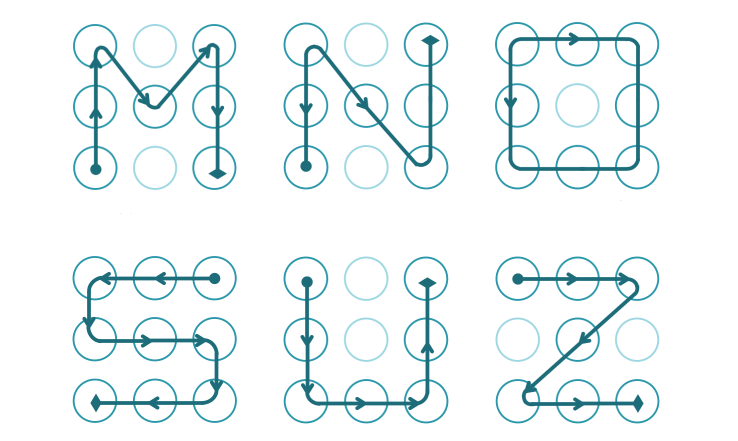
Such users may be impressed even with the list of most common passwords. But the most important is that it should motivate the users to develop their creativity.
For those, who prefer to practice
It’s a good idea to demonstrate such users the power of brute force attacks. You don't need to train users in hacking techniques, but you can show them some basics in your own example and reveal the basic principles.
The most important is to reveal that in case patterns (templates) are used, this fact is easily detected (there is a tremendous amount of recent data leaks). And if the pattern is known, it’s an easy task to generate a dictionary basing on this pattern.
For example; using a virtual machine and considering that it is not very powerful, let's consider the password of any 4 letters + year of birth. Quickly generate a dictionary in real-life mode and then implement the dictionary search. The result is in the screenshot: in our case, it took a little over 12 minutes to choose the correct password.
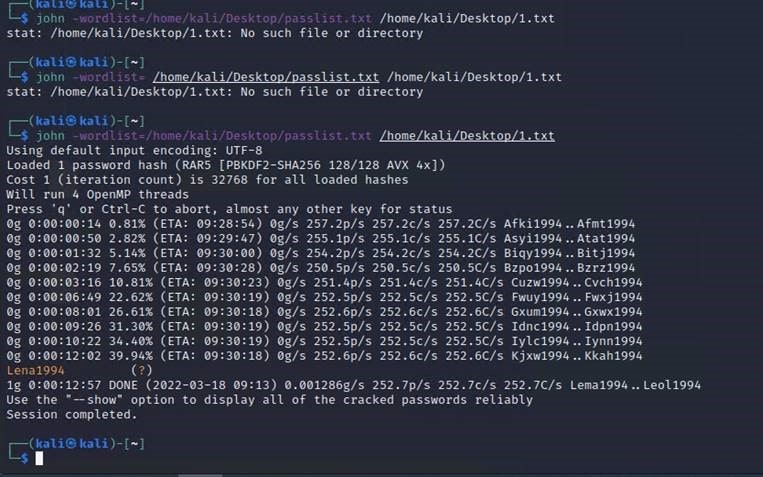
Outcomes
On the Internet you can find plenty of other useful links to illustrations, trainers, lifehacks. Thus, there is no need to start from scratches and develop everything on your own. It’s more important to organize everything appropriately.
In this article I’ve described a few approaches. The most important thing is to choose the right approach for the target audience in order to involve them in the process of dealing with information security tasks/problems. I wish you all success in the educational process.
With SearchInform Risk Monitor, you can protect your organisation from financial losses due to internal threats at all levels of corporate information systems. Follow the link to get a trial period, it's free for the first 30 days.

Subscribe to our newsletter and receive a bright and useful tutorial Explaining Information Security in 4 steps!

Subscribe to our newsletter and receive case studies in comics!