The Risk Monitor system by SearchInform provides reports about each intruders’ attempt to bypass the established IS rules.
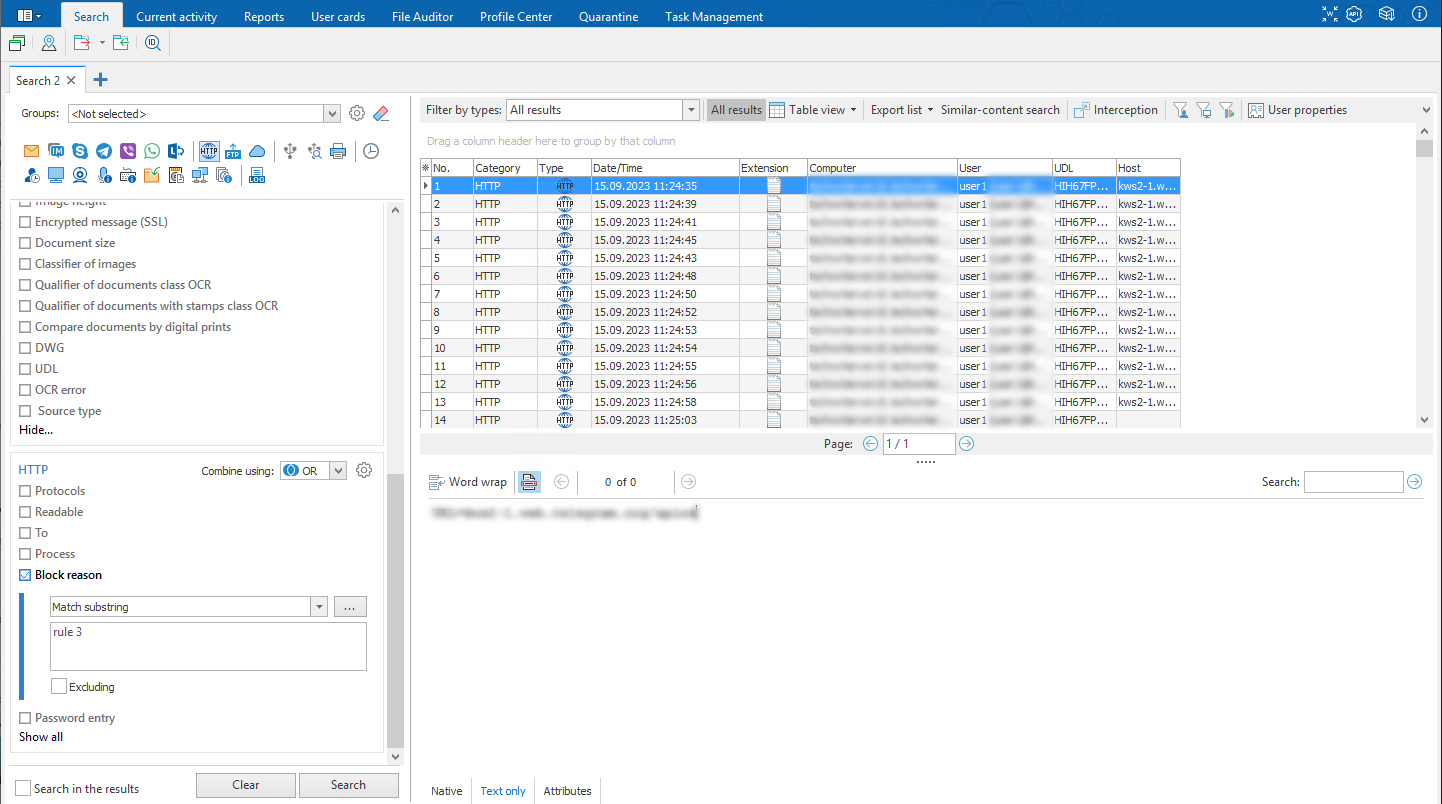
The updated version of SearchInform Risk Monitor system enables to control more precisely how employees comply with the corporate security policies set. From now on, the solution not only blocks employees’ potentially dangerous actions, but adds information on all the blockings activations to the specific report. It reveals, which user on which computer violated the established rules: for instance, attempted to copy a secret document to a flash drive.
Audit is also implemented for operations of data recordings to USB; printing operations; file transmition via email and messengers; attempts to bypass prohibitions to access websites and documents, containing SearchInform FileAuditor labels. Information security officer can view the list of violators in the main work console, by filtering the audit results by channel and activated blocking rule. Thus, even in case of incident prevention the employees in charge will be informed about the employees’ mistakes and deliberate malicious actions. This will help to fine-tune the infosec awareness campaign, aimed at enhancing users’ computer literacy and enhance monitoring of potential insiders.
“Audit is an important tool for assessment of the efficiency of security policies, implemented in the organization, as well as for detection of the weak points. Quite often malicious insiders, when they fail to steal information somehow begin to try some other options as well. The blockings’ audit enables to reveal the insider actions’ logic and proactively enhance protection.” – told Sergio Bertoni, the Leading Analyst at SearchInform.
SearchInform Risk Monitor has more than 10 types of blockings for all data transmission channels, both by the context (attributes) and content. Additional integration with the SearchInform DCAP class solution FileAuditor extends the capabilities, allowing to manage access to confidential data in arbitrary applications. Thus, SearchInform solutions’ capabilities for control of access to critical data outpace market competitors.
Click here to get a free trial of SearchInform Risk Monitor.

Subscribe to our newsletter and receive a bright and useful tutorial Explaining Information Security in 4 steps!

Subscribe to our newsletter and receive case studies in comics!