Nowadays, the number of both internal and external information security threats is growing steadily. Employees in charge of numerous organizations worldwide tend to understand the necessity to implement a SIEM class solution, which detects security events within the digital infrastructure.
Usually, customers expect a SIEM class system to be capable of:
- Gathering events from different sources
- Analyzing events and revealing incidents
- Notifying employees in charge on incidents occurrence
- Examining incidents to contribute to the process of incident investigation
- Initiating automatic incident response (in case necessary).
Such set of tasks requires SIEM to provide extended functionality. The more advanced the solution is, the more complicated it is to work with the system. This fact often prevents executives to implement a SIEM system – not every company has enough onboard specialists, who can work with the system.
SEARCHINFORM SIEM SYSTEM
Basing on the results of our research, employees in charge of 14% of organization don’t implement a SIEM system due to the potential difficulties, related to system implementation, configuration and customization.
In order to ease the work process with the system for the end user, we, basically, made the SIEM system functionality available out-of-the-box: the system is deployed quickly and is ready to immediately start work upon the installation, thanks to hundreds pre-set cross correlation rules. The basic management and analytics tools are implemented in the form of graphical interfaces, that’s why it’s easy for IS and IT departments’ employees, even if they don’t have relevant experience, to work with the system.
At the same time, convenience doesn’t compromise functionality. SearchInform SIEM in the real life mode detects:
- Hardware failures
- Targeted attacks
- Potentially malicious users’ actions in the corporate infrastructure.
The solution reveals incidents in chains of events (in the events aren’t analyzed altogether, some dangerous individual events may be missed) and is capable of responding to them in case necessary.
UNIVERSAL RULES
SearchInform SIEM includes over 30 connectors with nearly 400 pre-configured correlation rules. They help employees in charge understand what is actually happening in the infrastructure. As early as at the deployment stage, the pre-configured rules help the SIEM administrator detect layers of IT infrastructure with the events that require response. On the tab with rules, the administrator can analyze whether an event is actually an incident. What’s more, SearchInform SIEM gathers statistics on the incidents, thus, the SIEM administrator will not miss increase in the number of incidents.
The basic connectors in SearchInform SIEM enable to control maximum amount of data sources in the company’s IT-infrastructure. The most critical are the following ones:
- Active Directory
- DBMS
- Email servers
- Syslogs etc.
For instance, thanks to the control of Active Directory SearchInform SIEM reveals attempts to hack accounts or guess passwords, which employees may use simultaneously on different PCs. If the number of pre-set connectors isn’t sufficient, the solution provides Custom Connector which enables IS officer to fine-tune the solution and connect additional devices.
CONFIGURATION OF CROSS CORRELATION RULES
SIEM-systems process millions of events from different sources everyday. According to statistics, a team of 100 employees can generate more than 3000 Active Directory events on an everyday basis, and one operating in the basic mode VMware can generate up to 4 million events everyday. To detect only significant incidents in the entire event flow, the cross-correlation is embedded into SIEM class solutions. Cross-correlation is aimed at collation of security events from different sources, which together indicate a threat. Usually, creation of a cross-correlation rule demands some programming skills. However, in SearchInform SIEM this process was simplified. With the help of embedded graphical interface it’s possible to create rules which will reveal incidents basing on the analysis of a chain of events, gathered from different sources. Additionally, these rules specify parameters, according to which the system considers event as an incident, what significantly reduces amount of false-positives.
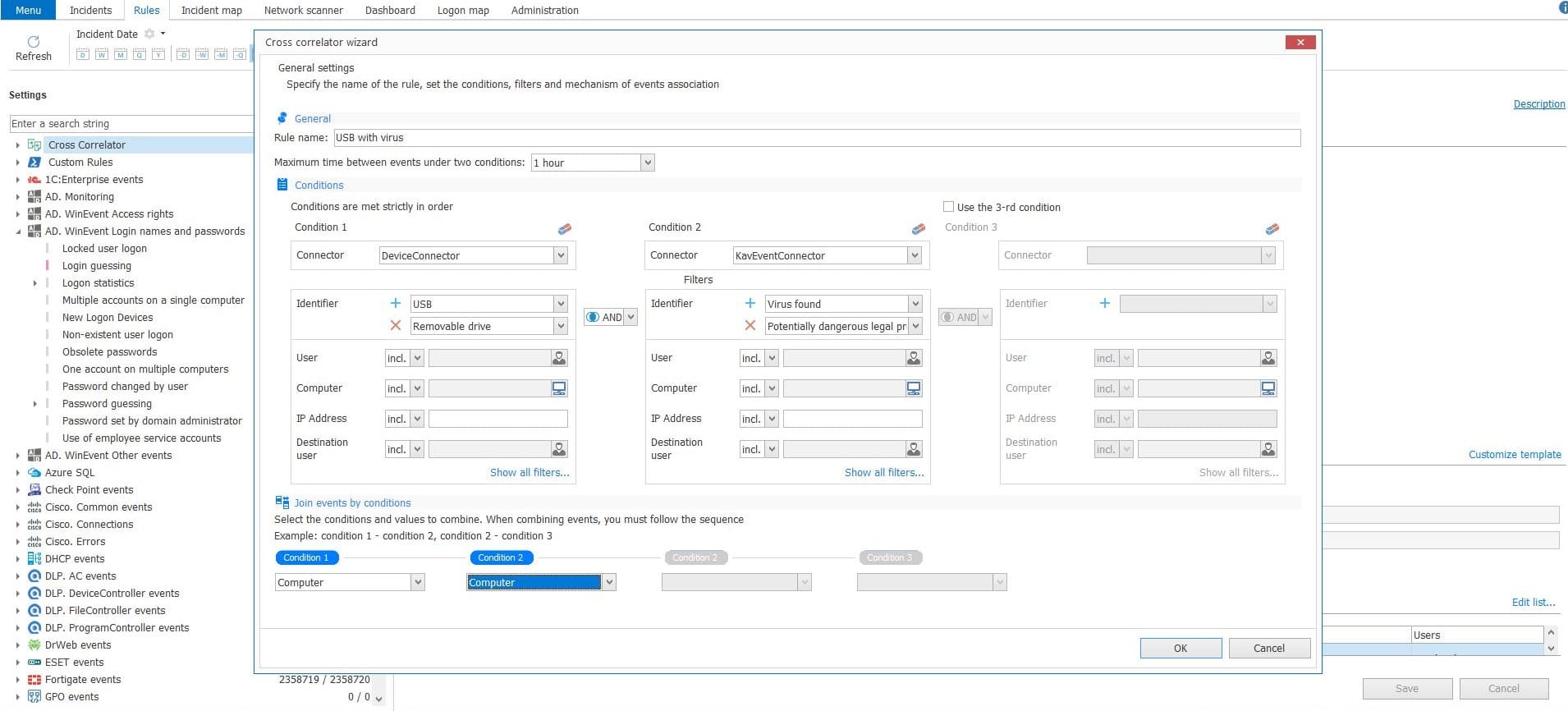 Graphical interface of cross-correlation rules configuration
Graphical interface of cross-correlation rules configuration
INVESTIGATIONS AND REPORTING
SearchInform SIEM has the embedded task-manager, which is useful for conducting incidents investigations, responding to incidents and preventing them. What’s more, it enables to perform investigations without necessity to use third-party tools, such as Jira, CRM or Confluence. Task Manager enables to trace the incident’s lifecycle, include a few events into one single investigation, appoint responsible employees in charge from the IS-department, assign investigation progress statuses, add comments and sum up everything. Basing on the results of investigations an IS officer can create new cross-correlation rules.
VISUALIZATION OF INCIDENTS
In order to understand the potential damage an incident may cause, it’s crucial to have the full picture of what is actually happening within the infrastructure. In order to deal with this task, SearchInform SIEM offers the Map of Incidents Tab, which interprets network structure, PC and users in connection to servers with installed SIEM connectors. The map enables SIEM system administrator to reveal all the incidents, which happened, for instance, after the account or PC compromise.
The Incident Map Tab
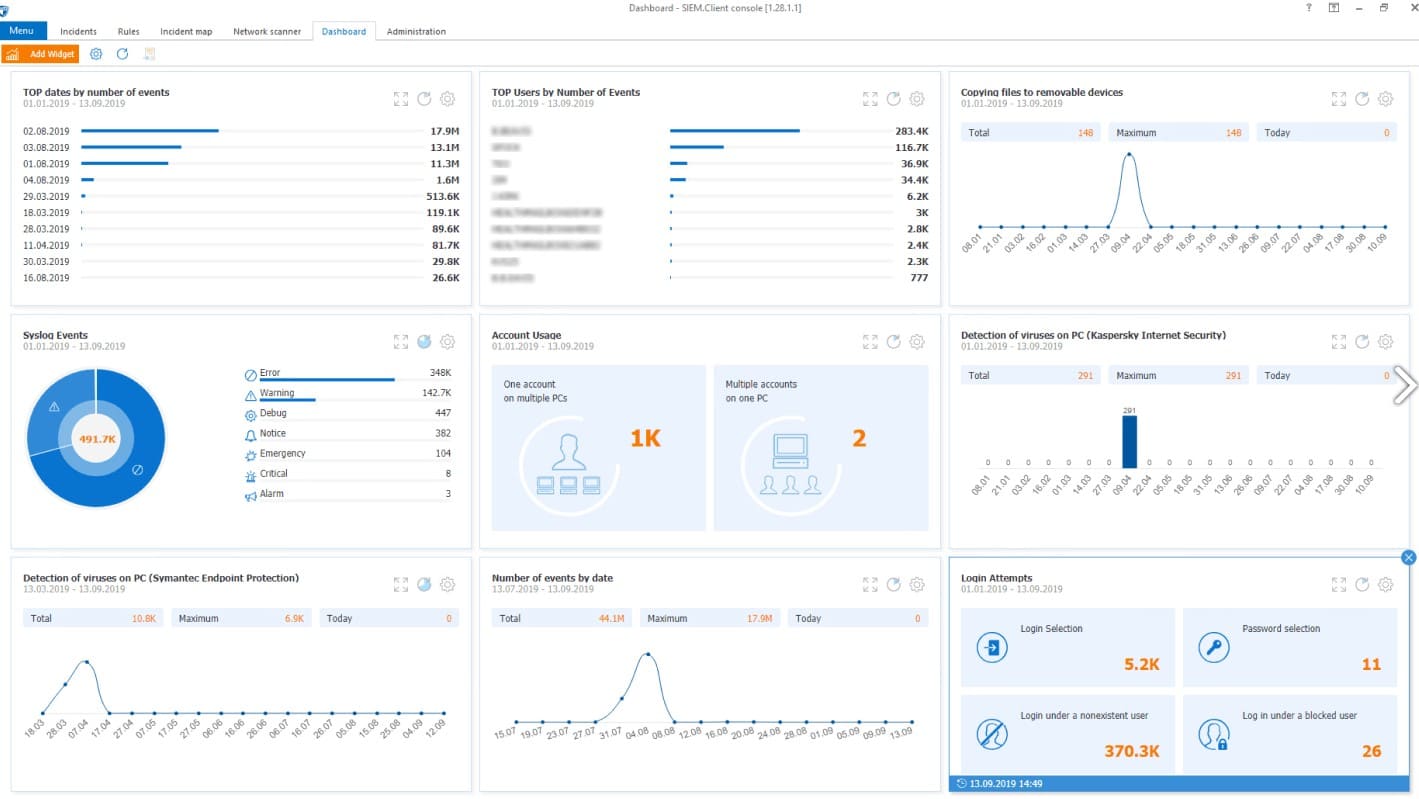
Another tool for analysis of collected data is dashboard with widgets. It shows the most valuable information: incidents statistics, events traffic according to connectors or users, list of rules for the most critical connectors, etc. The SIEM system administrator can configure each widget according to his/her own needs. The visual representation is useful for optimization of IT and IS-department employees’ cross-department collaboration.
SEARCH FOR THREATS AND AUTOMATIC RESPONSE TO INCIDENTS
In order to implement the full-scale protection of the corporate perimeter, it’s crucial for IT and IS department employees not to overlook potential software and hardware vulnerabilities. The network scanner was implemented with this aim – it helps to detect, for instance, open ports or illicit connection of new devices. The IS officer can configure the frequency at which the SIEM will perform the full-scale infrastructure inventory.
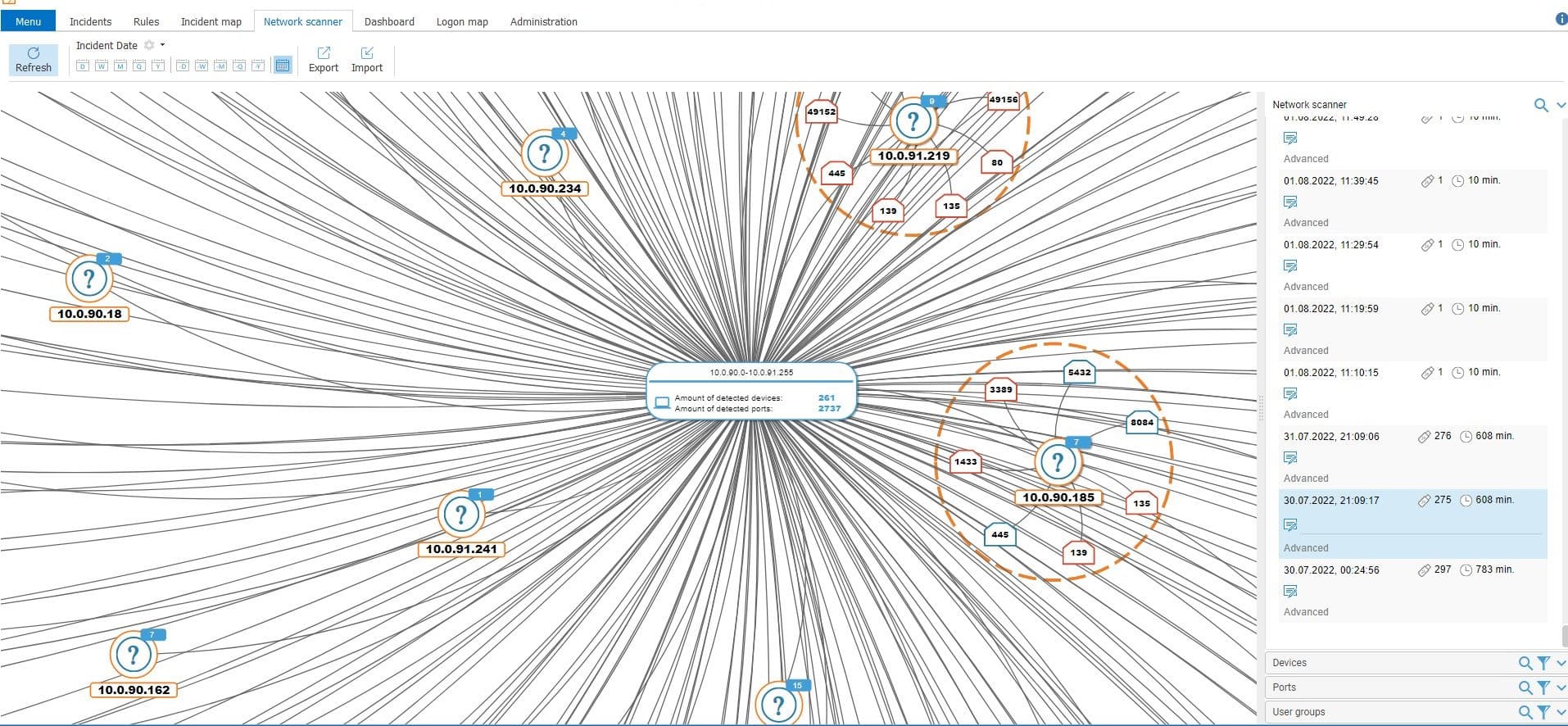
SearchInform SIEM network scanner
The SearchInform SIEM is capable not only of threat detection, but can also eliminate them. In 2023 we’ve added functionality, which isn’t typical for this class of solutions: automatic response to incidents. With the help of the editor, which is now built in the solution’s interface, information security expert can write any script that the SIEM system will run to mitigate the threat. For instance, if file encryption is activated on some detached PC, the SearchInform SIEM can activate a script, which contains the anti-virus response: scanning, deleting files or adding malicious software to a sandbox.
SearchInform SIEM is a solution which goes beyond the usual framework of this class systems. The software functionality, on the one hand, automatizes maximum number of processes and doesn’t demand user to have some specific skills, on the other hand, it provides a variety of flexible settings for monitoring and incident response. Basically, SearchInform SIEM fits in customers’ requirements and helps those, who fear that such a solution will require too much resources for configuration and exploitation.

Subscribe to our newsletter and receive a bright and useful tutorial Explaining Information Security in 4 steps!

Subscribe to our newsletter and receive case studies in comics!