By Sergio Bertoni, The senior analyst at SearchInform
The second task of the self-test was to check whether user access rights were distributed appropriately and eliminate violations (in case of detection).
1. Access rights audit
The task in this case was clear right from the beginning – we had to compare the benchmark access control matrix with ours.
A few reports in FileAuditor, including the one aimed at audit of inherited permissions and classic access log help to perform such a check. The access log was used for performing analysis of network storage. We checked, whether groups contained extra users (the ones, who shouldn’t be included there).
The report itself enables to monitor all the directories with the list of users and groups, who have access to them. However, in this case you get too much results and it’s quite difficult to detect deviations, so, the mini-version of the report came in handy. It can be obtained in the File preview mode when choosing a specific directory in the Console.
In this mode FileAuditor reveals details on access rights by retrieving this data from the file system resources. Thus, the IS officer can instantly see, which users can interact with a file / folder and what actions exactly are available for them. It’s also useful that it’s possible to reconfigure users’ access rights in the work console with a single mouse click. This is much more comfortable and quicker then to deal with the settings in the OS manually.
We didn’t detect any violations, as our system administrators usually appropriately moderate user groups and assign users’ access rights according to the benchmark matrix.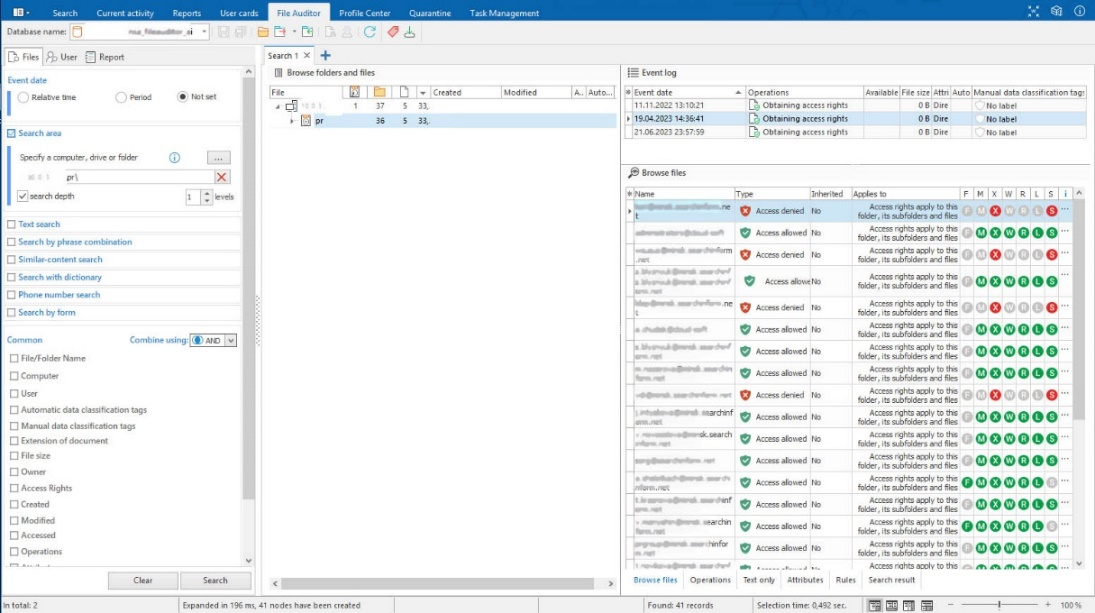 Viewing of access rights to the department’s folder
Viewing of access rights to the department’s folder
However, there is no rule without exception. We’ve detected an issue with network shares. It’s the ideal scenario if only employees of the department, system administrators and the Head of IS department have access to such folders. However, in reality, it turned out, that in some cases, users of other departments also had access to these folders. The problem was with the former employees’ accounts – in fact they were blocked and didn’t pose any information security risks, however, there was a mismatch in the number of users who should have had access rights and who actually had it.
What did we do: we had a conversation with system administrators and put everything in order in Active Directory.
We also referred to the Inheritance of rights report. It helps to deal with users access rights’ related issues, in case objects are added to storages and file system automatically grants users access rights to them. With the help of this report, for instance, it’s possible to trace, how exactly users’ access rights to subfolders and files, kept within large directories are distributed. If access rights to some specific objects don’t match with access rights to parental folders, then FileAuditor sends a notification. What’s more, the report enables to see, if there are any excessive access permissions to any resource present. We revealed some issues with access rights inheritage, however, we managed to quickly deal with them and didn’t find any more critical issues.
2. Management of permissions
Of course, even before the audit everything worked smoothly, in other words, access rights were configured appropriately, we didn’t have to start from scratch. The idea was to perform an additional access rights audit to some critical objects and enhance protection of these objects.
I’ll reveal it with the following example. Initially we checked, whether some specific content was kept inappropriately. One of the type of objects we were looking for were questionnaires for customers, which they filled before testing the software. They contained sensitive data on clients, such as configuration of infrastructure, data on employees etc.
In case such data is obtained by users, who aren’t involved in trials – this is a violation of agreements with customer. So, it’s required to make sure that such data is kept only by sales managers and technical support department employees, who help clients during the trial term.
It was required to check, whether such data was present on workstations of any employees, who weren’t involved in sales, as well as in common network folders. We’ve uploaded the questionnaire template, and configured rule basing on the search for similar principle and according to the document format. No violations were detected, however, we decided to play it safe.
What did we do: we had previously configured the rule, prohibiting access to folder with questionnaires’ templates for employees, whose job duties didn’t require with interaction with these documents. Such user rights and permissions can be configured in the AD, however, it can also be done directly in the FileAuditor (I’ve explained how to do this earlier: it’s just required to click on the right button and reconfigure access rights).
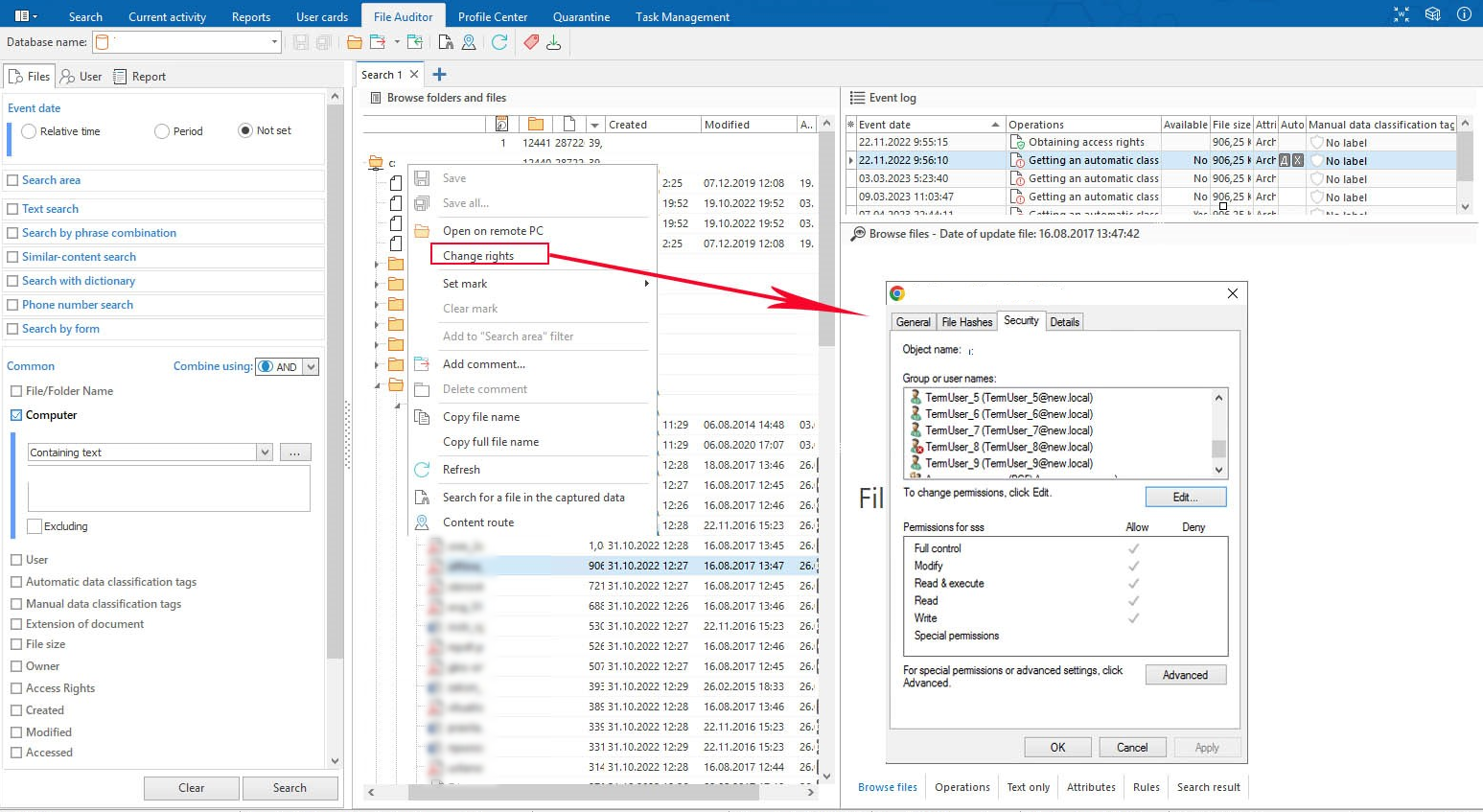 Change of access rights to file
Change of access rights to file
Besides, if it was required to configure the access rights from scratch (for instance, if we created the folder one more time), the report Resource owners could have helped. It enables to control creation of new objects in the file system and redistribute access rights to them. This is how it looks like.
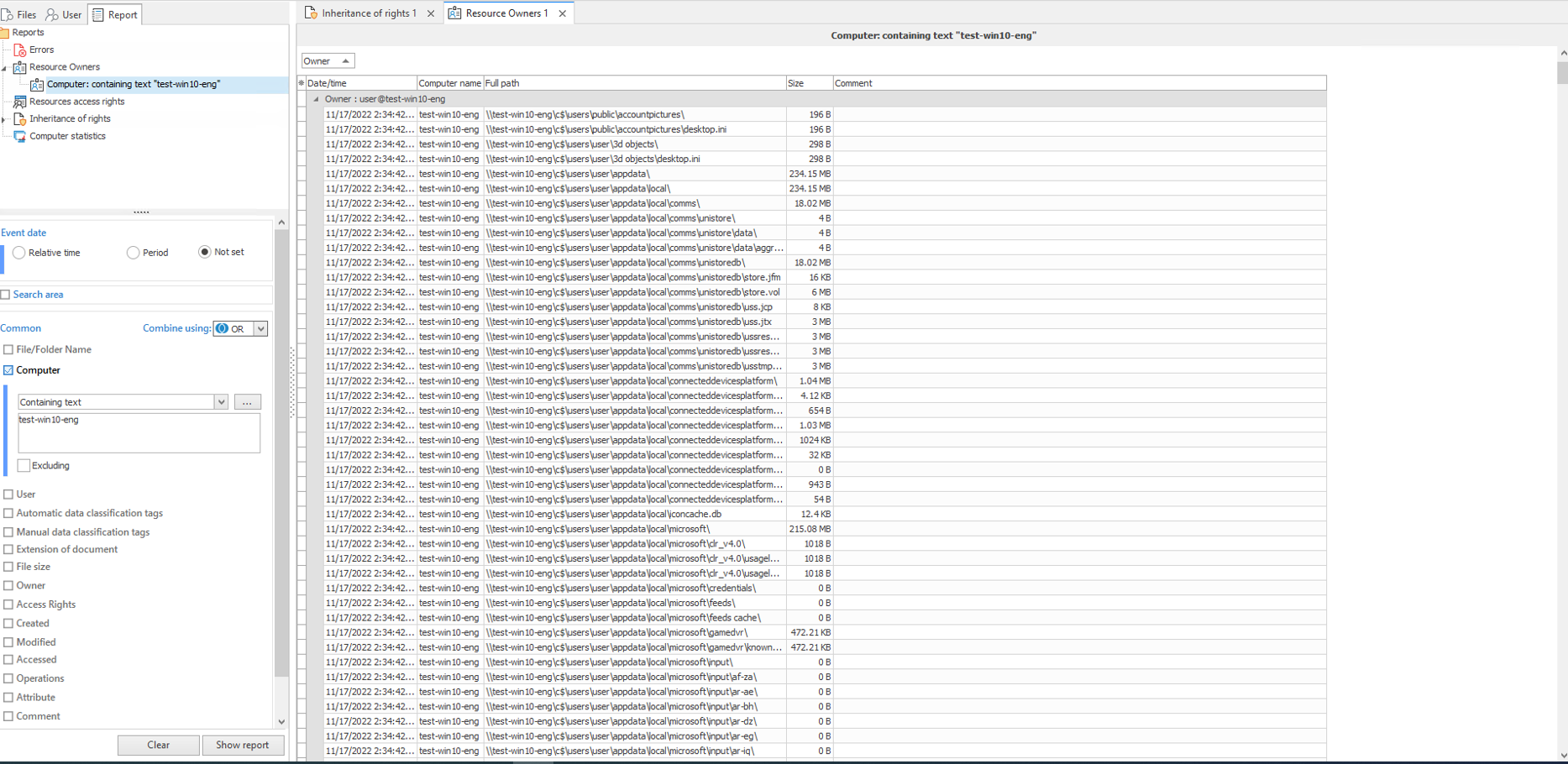 The example of Resource owners report (from test infrastructure)
The example of Resource owners report (from test infrastructure)
We also additionally configured blocking of transmission of Questionnaires via any channels for all users, who didn’t have legitimate access to these documents (only sales managers and technical support engineers had legitimate access to this data).
Blockings in FileAuditor work on the level of processes, which are allowed or prohibited to read documents from file system according to the conditions set.
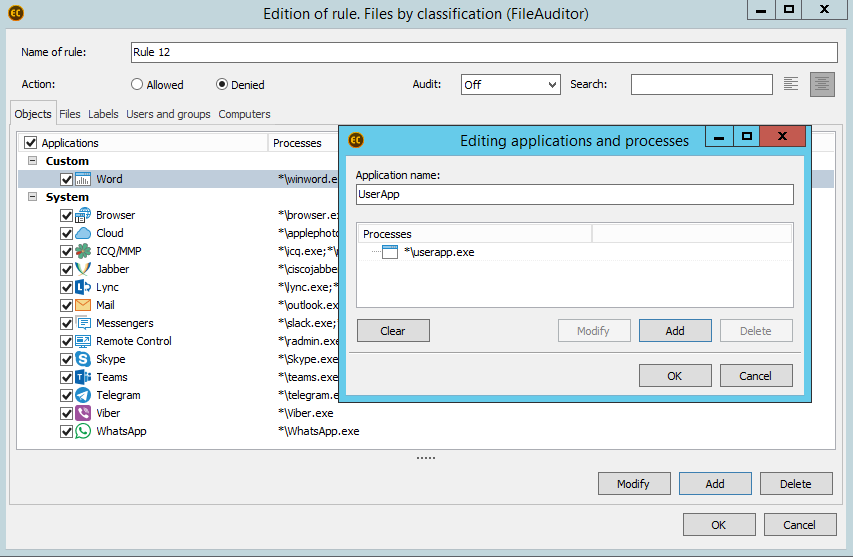 The example of configuration of blockings in FileAuditor
The example of configuration of blockings in FileAuditor
The blocking is implemented the following way: driver, which controls file system, analyzes the classification label, added to the document (in our case the Questionaires label was added) and refers to the FileAuditor to get instructions on how to process the document. In case all the requirements are met, the access to the file labeled is prohibited. The requirements can be specified according to the user, PC, processes and mixed in different combinations. As a result, the system doesn’t have to additionally analyze the file content to take the decision on blocking – the algorithms required are implemented instantly.
In other words, if it’s prohibited for users, who aren’t members of Managers group to read files, containing Questionaires label in MS Outlook, application will block opening of a file for these employees. This also means, that a user won’t be able to add a file in the attachment when sending an email. The restrictions are also implemented for groups of processes: for instance, for all browsers and messengers at once. The FileAuditor is capable of blocking access to a file via any application in no regard to its version, type and origin, it doesn’t matter whether it’s a system process or tailor-made corporate software. Thus, violators, who somehow obtained or received documents, which aren’t intended for them, won’t be able to transmit them anywhere.
An example of activation of access to file blocking
Blockings and manual access rights distribution in the system help to control reading, editing, resending and other unwanted operations on documents, containing confidential data. Focus on the content is the specific attribute of FileAuditor blockings, as traditional DCAP class solutions and other IS tools work principle is based on the examination of files’ attributes or their location, not content.
3. Monitoring of violations
At the final stage it is required to check:
- Who works with files
- What exactly do users do with files
- Whether they attempt to bypass restrictions.
Our employees are acknowledged about the information security rules and don’t violate them, so, for us, it was simply an experiment. Nevertheless, we made some interesting findings.
First of all, we checked the data on operations with most critical files in file activity log. The easiest method was to configure security policies, aimed at control of unwanted operations, which would automatically detect violations and instantly notify IS service. We activated the policy, however, didn’t detect any violations.
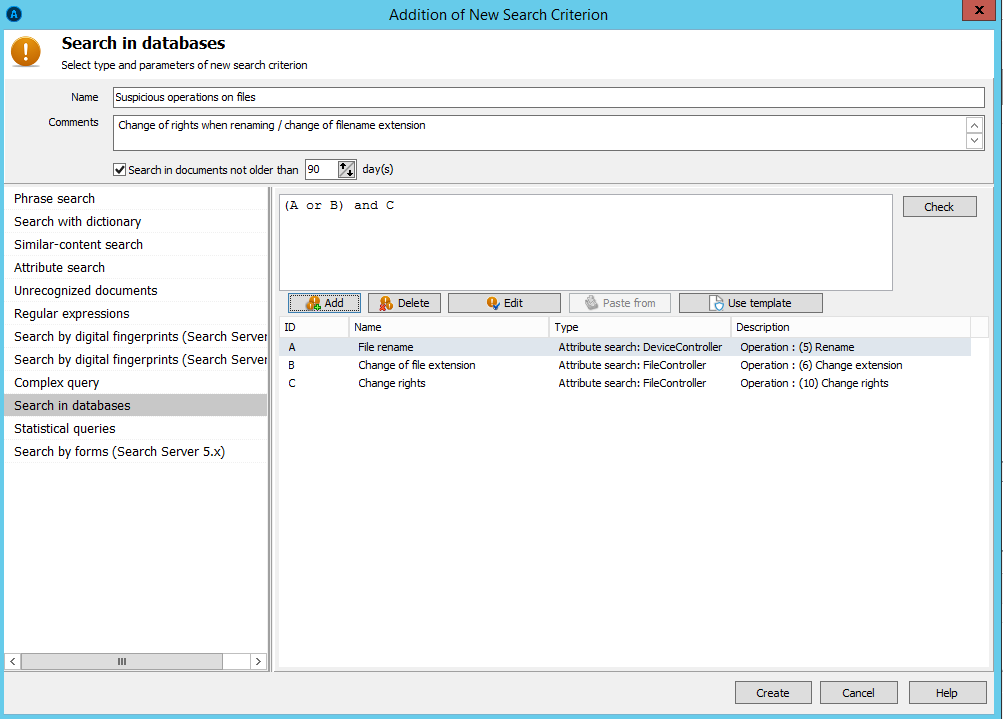
This is how the policy on search of unwanted operations is configured
In order to play it safe, I decided to examine everything precisely. FileAuditor uploads the history of attempts to access the file, containing labels, when the file is viewed it in the main console. Actually, operations are presented the classical way: reading, editing, transmitting etc. Additionally the system detects internal events: if a label is added to the file (in case the file was automatically labelled by the system according to rules set or if it was manually labelled by a user); if the file lost the label (for instance, if a user deleted or changed sensitive content); if it was renamed or deleted; if someone received new permissions for interaction with the file.
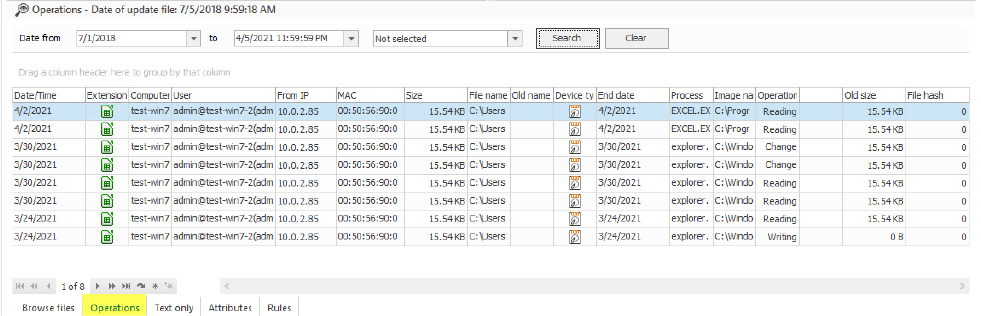
Viewing operations on file
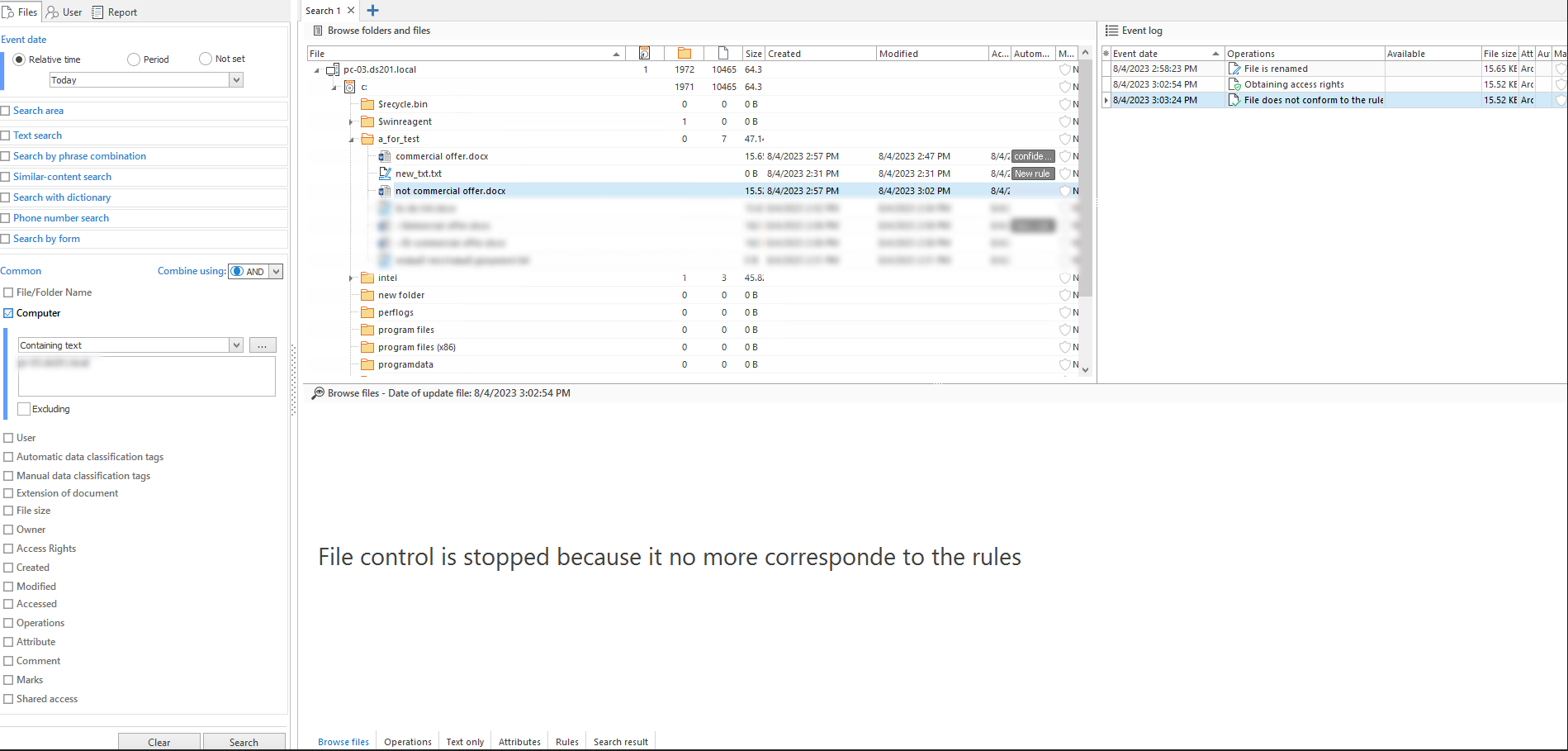
The example of File control is stopped event, when the file label is eliminated
However, the audit didn’t spring a surprise. No one tried to copy or somehow modify files. In fact, this is logical, taking into consideration the preconfigured access rights restrictions.
However, some violations, related to documents transmission were detected. The FileAuditor has the Operations - Access prohibited filter, which helps to deal with this task. It enables to perform an operation, which is in its own way the audit of blockings: it reveals both manual attempts and access attempts with the help of applications to open a file/folder, access to which is blocked for a user.
The following incident was detected: sales manager, who had the legitimate access to a file from the Questionnaires category sent it to the PR department specialist. Logically, PR specialist didn’t manage to open the file, and the solution, in turn, detected the fact of blocking response. It turned out, that the manager planned to share the questionnaire with the technical support engineer, but accidentally sent the email to the incorrect recipient (because that PR department and technical support department employees are namesakes).
What did we do: we reminded the manager about the necessity to be more attentive, as he could have accidentally sent the questionnaire to a third party recipient. The last thing we had to do was to explain the PR department employees what data this document contained and why they couldn’t open it. This case made us ponder that it will be very useful to add a mechanism, which will notify a user about the blockings transparently. Such a mechanism acts as an additional reminder about the corporate security rules and helps users to understand, why they can’t perform some operation. We also decided, that it would be great to provide users with an option to rapidly get in touch with the IS officers to approve operations on the required file. Thus, we’re currently developing the functionality, which will enable users to make access requests via FileAuditor interface, after testing we’ll release it.
A bit of outcomes
The most important one is that audit really perks up. Our experts deal with the intercepted data on an everyday basis and analyze, how employees work with confidential data. Basing on our on-hands experience, I can say, that, basically, up to 90% of violations take place because employees somehow gain access to files, which were kept inappropriately. If you perform the audit, you stay one step ahead of problems. Taking into consideration the capabilities of configuration proactive restrictions and blockings, this is especially useful.
As a result, I can say, that the experiment turned out to be a success. Even basic capabilities of the audit helped us understand, how to enhance the corporate IS policies. Besides, this test helped us to formulate new tasks for the team of developers: we understood, that some options could be realized in a less complicated and more user-friendly manner, besides, the new ideas for useful features originated. Thus, most probably, the experiment will finally be useful not only for us.
If you also wish to check whether everything is put in order in your corporate file system, you may request a free trial of our solution and do the experiment too.

Subscribe to our newsletter and receive a bright and useful tutorial Explaining Information Security in 4 steps!

Subscribe to our newsletter and receive case studies in comics!