The time has come to find out if July was full with information security incidents. In our traditional digest we've gathered the most memorable incidents. In this digest we’ll reveal: There's the aftermath of the Australian insurer Medibank leak, the investigation of the massive Nickelodeon leak, and even unreliable employees with a craving for Amazon's millions.

Social engineering vs. social issues
What happened: The Saxon State Ministry for Social Affairs and Social Cohesion was suffered a BEC attack.
How it happened: in Saxony more than 800 kilometers of wire fence were installed in 2020 to prevent the spread of African Swine Fever. In February 2023, The Saxon State Ministry for Social Affairs and Social Cohesion received an invoice from a supplier in Lower Saxony for the next pack of 50 kilometres of fence. Malicious actors, who read business correspondence decided to take advantage of the situation and conducted a BEC attack. In early March, fraudsters impersonated the contractor and sent an email to the ministry representatives with a notification on the change of bank details, required for conducting delivery payment. The ministry employees didn’t suspect any deception and transferred € 225,000 to the fraudsters' account.
The state body representative told journalists that the procedure of invoice payment is based on a "four-eye" principle, what means, that approval of two employees is required. And if there are any changes to the data made, officials ask the company for clarification through another channel. The internal investigation to determine why these precautions didn’t work is in progress.
Dangerous abuse of power case
What happened: A Texas law enforcement officer has pleaded guilty for using a proprietary system to identify geolocation of his acquaintances with the help of mobile phone operator’s data.
How it happened: Adrian Pena worked as a deputy marshal for the Uvalde County Sheriff's Office in Uvalde County, Texas, and had access to the Location Based Services (LBS) as part of his job duties since 2014. The service allowed registered law enforcement officers to obtain the subscriber's approximate location by mobile number. LBS was owned by Securus, which purchased geolocation data from mobile network operators with the help of several intermediaries.
To ensure that the system was only used for law enforcement purposes, to submit a request, an authorized officer had to log in with a personal username and password, manually input the subscriber’s number, download the official permission to search for this number and put a tick to confirm that the appropriate file was loaded.
According to the case file, Pena used the LBS service 11 times in 2017 for his own purposes, searching the numbers of his acquaintances, as well as people with whom he had a personal relationship and their spouses. He uploaded arbitrary files to the system 8 times to pass the checks. It might have been an empty file called Blank doc.docx. The deputy marshal made it even worse by lying to investigators and telling that he hadn’t used the system for his own purposes. In June 2023, a year after the indictment, Pena pleaded guilty to illegally obtaining confidential data. He faces up to 10 years in prison.
Hacking with counterfeit
What happened: the victim of a stolen PayPal account was forced to pay $1.2 million to Adidas and the NBA for fraud.
How it happened: In December 2022, PayPal account, belonging to Sarah Luke from Byron Bay, Australia was exploited for making hundreds of fraudulent transactions.
Luke believes, that the prerequisite for the incidents was the data breach that occurred at the Australian insurance company, Medibank, two months earlier. However, the organization denies correlation between the events. Luke suspects that the account was hacked during a massive credential stuffing attack, which impacted about 35,000 PayPal wallets in December of the same year.
When Luke received her first email about counterfeit Adidas products being sold on her behalf, she didn't take it seriously and deleted the email. Unfortunately, it turned out to be true. Both the sportswear manufacturer and the NBA sued the Australian for trademark infringement.
There was probably no trade of counterfeit goods. Intruders may had used Adidas and NBA branding on phishing sites to trick victims and receive payments on the Luke's PayPal. US companies often resort to trademark lawsuits to combat fake websites. The proceedings against Sarah Luke were held in the US without her participation. The court ordered her to pay a $200,000 fine to the NBA and a $1 million fine to Adidas. During six months, Sarah Luke has been trying to drop the charges.
Chinese Zuckerberg
What happened: Chinese police arrested a Beijing university graduate for using illegally obtained information on a website to rate students' appearance.
How it happened: Law enforcement agencies responded to posts, which appeared on the student forum at the Renmin University of China. Users shared screenshots of a platform to rate the attractiveness of students. Basing on the screenshots, the page contained the following data on people, who studied at the university from 2014 to 2020: photo, name, student number, college name and name of student’s hometown.
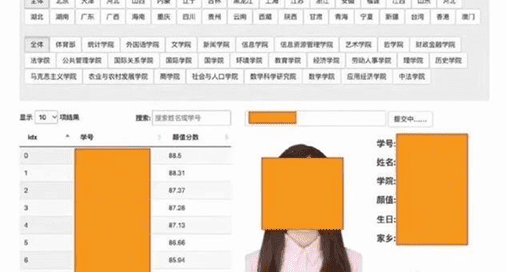
The incident was widely discussed on Weibo social media. Some users compared the site's creator to Mark Zuckerberg. In 2003, while studying at Harvard, he created a website, the forerunner of Facebook, to compare the attractiveness of students' photos.
The university administration responded to the outrageous news by stating that they were concerned about the possible illegal acquisition of student information, and had contacted the police officers. The person arrested on suspicion of data theft turned out to be a 25-year-old graduate of the Renmin University of China named Ma. It’s not clear yet how he obtained the data on students. However, while studying at the university, Ma worked as an assistant in the university's information center and was able to use a privileged account.
Cartoon leak
What happened: Nickelodeon Animation Studios is investigating a major leak of documents and media files.
How it happened: At the end of June, rumors about a data leak from Nickelodeon's animation department began to spread on the Internet. Allegedly, the total volume of files distributed via Discord was up to 500 gigabytes and included unreleased footage, Photoshop documents, scripts and more. Nickelodeon representatives confirmed the authenticity of the data, but told that some documents were ten years old. The leak probably occurred in January 2023 on one of the company's portals. Due to an authentication error, users were able to access the animation department. Nickelodeon closed the breach two months later.
An email with a formula
What happened: Japan accused a Chinese researcher of sending confidential information to a chemical company, based in Beijing.
How it happened: Quan Hengdao had been working as a researcher at AIST National Institute of Advanced Industrial Science and Technology since 2002. According to the investigation, in April 2018, he forwarded an email to the Chinese company, containing data on the synthesis of fluorine compounds. A week after receiving the email, the company applied for a patent in China, which was granted in June 2020. The data in patent resembles information, sent via email. In addition, according to Japanese media reports, the Chinese company, which received the data from Quan Hengdao, has an office in Japan, where the researcher's wife works. Investigators believe that the misuse of the data has affected national interests. The defendant disagrees with the charge and believes that the data didn’t constitute a trade secret.
Fictitious Amazon contractors
What happened: Amazon's warehouse manager and her accomplices stole $9.5 million from the company via shell companies. The fraudsters used the stolen money to buy luxury homes and cars.
How it happened: The fraudulent scheme, which involved seven people, was inspired by Amazon warehouse manager Kayrika Wortham. The employee was responsible for work with contractors and for conducting invoice payments for their services. The essence of the scheme was the withdrawal of money through fictitious companies. Wortham provided her uninvolved subordinates with false data and ordered them to add new contractors into the corporate system and then approved the lists herself. Team members submitted fake invoices to Amazon on behalf of non-existent companies, Wortham approved payments, and the fraudsters received transfers to their accounts. The data (names and social security numbers), required for registering the fictitious contractors was provided to the group leader by two of her colleagues who worked in other Amazon divisions. One of them used data from family members and acquaintances, and the other bought stolen data. The group managed to involve one more manager from another Amazon warehouse, who continued to approve the fake contractors even after Wortham left the company in March 2022.
The earnings Wortham and her partner spent on buying a luxury home, as well as on expanding their car collection with Lamborghini Urus, Dodge Durango, Tesla Model X, Porsche Panamera and Kawasaki ZX636 motorcycle.
Kairika Wortham was sentenced to 16 years in prison and ordered to fully repay Amazon the money stolen. The other members of the group are also awaiting sentencing. Sometimes, company employees’ actions can cause more damage than hackers’ malicious activities.
Clearing the water from the software
What happened: A former technician attempted to uninstall software used to control a water treatment plant in California.
How it happened: the incident happened in mid-January 2021 at a water treatment plant in Discovery Bay, a city of 15,000 people in northern California. Rambler Gallo worked as an instrumentation technician for Veolia North America in Massachusetts, which was contracted to maintain the California plant from July 2016 to the end of 2020. Gallo had full access to the water treatment plant's SCADA system and was responsible for maintaining all instrumentation and programmable controllers. The plant's industrial systems were connected to an internal network that was not directly connected to the internet. However, it was possible to access the network via a contractor's laptop located at the plant. The technician installed the TeamViewer remote access software on this laptop.
Shortly after his dismissal, Gallo connected to a corporate laptop via TeamViewer and sent a command to remove from the internal network a program called Ignition – a tool for integration of all the plant systems, including ones aimed at control of water pressure, filtration and chemical composition of water. The incident was detected a day later, then the access for the former employee was blocked, the deleted software was reinstalled. In June 2023, the employee was charged with a computer crime and may face up to 10 years in prison and a $250,000 fine.
Bengal ID
What happened: A Bangladeshi government website leaked the personal data on 50 million of the country's citizens.
How it happened: A leak on the Bangladesh’s government website was accidentally discovered by security researcher Victor Markopoulos. The expert was searching data for a project and by chance made this observation. He noticed that the URL for the Bangladeshi site contained the register word instead of the required number; when replaced with numbers, it showed records on citizens. The records included person's name, parents' and grandparents' names, national identity card number, names of banks where transactions were made, and even payment amounts.
After discovering the leak, the researcher sent several emails to Bangladeshi authorities, including the government's Computer Incident Response Team (BGD e-GOV CIRT), but received no response. He then shared the story with TechCrunch, without naming the website. The day after the story was published (a week and a half after the initial notification), the Bangladeshi authorities blocked free access to citizens' data, and CIRT said it had "demonstrated its professionalism and expertise by swiftly initiating a thorough investigation into the matter, leaving no stone unturned in pursuit of undertaking the extent and impact of the data breach".

Subscribe to our newsletter and receive a bright and useful tutorial Explaining Information Security in 4 steps!

Subscribe to our newsletter and receive case studies in comics!