EndpointСontroller
Shadow copying from USB
The updated version of the product enables the audit of all files stored on a USB device connected to a PC. The system makes shadow copies of files and checks them against all security policies. Such an approach permits the more accurate identification of risk groups of employees. For example, you can find out about radical views of employees, their addictions or unreasonable storing of company’s secrets on a personal flash drive.
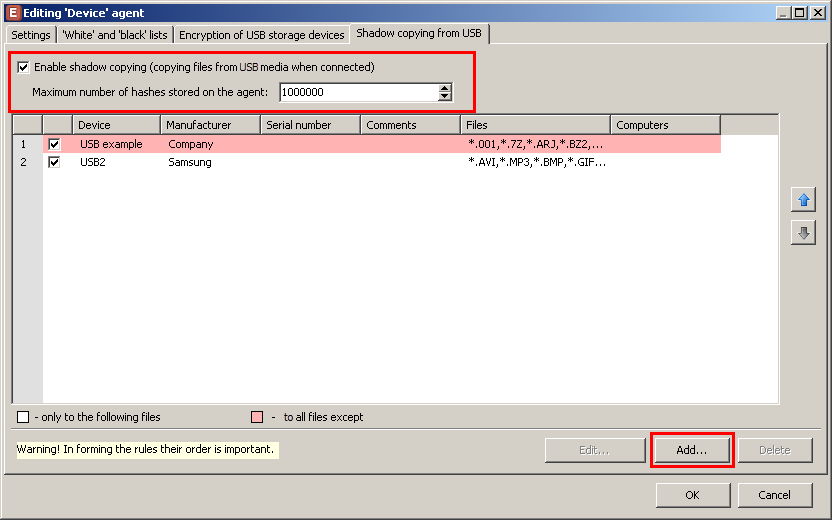
Set up of access/blocking of tokens
It was difficult to detect the connection of a token to a PC before: the system could identify a device as a USB or smart-card. Aa a result, you had to combine several security rules for different device types in order to allow or block a device. Now, the system accurately detects the connection of tokens and allows managing access to them with a single rule. The system has become more flexible.
New device types in DeviceAudit
The enhanced system can not only detect the connection of a phone to a computer but can also detect the device: Android, Apple iOS, BlackBerry Palm and Windows Phone. It permits information security departments to apply more flexible security settings. For example, they can grant access to corporate Apple devices with inbuilt security system but block personal Android devices of employees who can pose threat.
Interception of passwords by Keylogger
The Keylogger agent settings feature the capability to disable interception of passwords that users enter in the authorization system windows. By default, the interception is on.
ReportСenter
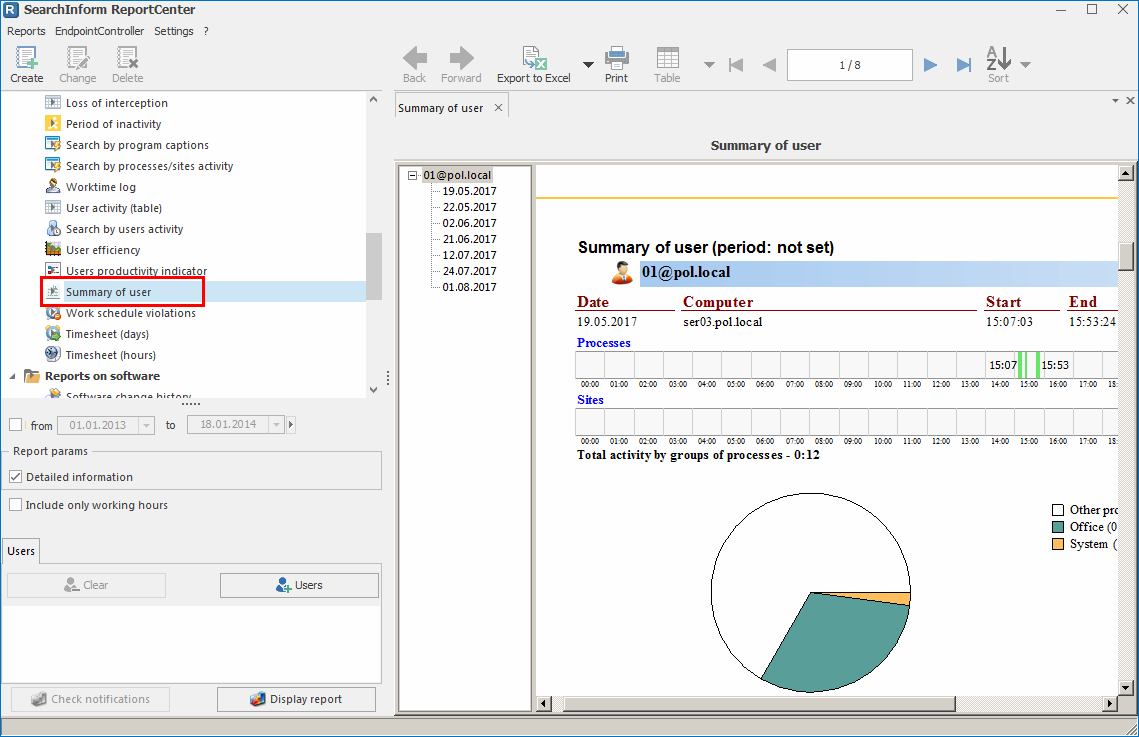
Summary of user report
A new report Summary of user displays information about processes/sites launched/visited by a user during each 24 hours, as well as time spent in/on them. You can optionally view a table with detailed information about the sequence of launched processes and visited sites during the day, as well as the duration of activity in/on each of them.
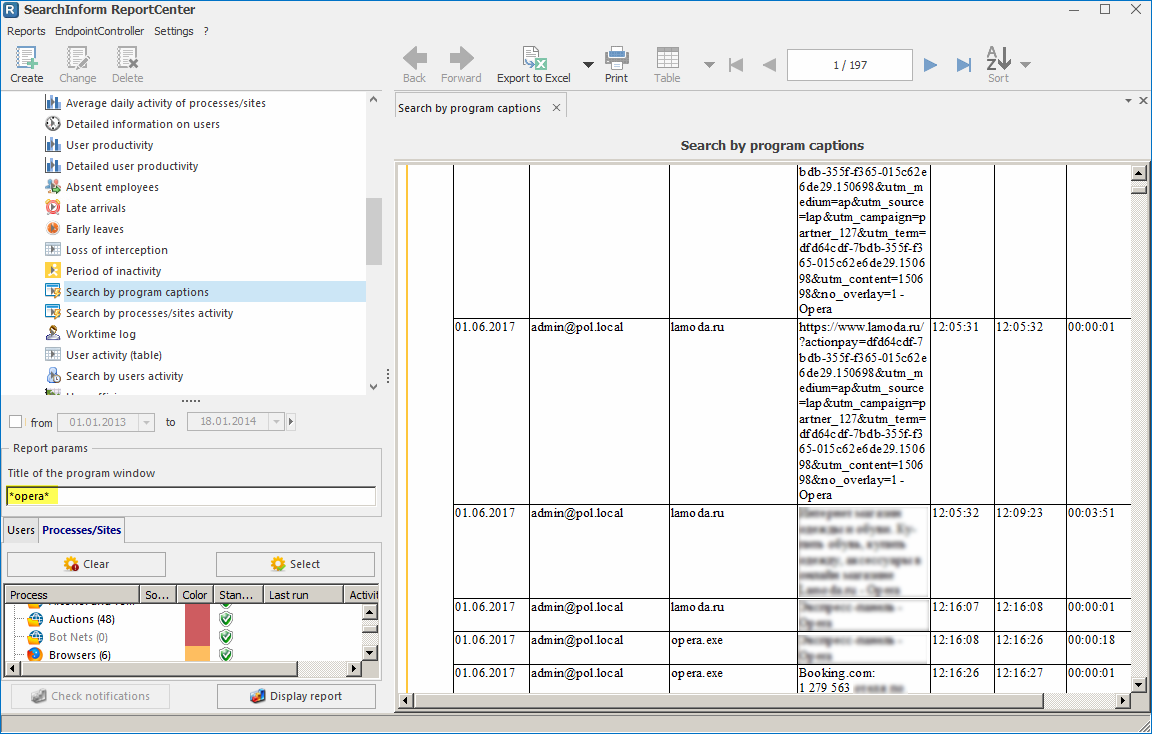
Search by program titles report
Starting Microsoft Word, a user works with a particular document. By the title of this process, SearchInform DLP tracks activity of a user and duration of activity. Data in the report can be limited by a time period, specified users, as well as a list of processes/sites with the specified title.
AlertCenter
Detection of similar email addresses
The feature is used when creating policies to detect sending of files to the personal email or email of competitors. Incidents on the match of internal corporate email are not generated. For example, an email was sent from [email protected] to several email addresses among which there is [email protected]. So, an incident will be generated on the match of “ivanov” in the address of sender and recipient.
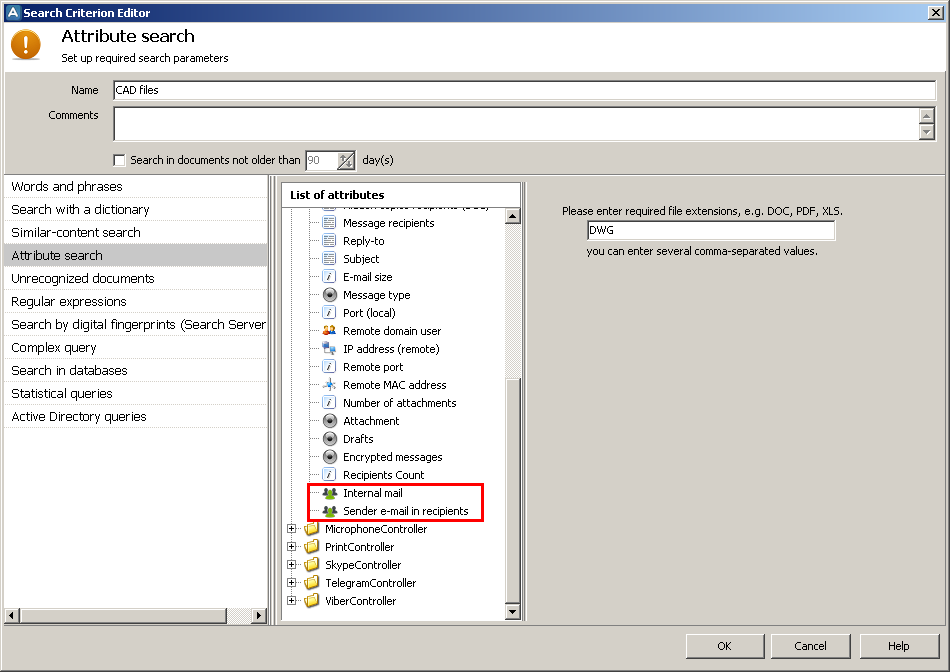
Batch configuration of policies
After the update, the process of configuration of security policies became even simpler. Now, you can configure, reconfigure and disable parameters (check schedule, recipients of notifications and used lists of notification) centrally for all policies and search criteria.

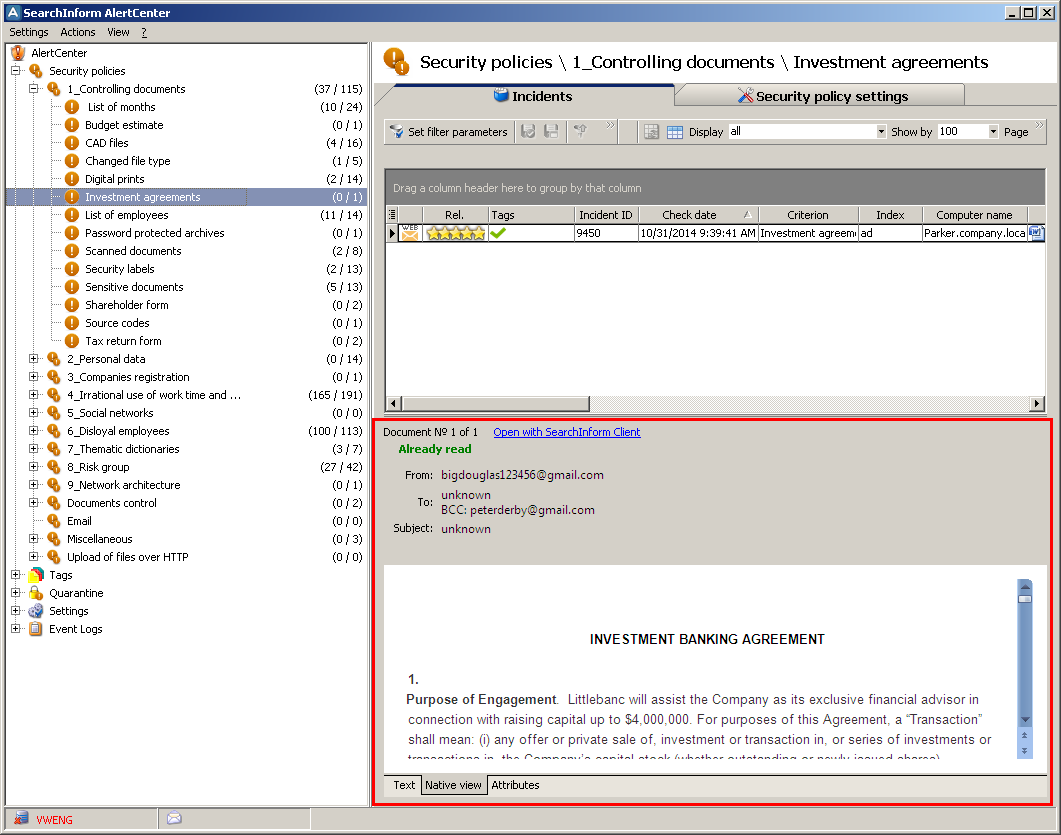
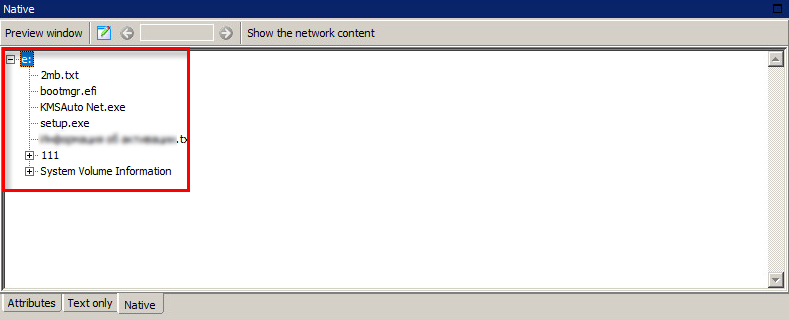
Native view
A new view mode of incidents allows seeing details in the native format of the source document (tables, background, font, highlight and other elements are displayed). When a SearchInform DLP administrator has several different alerts on one incident, native mode allows switching to the source document and clarifying details.
DataCenter
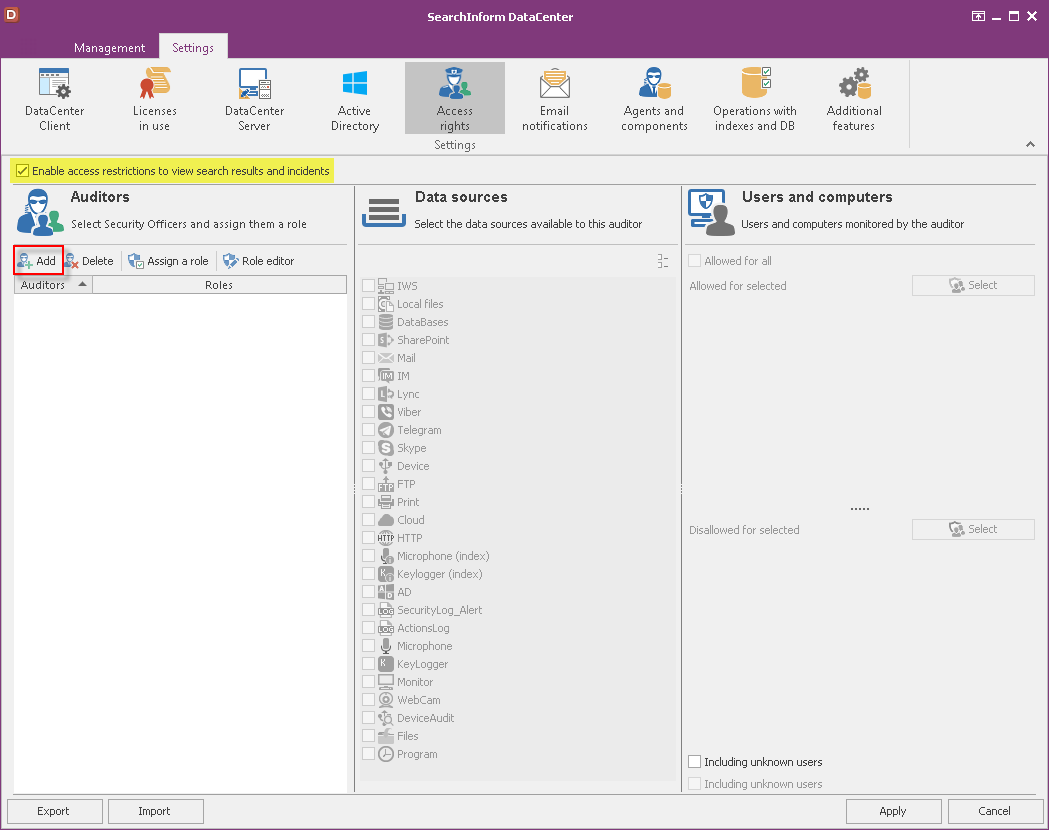
Management of access rights
Before the update, the system was distributing rights by users. Now, the solution employs a different model: a unique role with preset access rights is created after which it is assigned to particular uses. By default, the system has preset roles Admin (full access), Viewer (only viewing). Each new security auditor is assigned the Viewer role that can be changed if necessary. You can select a few roles.
SearchInform Client
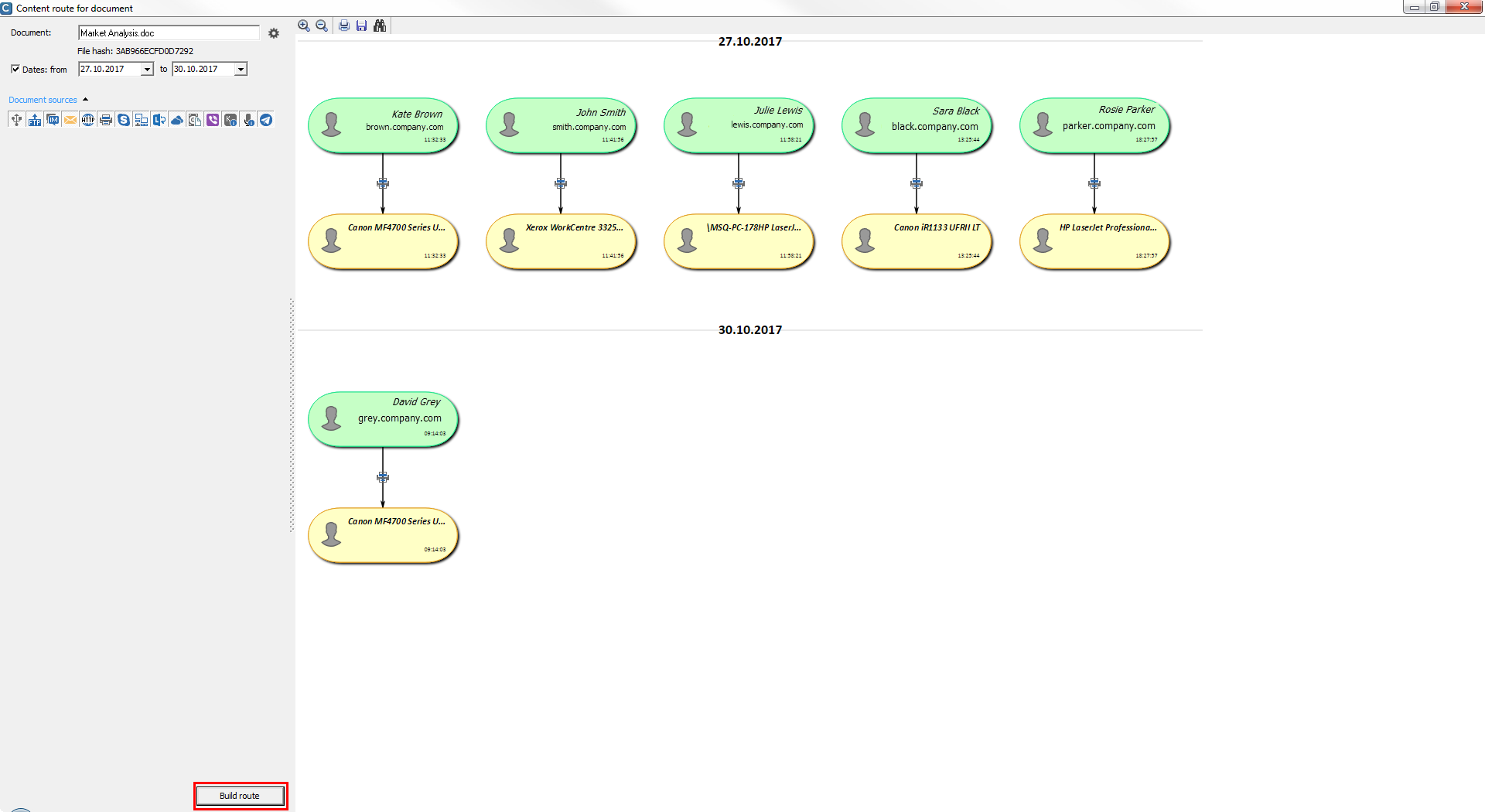
Content route of documents
There was added a feature of building a content route for data that has FileHash attribute (supported only in SearchServer 4.*). The system provides a clear picture of transmission of documents, identifies sender and recipient, as well communication channels used to transmit data. The feature levels up the investigation process and allows the IS department to quickly track dissemination of information.
File system structure
To simplify the operation, the system displays file system structure for data received with the help of shadow copying from USB.
Search Server
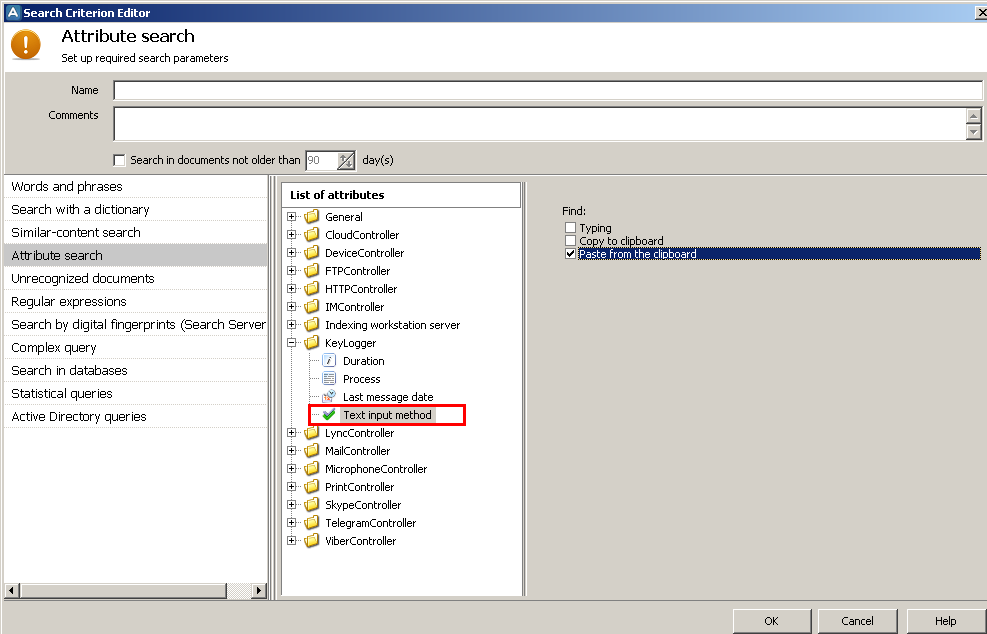
New KeyLogger attribute
The Text input method attribute allows searching in the contents of the clipboard by criteria: typing, copying to the clipboard or pasting from the clipboard.

Subscribe to our newsletter and receive a bright and useful tutorial Explaining Information Security in 4 steps!

Subscribe to our newsletter and receive case studies in comics!