Do you consider launching comprehensive monitoring of your internal business processes and even reinvent business continuity management strategy but aren’t sure you want to delve into risk management program and hire extra staff, assign your specialists to the new job and purchase the system to integrate it with your business architecture and implement all the control? If you do – read and learn how to establish a smoothly supervized workflow and not to the detriment of your primary activities.
What is it?
Our information security services are an opportunity to ensure comprehensive protection from external and internal threats with the help of a professional who specializes in risk evaluation, mitigation and regulatory compliance. Our colleague, security analyst, evaluates staff-related business risks, analyzes user activity within a system, and controls productivity implementing employee monitoring software and time tracking software toolset. All these measures help you prevent data leaks, fraud, sabotage and other incidents.
Our services include:
- Installation and configuration of the instruments for controlling of data transfer methods: via communication channels and to external storage devices (DLP);
- Analysis of information captured by the DLP and violation identification
- Shaping detailed incident reports
- Employee monitoring, insider threat and blackmail discovery
- Performance monitoring and project management support
- Internal threat detection, early warning, influencing factors.
How does it work?
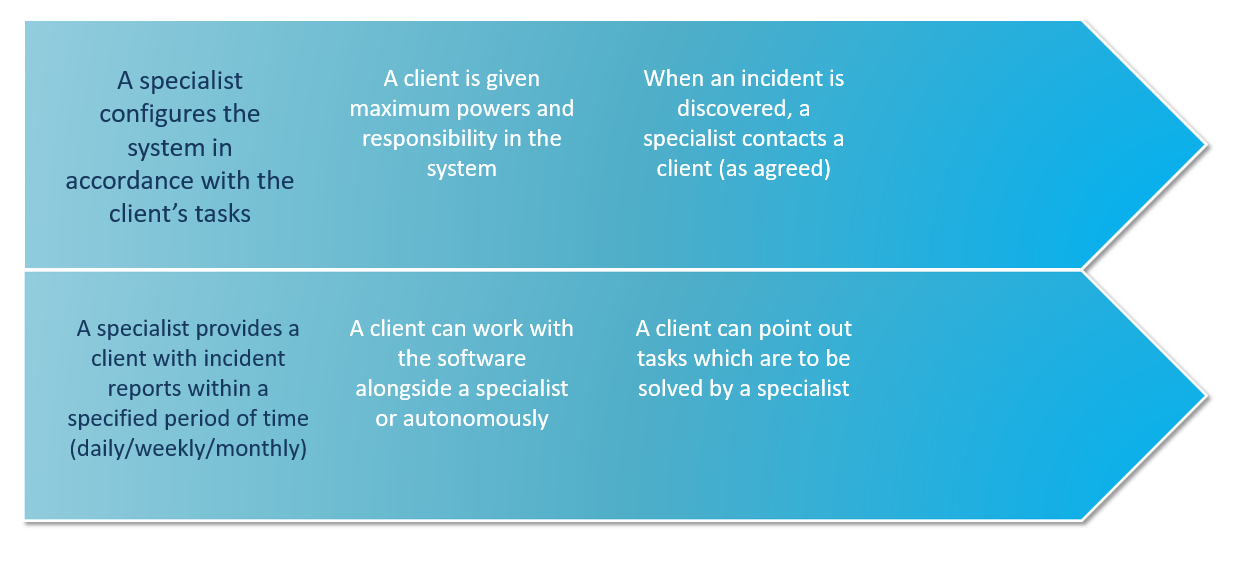
Who needs it?
Any small, medium or large business can apply for the information security service. And for small and mid-size enterprises it is probably the only way to solve information security issue.
How do you benefit from applying to our services?
- A company has no internal threat mitigation tools installed, and no SOC or risk management department in place, but the need to protect data is urgent (50+ PCs, operations on personal data, competitive market – companies might get their trade secrets and customer databases stolen)
- A company has a security department, but it is responsible for physical and financial audit, and data protection remains an issue
- A company has a solution installed but has no staff to implement the risk management program.
One of the advantages of using services is in free trial period. Experiencing our information security services for free will let you assess the skills of our analyst and capabilities of the software as well as to detect weak spots within your company.
Cloud option is also available. No need to install the solution on a company’s server – data from endpoints is received by our server running in the cloud and our specialists work with this information.
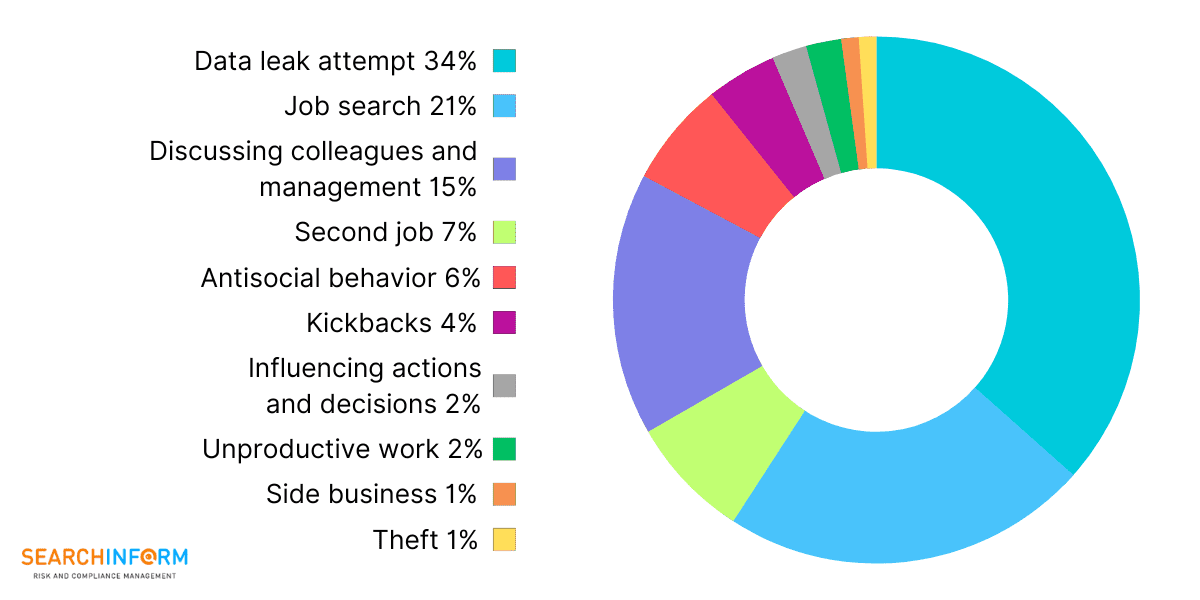
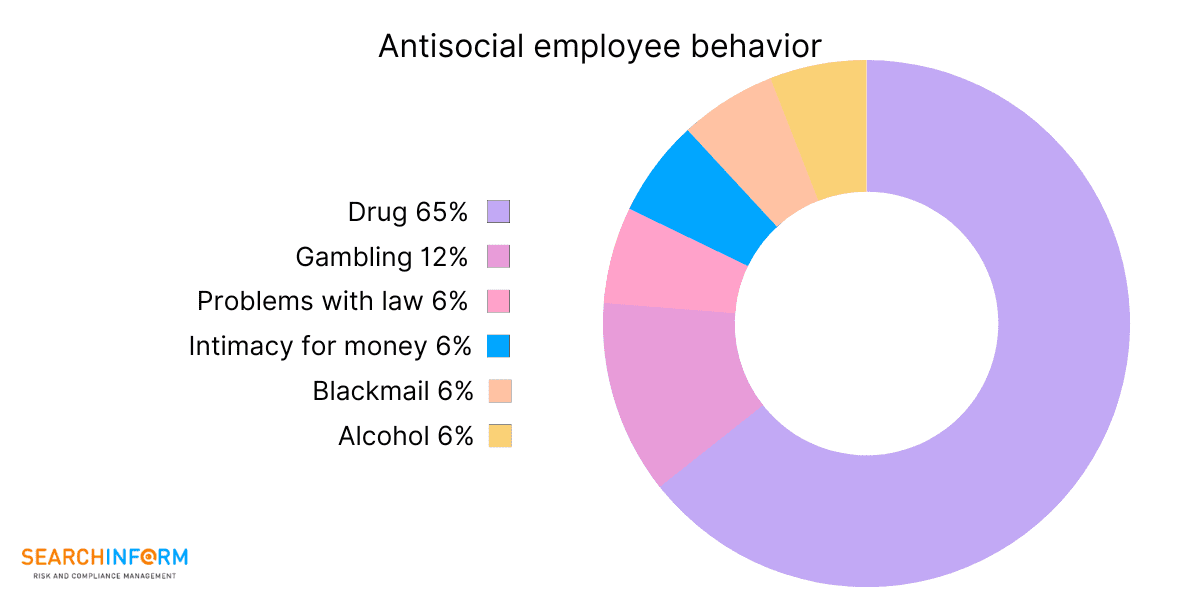
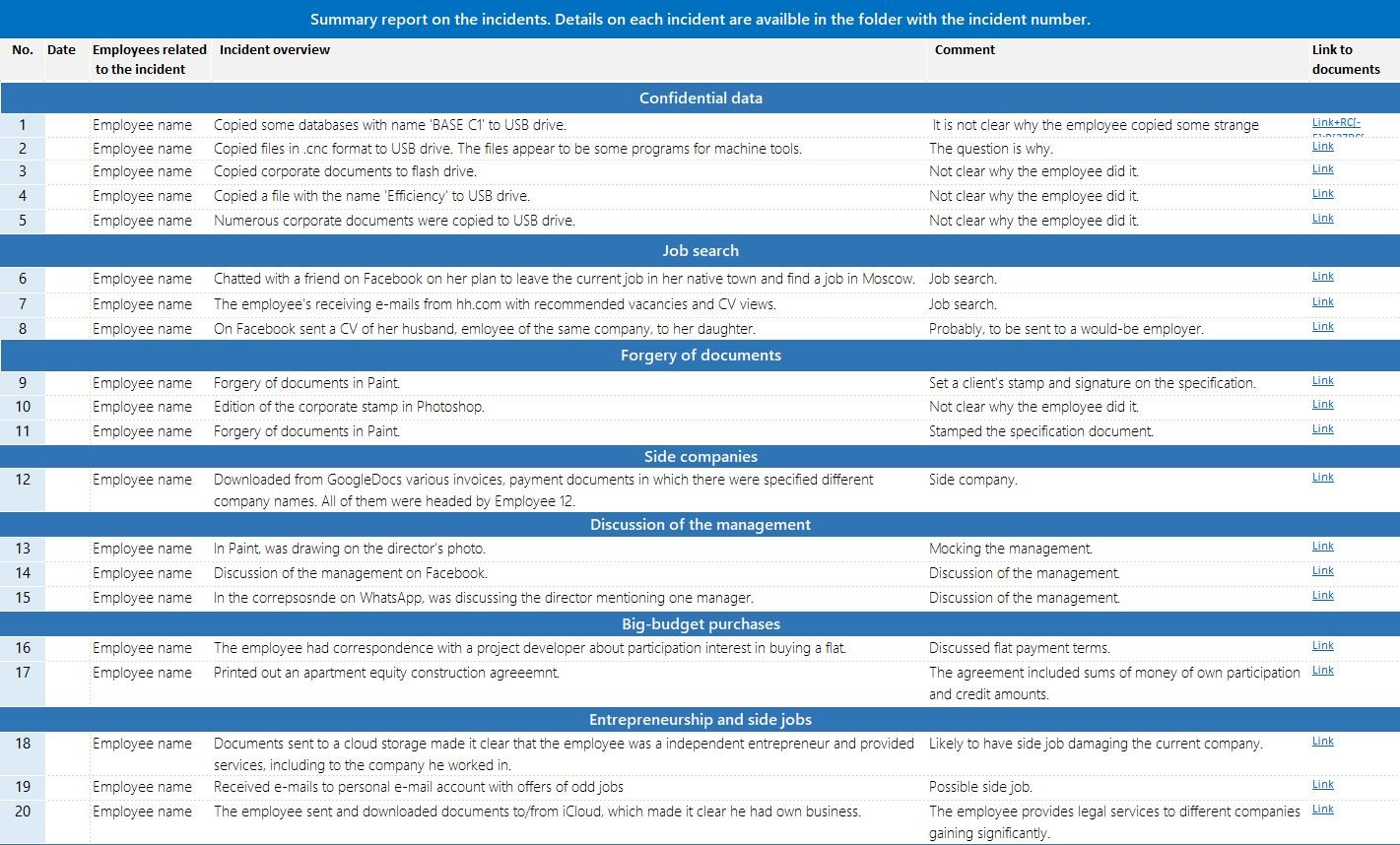
Incidents discovered by our clients during the services trial:
How to launch the process?
1. Prepare your system for the external access.
A specialist has to access a corporate system in order to configure the solution and search for incidents. All specialist’s activities get logged, documents between a contractor and a company (or a third party contractor) is signed – the package includes a non-disclosure agreement. Besides, the information security services provider risk’s its reputation in case a supplier is to blame for a customer database leak.
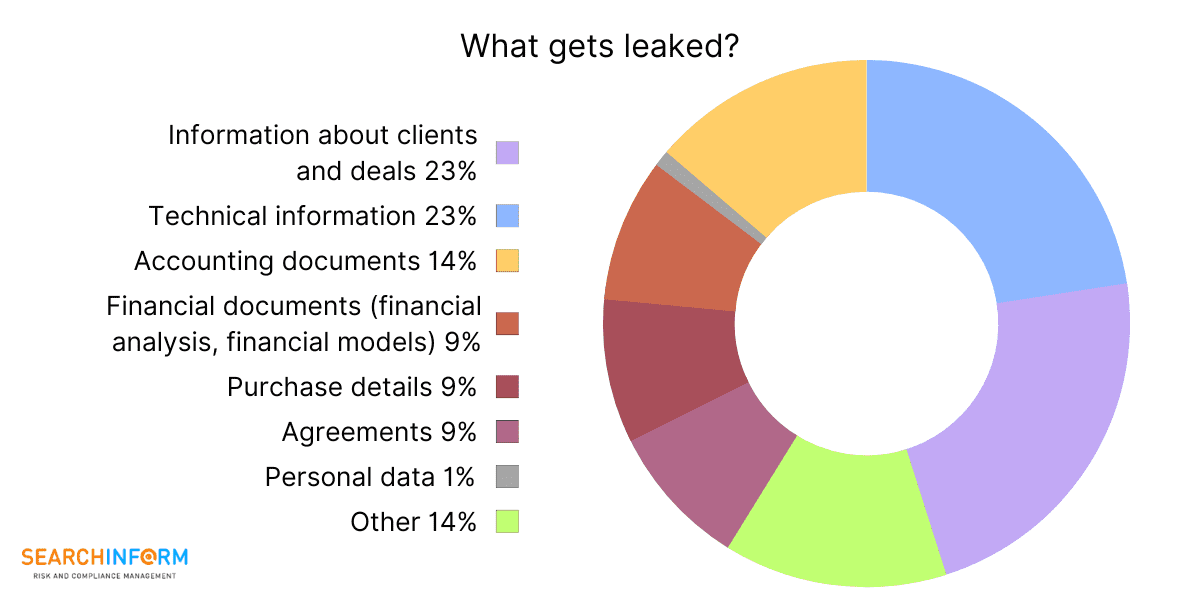
2. Provide the analyst with information about the company
Even for an experienced specialist a client company is a terra incognita. Provide the analysts with details to shorten introduction time and facilitate integration.
What should be given:
- the list of employees whose computers will be monitored by the professionals (to assess user activity adequately, for example, a Deputy CEO can read the accounting documentation, but a supply manager can’t)
- the list of remote employees (managing remote employees is an issue, they should be monitored in the first place, because they have access to corporate data, but are out of sight)
- the list of email domains (to monitor inbound and outbound email)
- email domains of competitors (to monitor communication between colleagues)
- job descriptions (to understand business processes), etc.
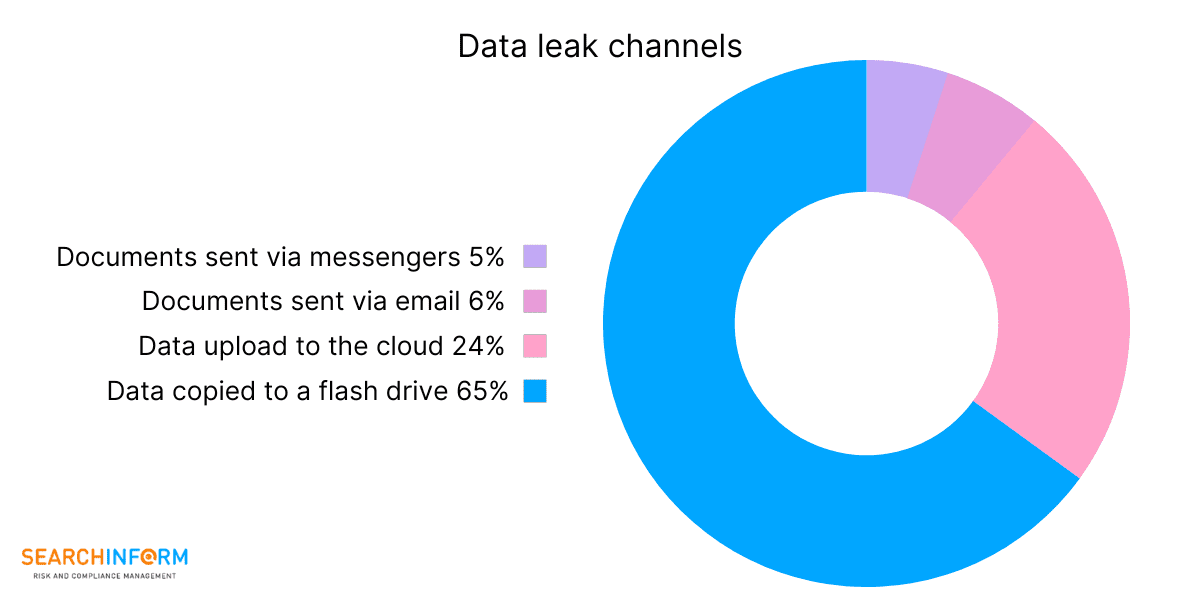
This information is sufficient for detection of typical incidents. Besides, specific tasks are to be set to allow the analyst to have a grasp of an issue and use as much knowledge as it is required. Discuss with the specialist the subtleties in your employees’ work. An honest talk will let you determine which violation should be considered an incident, evaluate the level of criticality and promptly solve the situation.
Case study from our client:
The company relocated its remote employee from an IT department to work in the office. A drop in productivity was observed soon after the staffer’s transfer. The manager asked the head of the department if there was a problem but received no informative response. The internal threat mitigation instruments helped to analyze the employee’s correspondence. It was discovered that a conflict erupted between employees who wouldn’t communicate with each other properly during work hours. The IT specialist was placed to work remotely, and the cooperation improved.
3. Choose a person in charge
An analyst implementing the program for your company will need a curator from your company to cooperate – it can be some employee who will stay in contact with an analyst and make decisions regarding the detected violations. A curator will have a privileged access to the computer monitoring software and can even work with it independently.
The job should be assigned to a responsible and loyal employee who is trustable enough to access the company’s corporate secrets. Ideally, this is a Chief Security Officer or a business owner. The former knows where the company’s weak spots are and can improve the workflow. The latter loses money in case an incident occurs, therefore approaches data security seriously.
In fact, a top manager or an information/financial/physical security officer, or a system administrator usually becomes a curator. But this role can be taken by any authorized representative or loyal assistant of an owner.
If a curator was chosen improperly, the services won’t demonstrate the maximum efficiency. For example, he can slowly react to violations which can hinder the process of an incident prevention. Irresponsible employees can hide the “unnecessary” events from the management attention (discussing of executives, disgruntlement caused by a salary). Insufficient competence or disinterest can lead to negligence regarding detection of violation or identification of a suspicious tendency. As a result, correspondence in a corporate chat becomes a real problem, and a valuable employee goes to a competitor.
Case study from our client:
Eight employees launched a side business and supplied raw materials to their employer on favorable terms. Among violators there appeared to be a Chief Information Security Officer.
The violation was detected by a specialist providing information security service. One of the staffers received an email which listed currently working and former employees as the supplier’s representatives. The employee sent job descriptions, which the violators would use for their side business, in response to the email. Some of the employees were fired, some – fined.
4. Agree on urgent communication and regular reports
Efficiency is important in information security, that’s why it is better to decide where, when and to whom a specialist will send information.
For urgent issues for discussion between a curator and a specialist – and an executive If required – a phone or a messenger should be used.
Besides incident prompt notifications which require quick intervention, a specialist sends a detailed report to a curator. The report described all the incidents (major and minor ones). The reporting frequency and addresses should be discussed in advance. If a company takes under control 100 PCs, the first report can be requested after 7-10 days of the services usage. And if 500 PCs are controlled, the report can be requested once a month. It is enough time for a specialist to collect the needed information in each department and each PC.
SearchInform specialist monthly report
Some evaluate the efficiency of information security services referring to the number of detected incidents, but the quality should be the focus. One thing is to spend half an hour in social media, and the other thing is to accept $* millions bribes for years.
Case study from our client:
A regional manager at an industrial company and her subordinate were accepting bribes during 12 years. The money has increased in value up to tens of millions as the manager closed major deals. Audio recording, enabled by monitoring configuration, helped to detect an incident – the subordinate was discussing the business at the workplace. After all the bargains were examined it was discovered that they earned 10% of the final value. Both were fired.
5. Sort out the incidents
A specialist’s responsibility comprises processes from a solution integration to a detailed incident report. A specialist providing services can point at the most critical violations and recommend measures to take. But decision making is a curator’s and executive’s responsibility.
How to mitigate data breach consequences effectively?
Reports present the actual situation in a company: who is productive, and who only pretends to work, who holds tenders fairly and who accepts bribes. Being in possession of information it is easier to conduct a correct and efficient decision making.
Summary
Information security services are a good option for companies which have no time and no sufficient resources to arrange in-house security. Remember that such an approach requires serious attention from both sides, and it will not take long when our services will give you the best results.
An industrial company applied to the services trial, during which small and large-scale incidents involving 300 out of 360 employees were detected. There were side businesses, early leaving from work and collaboration with competitors among the violations. Apply for a trial period and make sure your company’s policies and risk management program meet the standards.

Subscribe to our newsletter and receive a bright and useful tutorial Explaining Information Security in 4 steps!

Subscribe to our newsletter and receive case studies in comics!