This was revealed by the survey conducted by SearchInform and NEXTA ÇÖZÜM.
SearchInform, the leading global risk management product developer, together with its partner NEXTA ÇÖZÜM, IT consultant and distributor, surveyed representatives of 100 Turkish leading companies to find out how their experts ensure data leaks protection, whether they are planning to increase data security budgets and what data channels their security officers consider the riskiest.
CIOs and CISOs, who took part in the survey, believe that data transmission via USB devices is the riskiest channel in terms of data leaks. Nearly 80% of experts believe that this channel should be controlled first. Other data channels which CIOs and CISOs consider the most unsafe ones are email and messengers. Employees tend to leak data most often via these channels, both accidentally and with a malicious intent.
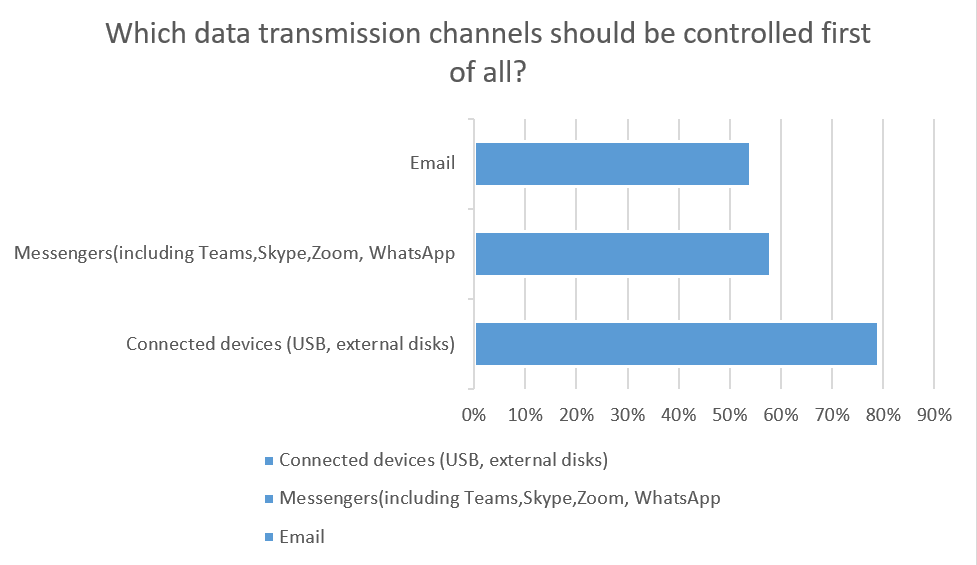
*some experts chose more than one option
Elena Varol, SearchInform Regional Manager, Turkey: “The results of the survey reveal that the traditional channels are still among the most unsafe ones. Employees often send emails to incorrect recipients or use messengers to share confidential data in violation of the established information security rules. Intruders, in their turn, also often try not to invent some new techniques, but leak data via flash drives or send it via email. According to our customers’ experience, internal actors attempted to leak data via external devices in 56% of all cases, and email was used for data leak attempts in 21% of cases. The good news is that modern data protection solutions (DLP systems) are capable of controlling all these channels and preventing data leaks. Advanced solutions are capable of preventing data leaks via new messengers, such as Telegram, which popularity is increasing steadily.”
The bad news is that there is a lack of special-purpose protective software. Thus, many companies fail to protect trade secrets, as well as personal data of customers and employees. This, in turn, means that these organizations fail to comply with the KVKK requirements.
Overall, it is required to invest into information security. However, respondents of only 20% of organizations reported an expected increase of budget allocated to information security next year.
Elena Varol, SearchInform Regional Manager, Turkey: “The will to save money is understandable. However, taking into consideration the current information security landscape and the fact that there is a step change in the amount of information security risks that organizations face worldwide, it makes sense to carefully plan the budget allocated for enhancing corporate data security. Information has already turned into one of the most valuable assets for any organization, and investments into its security will pay off. There is a beneficial option, especially for SMEs, to consider the new approach to data protection: instead of purchasing protective software, it may be useful to implement multifunctional modern solutions, which are available on the service model, don’t demand many resources and are deployed in the cloud. This way, companies can spend their budgets more thoughtfully, save resources and ensure protection at the same time.”
Nexta Çözüm Danışmanlık A. Ş. has more than 20 years’ experience in the IT market, developing and implementing complex IT solutions for different industries. Nexta provides consultancy, assessment and research, project management and full technical support for its customers. Deep knowledge of the local IT market and understanding of customer’s needs put Nexta on the leading position and ensure the best quality of its services and full functioning of deployed solutions.
SearchInform is one of the leading risk management product developers. For over a decade, the company has been a technological trailblazer focusing on contemporary cybersecurity threats, protecting business and government institutions against data theft, harmful human behavior, compliance breaches and incomplete audit. More than 4000 companies across all major economic domains, from banking and retail to machinery and fighter jet manufacturers, count on SearchInform regarding efficient holistic risk management solution defending against ever-improving threats and allowing you to avoid ominous consequences.
You can use SearchInform products to provide comprehensive protection against insider threats at all levels of corporate information systems. Follow the link to get a trial period, it's free for the first 30 days.
SearchInform uses four types of cookies as described below. You can decide which categories of cookies you wish to accept to improve your experience on our website. To learn more about the cookies we use on our site, please read our Cookie Policy.
Necessary Cookies
Always active. These cookies are essential to our website working effectively.
Cookies does not collect personal information. You can disable the cookie files
record
on the Internet Settings tab in your browser.
Functional Cookies
These cookies allow SearchInform to provide enhanced functionality and personalization, such as remembering the language you choose to interact with the website.
Performance Cookies
These cookies enable SearchInform to understand what information is the most valuable to you, so we can improve our services and website.
Third-party Cookies
These cookies are created by other resources to allow our website to embed content from other websites, for example, images, ads, and text.
Please enable Functional Cookies
You have disabled the Functional Cookies.
To complete the form and get in touch with us, you need to enable Functional Cookies.
Otherwise the form cannot be sent to us.

Subscribe to our newsletter and receive a bright and useful tutorial Explaining Information Security in 4 steps!

Subscribe to our newsletter and receive case studies in comics!