SearchInform has released the update for the DLP system. From now on, the system detects potentially dangerous emails in the staffs’ mailboxes. Thanks to this data information security specialist can mitigate the risk of downloading malicious attachments, clicking on phishing links or getting in touch with fraudsters by a user. The data, retrieved from the DLP system can be used for spam-filters settings optimization on a corporate mail service. Thus, the risks of work station compromise and accidental data leaks occurrence are reduced significantly.
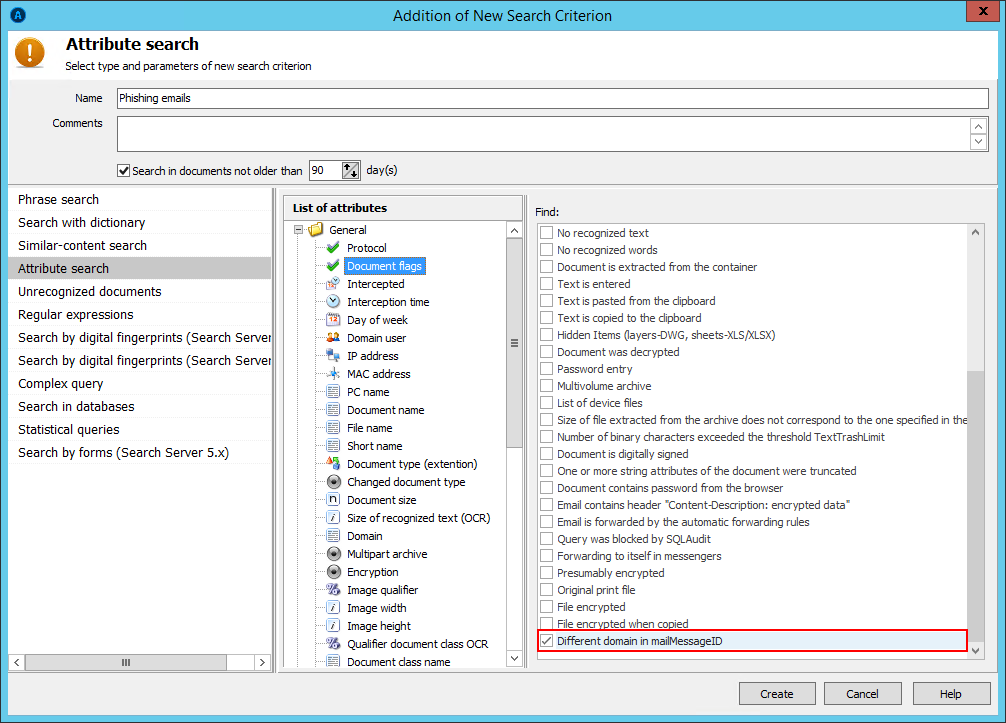
Phishing emails recognition function works on the principle of comparing MessageID and Sender (From) attributes, so, the system detects cases when the domain and the sender’s real address differ. In case these parameters are not the same, the DLP system marks the letter as a phishing one and notifies an information security officer. Detection of such letters may be set in the “search for attributes” section.
“Social engineering methods remain the main cybercriminals’ tool, and the main remaining channel is still email. According to the survey data, more than 30% of employees open phishing emails. Such emails may have links or attachments, containing programs of remote administration, encryption virus and other malware soft. In order to exclude this threat, our DLP system notifies information security specialist in advance, that an employee has received a phishing email .” – said Alexey Parfentiev, the leading analyst at SearchInform.
Phishing detection is an additional tool for control over atypical risks, including external ones, which extends the DLP system functionality. Previously, functions of employees’ passwords reliability assessment and corporate accounts compromise (when an employee’s account is used by other staff members). Another method for account stealing attempt detection is the face recognition function. The system performs screenshots each time a user logs and notifies, if a third party does it.

Subscribe to our newsletter and receive a bright and useful tutorial Explaining Information Security in 4 steps!

Subscribe to our newsletter and receive case studies in comics!