By Sergio Bertoni, The senior analyst at SearchInform
In 2020 we released our own DCAP class solution – SearchInform FileAuditor, which was developed for control and protection of data at rest. Since then we’ve presented our system hundreds of times and revealed, how useful the system is in real life and how exactly it helps to keep everything in order in corporate storages. We’ve also gathered statistics, provided by our clients. It turned out that in almost all cases of audit with the help of FileAuditor, violations in access rights distribution, inappropriate keeping of confidential files, as well as other issues, related to resource overrun were detected. I’d like to notice that, first of all, we always test our solutions ourselves. Today we decided to reveal a few illustrative cases of how we performed audit of our own file storages and share that the statistics, provided by clients, isn’t an exaggeration.
The initial data
Any DCAP class solution has to deal with two basic tasks: search for files and managing of access rights to them. In this article, we’ll focus on the first one. We had the task to perform the inventory of file storages. The first step of our experiment was to find out how the storages are used and how are the documents, which fall into the critical categories (containing some very confidential/sensitive data) are kept. The task was solved with the help of FileAuditor solution.
Basically, the solution work process is based on the following principles:
- It scans all storages and classifies files according to their content: for instance, personal data or source code and adds the appropriate labels to files.
- Monitors all operations with files, reveals, who and when worked with file and what operations exactly were made, for instance, if a file was renamed or transmitted anywhere.
- Traces access rights and finds out violations in files and folders access rights distribution; enables to manage users’ access rights for performing some specific operations, for instance: reading, editing, deleting etc.
- Blocks unwanted operations with files according to the rules, configured beforehand. For instance, prohibits to open files via some specified applications or blocks attempts to attach files to emails.
- Makes backups of required types of files just in case they are lost or stolen.
The solution works via agents on users’ PCs, network folders are scanned with the help of network service.
In our case, the system had to check 170 PCs of a few department employees (each of them had approximately 750 GB of data to be examined) and shared network folders.
It's required to notice that in this article we basically describe some specific tasks, which are relevant specifically for our company or tasks, which aren’t very common in order to reveal how exactly we configured the system. We’ve successfully dealt with most typical tasks, such as categorization of numerous types of personal data, correspondence, labelled documents, contracts, acts, invoices etc. before the experiment with the help of FileAuditor pre-configured policies. There are more than 80 such policies available, we’ll focus on them later.
Now let’s proceed to the experiment itself.
Resource overrun
We’ve started with some practical tasks – a few managers reported that there was too small free space on their machines. Before providing them with additional resources, we decided to analyze, what data is kept on their PCs and why they are clogged. Basing on our clients’ experience we knew that FileAuditor frees up to 40% of file storages’ space, basically, by deleting copies, outdated documents and trash, which isn’t related to employees’ job duties. There was a suspicion that the case of our employees was a similar one.
We’ve configured a few rules to perform the audit. In order to be able to monitor how many documents refer to the required category and how much do they weigh we used the specific report on PC statistics and assessed the results basing on this report.
1. Search for “heavy” files
The most heavy item, which could be kept on managers’ PCs were virtual machines, which are used for live demonstrations of our solutions for clients.
From time to time we release updates of virtual machines, this approach is more universal than to write manuals, describing what should be reconfigured and added to the old versions. However, users sometimes forget to delete old files, and it should be noticed that each virtual machine requires 40-60 GB of free space.
We’ve configured the classification rule for virtual machines, according to the .vdi extension in FileAuditor. The scanning was performed on all PCs, however, lately we excluded testers and developers’ machines when we analyzed the results of testing, because it’s fine for them to keep a few environments on machine simultaneously.
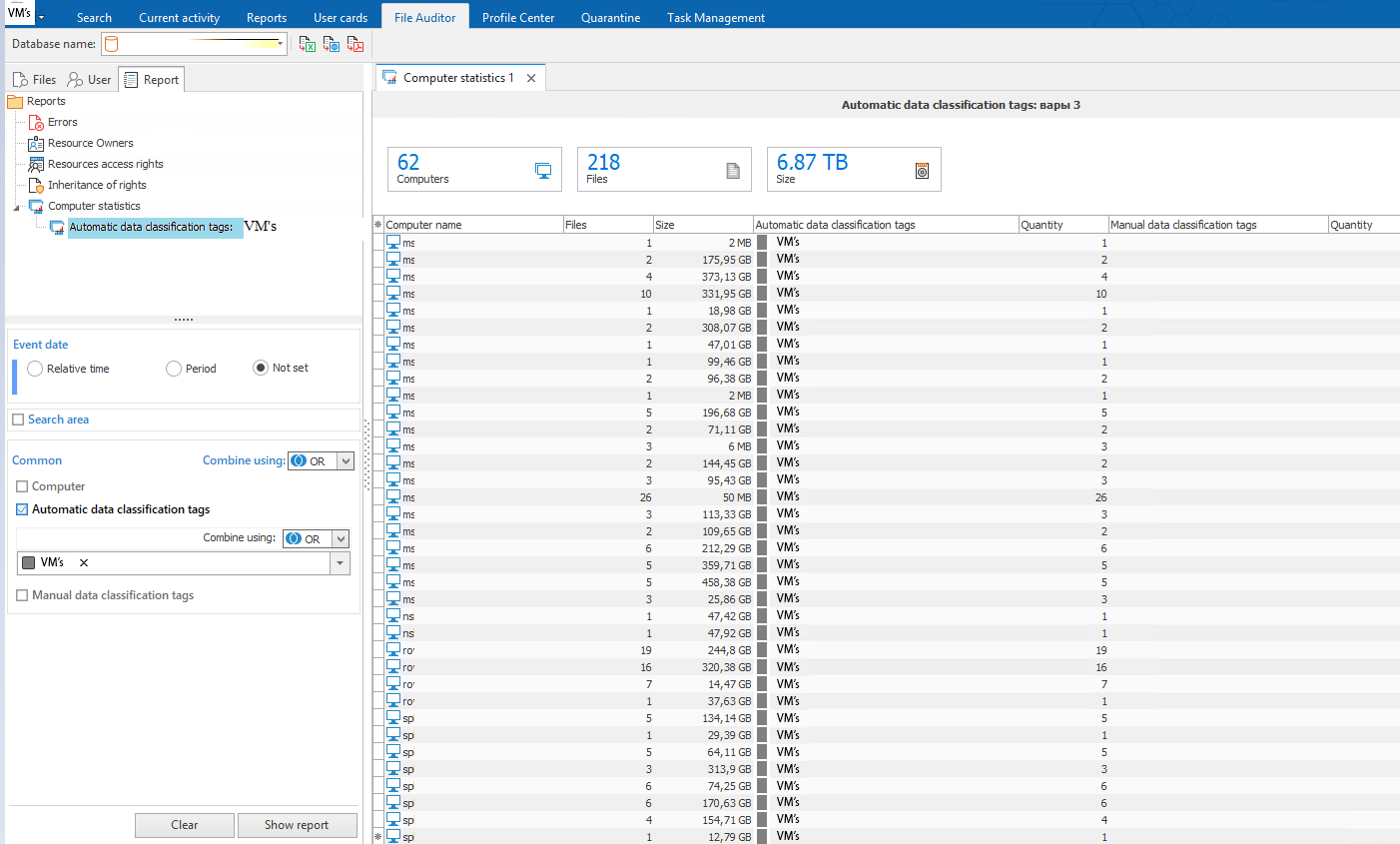
All in all, extra copies of VM’s were found on 17 PCs, overall, 1,39 Tb of extra data was kept. We also found out that four managers kept a few environments simultaneously, one manager even had 8 of them. So, we had to remind one more time that old versions of virtual machines should be deleted.
2. Search for multimedia
Work with audios and videos corresponds with the PR department specialists’ job duties, as they are in charge of development of media content. In all other cases media content kept on corporate devices poses a risk of irrational resources usage, as multimedia files require a lot of space, in other words, overload storages, and in case plenty of multimedia content is downloaded via corporate Wi-Fi – the network is irrationally overloaded.
In FileAuditor we’ve created the classification rule basing on the files’ extensions: mp4, wav, avi etc. The scanning was activated on all PCs and in network folders, however, we excluded PR storages when analyzed the results.
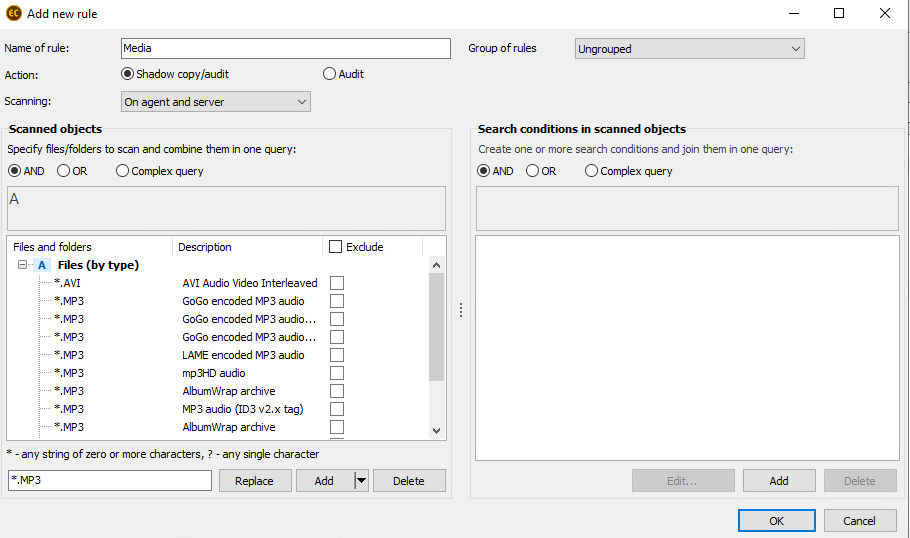
Configuration of classification rules
Overall, we’ve found 626 GB of data, which seemed to be trash, and it turned out, that top violators were developers and testers. Approximately 30% of all this irrelevant data was kept on computers of two employees: one of them kept 144 GB of music, the second one kept 75 GB of music. For comparison: employees of the PR-department (who are in charge of media content production) altogether kept only 25 GB of media.
 Audio library of the employee
Audio library of the employee
3. Search for outdated documents
There was a task by company’s executives – to remove the outdated technical documentation from corporate PCs. These documentation included files, containing:
- Mentions of products that were no longer on sale
- Irrelevant features
- Outdated names: for instance, controllers in our DLP solutions were previously named sniffers.
If such documents are present in the corporate document flow, this may mislead customers, affect business processes or even lead to fraud. In turn, if such files are kept, but aren’t used, they uselessly overload the corporate storages and, thus, it’s required to clean up the corporate infrastructure from them.
We’ve performed search basing on two criteria. First of all, we’ve added classification rules, configured according to the specific text attributes search, which included product names and outdated technical requirements. As the outdated ones we considered, for example those, which contained mentions of sniffer instead of controller. However, there was a nuance: different words could go together with the sniffer, so, the rule was complemented with search by character sequence.
Secondly, we’ve set the classification rule based on the attributes: the last interaction with the file had to be more than 5 years ago. This was required to obtain outdated files, which weren’t used any more.
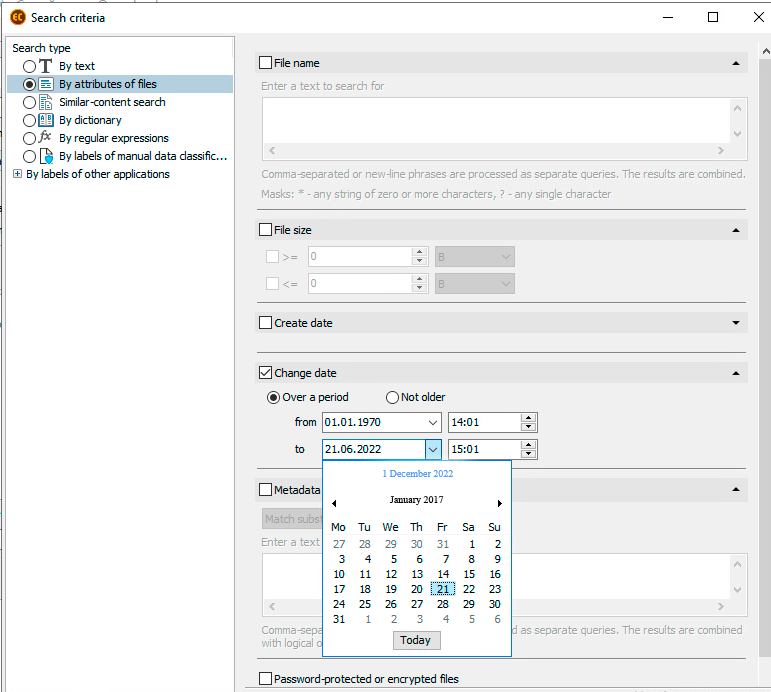
Configuration of search for out-of-use documents rule
Overall, we’ve found 2726 outdated documents. As it was revealed, PR department staff members kept large trove of old marketing materials in the network folder, what’s more, these documents were also kept by sales managers. Outdated technical documents were also kept by programmers, testers and even technical support engineers. Some documents were even actively used: basing on the archive of operations we found out, who and when worked with files. Luckily, the outdated files weren’t sent to customers, however, just in case, we conducted a newsletter and explained our employees, where exactly they can find the relevant up-to-date documentation on products.
We found out that all users kept some out-of-use documents. In total, they occupied 214 GB of space. Most often, such files turned out to be data archives. Quite often they also turned out to be files, which ex-employees shared with new colleagues when they just joined the team. In theory, it should had helped not to interrupt business processes, that’s why we referred such findings to legitimate category, even though no one worked with these files for a while. So, we asked heads of departments to make sure that everything is put in order in network folders and asked everyone to remove trash from their computers.
In addition we also decided to get rid of all documents in outdated design, this was the requirement by PR department employees. After the rebranding we changed the corporate style. However, some internal documents and some materials for clients were still in outdated design.
This task turned out to be more complicated one: it was required to find documents of different formats, types and content. So, we’ve configured the search according to the phrase, which was the slogan from an old logo, previously placed in headers.
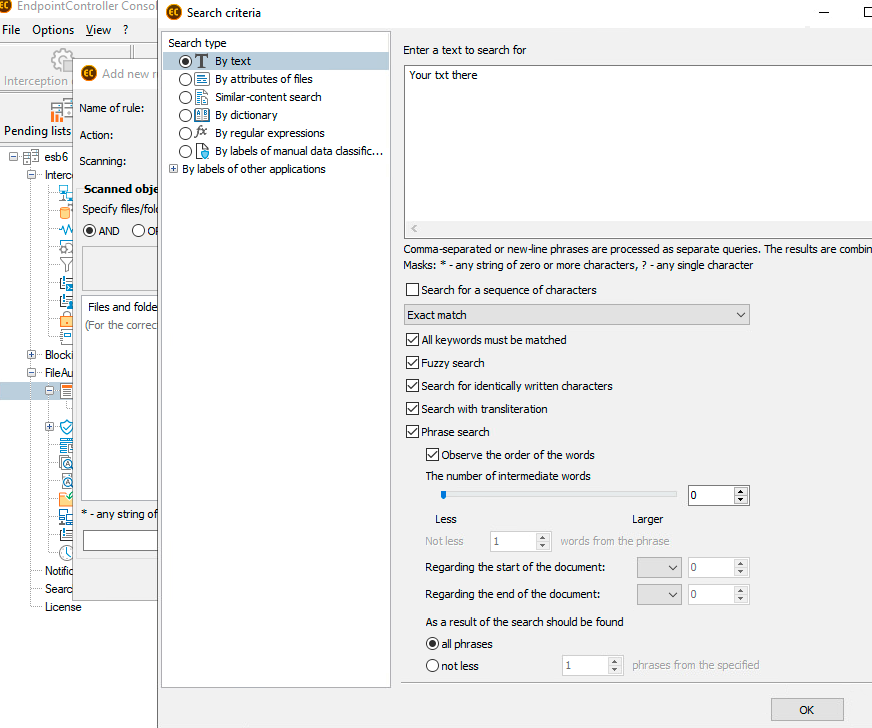
Parameters for search of documents, containing outdated slogan
We’ve obtained plenty of such documents, however, only two employees kept them. What’s more, one employee used these documents when testing our DLP and DCAP solutions. It was easier with our second employee – it was enough to talk with the employee and he instantly deleted outdated forms. Our PR department employees also reminded everyone about the requirement to use Brand Book.
Inappropriate keeping of data
The main task was to find documents kept by employees in violation of security rules. There were two ways how we could deal with this task.
The first one was to analyze business processes and find out, which employees took part in specific operations, where to exactly were the documents transmitted etc. Then, all the deviations from the sample were added to violations. The second option was to find out all the documents, kept in violation of security policies established (in other words, if documents were kept inappropriately).
The second option is easier and more comfortable when many PCs and large troves of data should be processed.
When preparing the plan, we, first of all, considered operational risks. For instance, all forms of personal data keeping and processing related processes are regulated by law requirements, incompliance with them leads to fines. What’s more, we also considered fraud probability, side companies and other economic security threats. As a result, we searched for documents, referring to the personal data type and other suspicious files, which indicated the probability of fraud.
1. Search for personal data
Below you can find an illustrative case of search for passport scans. We excluded PCs of HR and Accounting department employees from the search, thus, any case of detection of passport data keeping on computer was considered as a violation (there was no need for other employees to keep copies of passports on their computers). We configured search according to regular expressions in FileAuditor (passport ID) and connected OCR to read text on images. We also specified the request with the phrasal search: added words Passport, Issued etc. We also specified the attributes to check only graphic files during the experiment.
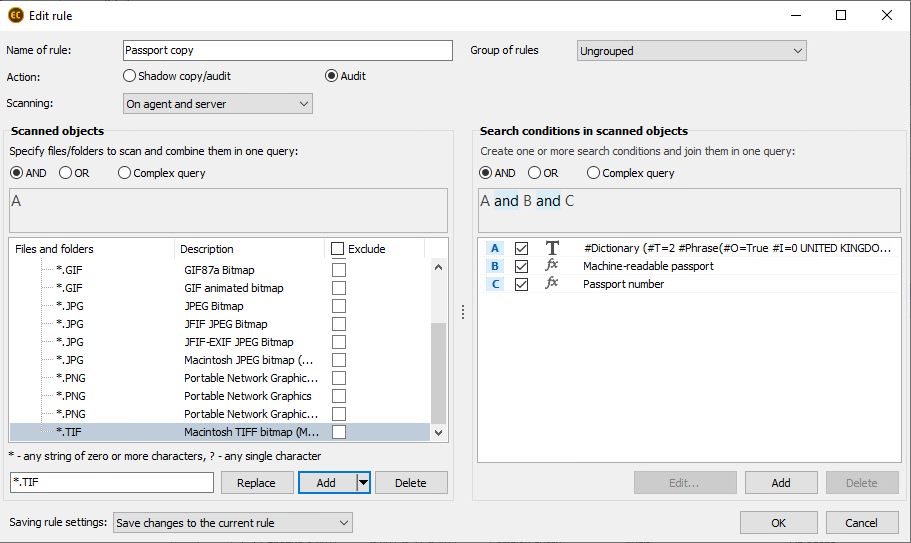
Configuration of classification rules for passport copy search
Our team is highly disciplined, thus, there were practically no responses. Third-party’s personal data was kept only on one employees PC, however, even this was an accidental incident. As it was revealed, the problem was in the inappropriate scanner usage. It had an option of saving the image scanned directly to the folder on a specific PC. The PC was chosen from the list before scanning. Employees from time to time accidentally chose the first PC from the list and sent images to that PC. As a result, a few irrelevant files were saved on the PC, however its owner even hadn’t an idea that the documents, including password copy, were kept on his computer.
2. Search for third party companies’ charters
Presence of companies’ charters on employees’ PCs indicates a risk that they commit fraud, for instance, they may be in collusion with a counterparty or may run a side company. In the FileAuditor we configured the search for similar rule. Then we uploaded an example of a company charter to the solution and added the company name and details to the exceptions.
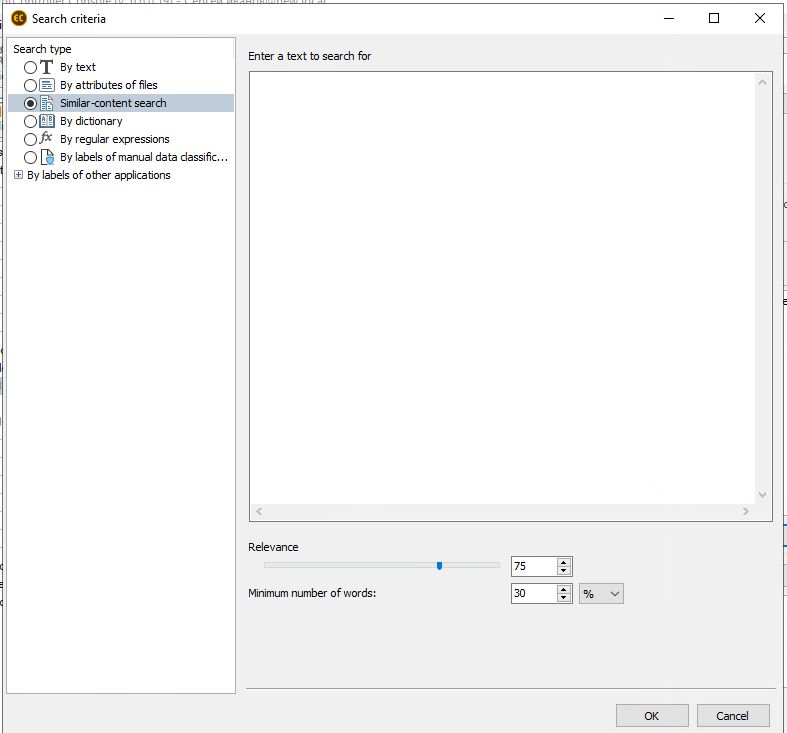
Configuration of the classification rule
A few such documents were obtained on the testers’ PCs. However, it was revealed that in fact these documents were just examples used for testing our DLP and FileAuditor solutions.
Besides, the standard classification rules are configured nearly the same, with their help it’s possible to search for all typical documents, such as acts, invoices etc. avoiding false positives. In other words, with the help of DCAP solution it’s possible to solve not only security tasks, but enhance efficiency of document flow as well.
A bit of outcomes
As it was expected, thanks to the experiment we’ve obtained a few shortcomings. The file system audit was for our own good. As a result, we’ve managed to clear some space, and another impetus was when we conducted preventive talks. If employees know that the audit of how files are kept is performed, they are more careful in terms of keeping files. What’s more, audit enabled to assess the efficiency of business processes – for example, we managed to optimize some of these processes and also gathered some useful information for future.
Basically, it’s not a typical information security task to deal with resource overrun, however, it’s just the first step. In the following articles we’ll reveal, how we dealt with the task of access rights audits and dealt with corresponding issues.
In case you wish to try the FileAuditor solution, you may visit the product page and require a free trial. During the trial term, you’ll be able to put the corporate file system in order and reveal whether there are serious violations of data keeping related process present in your infrastructure.

Subscribe to our newsletter and receive a bright and useful tutorial Explaining Information Security in 4 steps!

Subscribe to our newsletter and receive case studies in comics!