The global market of information security tools offers a wide range of DLP systems (Data Leak Prevention). And the demand for them is only growing. Companies already recognized DLP products as an integral part of the information security system but faced a problem of their choice. Comparing their characteristics and testing each system in combat conditions to pick the right one can be time-consuming and labor-intensive. Most InfoSec companies understand that the best way to choose is to try.
Where to Start?
Competent work statement will help to narrow down the choice at the preliminary stage. Selection criteria to be considered include:
- Number of controlled channels
- Reliability and speed of the system
- Analytical capabilities
- Expertise, experience and reliability of the developer
- Availability, quality and speed of the response from technical support
- Price and owning cost of the system.
The main requirement for a DLP system is the capability to prevent the leakage of confidential data through any channel used in the company. If the solution does not cover at least one channel, you should carefully study the other capabilities of the system and understand whether they compensate for the lack of the control over the necessary data channel.
The basic features of DLP systems also include monitoring the storage, use and transfer of critical documents within the corporate environment. A number of DLP systems are capable of encrypting data so that it could not be read when taken outside the company’s perimeter.
What DLP Systems Are Better?
Traditional classification includes two groups of DLP systems:
- Active which can block confidential information when violations are detected.
- Passive which can only observe data flows without interfering and influencing processes.

Modern leak prevention solutions are two-in-one systems that can work in both active and passive modes.
Combined use of the two modes in DLP systems provides an advantage already at the testing stage. The deployment of active DLP runs the risk of suspending smooth business processes due to incorrect settings or inefficient response to events. Installation of a DLP complex in a passive test mode allows checking whether the settings of monitoring and response rules are correct, whether traffic channels are under continuous control, and to prevent the overload of network infrastructure by logging and archiving systems.
Methods of architectural integration is the basis for another criterion for classifying DLP solutions.

Host DLP systems involve the installation of agent programs on users' computers. Agents monitor compliance with security policies and prevent potentially dangerous actions, for example, the launch of software from removable devices. Agents register all user actions and send information to a database. Thus, IS experts get a full picture of processes on the corporate network.
The main advantage of host solutions is a better control of information transmission channels and users’ actions in the workplace. Agents record all actions at the computer, and the most advanced DLP solutions allow you to record employee talks or, for example, connect to a webcam. The disadvantage of host systems is the limit of control to devices connected directly to workstations.
When choosing host DLP systems, you should pay attention to agent installation method. The method of remote installation and administration will relieve IS experts from manual installation of agents on each workstation.
Another important requirement for agent components of host DLP systems is a hidden mode of operation and protection from deleting. If a user has local administrator rights and above-average level of IT literacy, he/she can potentially stop the agents and remove the computer from the range of a DLP system.
Network DLP systems are based on the use of centralized servers where a copy of incoming and outgoing traffic is forwarded for checking against security policies. Network solutions provide a high level of protection against unauthorized exposure since they can restrict access to a dedicated gateway and grant administration rights to a limited number of employees.
Accordingly, the scope of network DLP systems is limited to network protocols and channels: SMTP, POP3, HTTP (S), IMAP, MAPI, NNTP, ICQ, XMPP, MMP, MSN, SIP, FTP, etc. The capability to monitor the most frequently used data transmission protocols can be the rationale for choosing network DLP solutions. Security administrators prefer network DLP solutions due to their easy integration and customization.
Host and network DLP systems control different data channels, and the logical step of developers was the integration of capabilities from various solutions. Almost all modern leakage prevention tools in the IS market are omni-purpose complexes.
Administration and architectural features of DLP systems should be considered together. It is necessary to compare the algorithms for the deployment of system components, the methods for allocating roles, and the integration of the management console. The security administrator must first assess the informative value of the interface, complexity of setting the rules and other parameters which should be taken into account for easy management of information security systems.
Analytical Capabilities of DLP Systems
Four parameters will help to determine if a DLP solution meets the company's objectives.
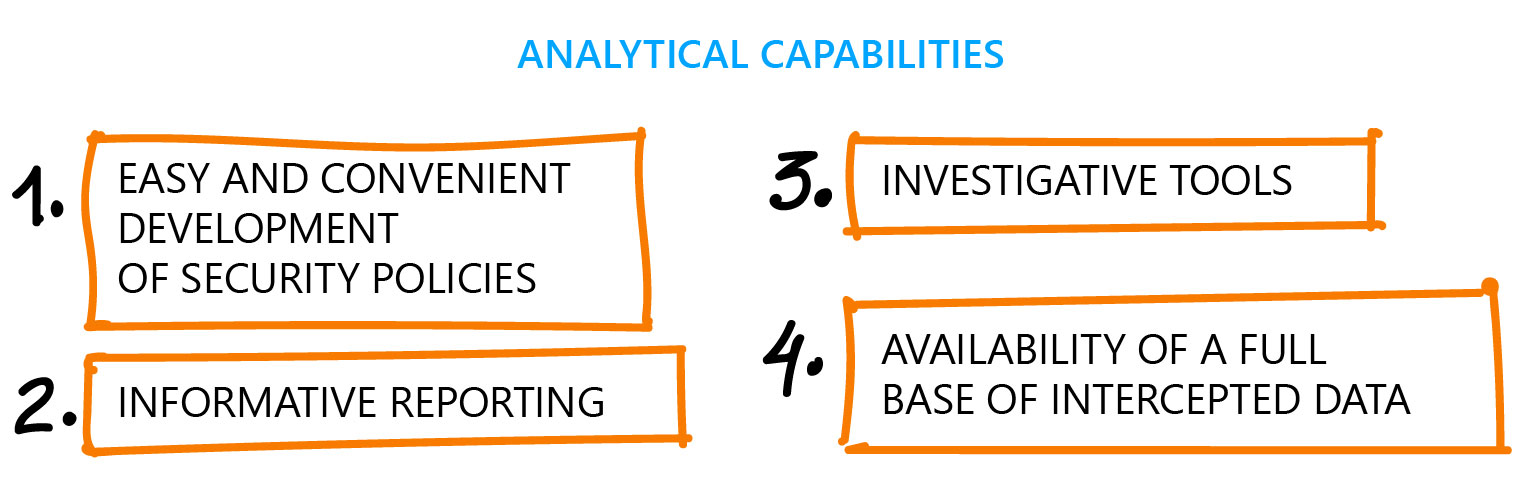

Reporting depends on the capabilities of a DLP system not only to monitor but also to archive the captured information. A shadow copy can contain different types of data: web traffic; mailing; printing activity; files saved to USB media, and information traversing network protocols. Shadow copying is an effective method to investigate incidents. However, not all DLP systems offer backup option because of the additional load on network resources and endpoints.
How Much Does a DLP System Cost?
The price is an important criterion that will narrow down the choice of solutions when developing requirements for a DLP system. Host and network systems are cheaper than omni-purpose ones. The general principle of pricing is reduced to a simple formula: the more additional options a solution has, the higher its total price is.
The price of a DLP system is directly proportional to the number of available advanced tools, including the feature of recognizing text in the image, modules of linguistic analysis, self-learning technologies and other features. The higher the requirements for the protection of corporate information and the higher the budget allocated for information security are, the more advanced a DLP system will be. Advanced features include:
- Capability to determine transliteration
- Bayesian analysis
- Use of signatures and regular expressions
- Digital print technology for analyzing documents with little change in structure and content
- Optical Character Recognition (OCR) modules and other high-tech tools of content analysis.
The cost of a DLP system is not only the cost of the system itself. Several expenditure items form the total price.
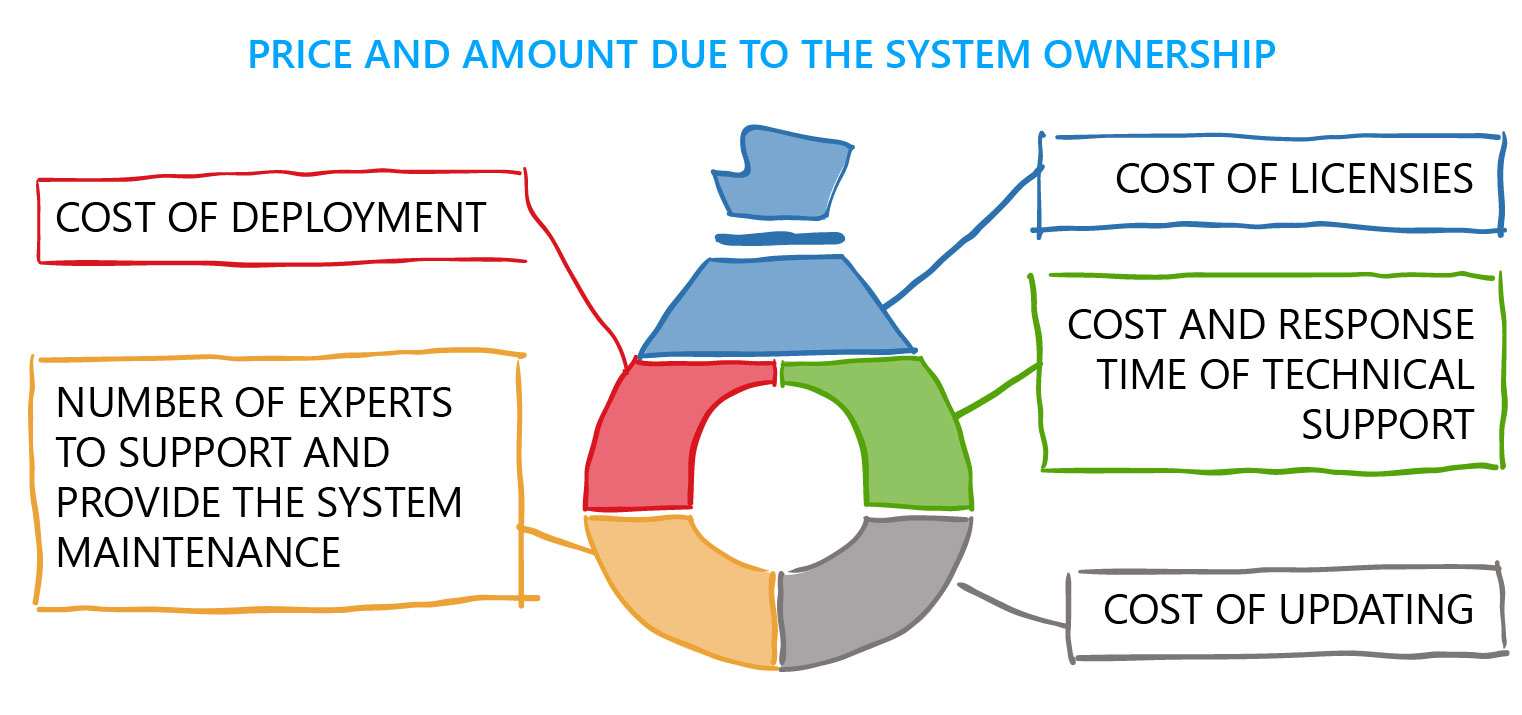
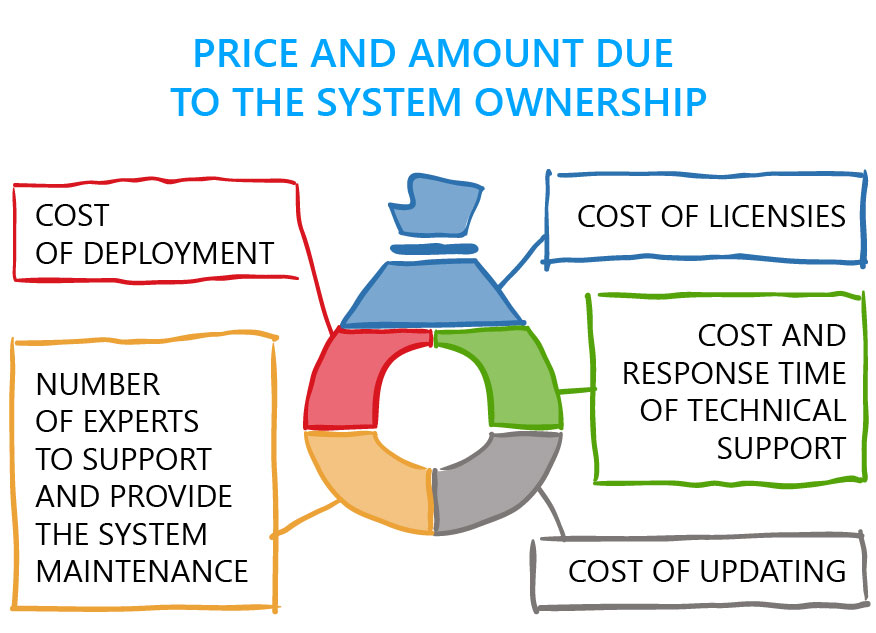
One of the ways to reduce the cost of the solution is to find out whether it is possible to purchase separate DLP modules in order not to overpay for unnecessary interception channels.
The Final Stage
Before choosing the right DLP solution, it is better to conduct tests under real load. For testing, you must select two-three systems in accordance with the statement of work and budget. The testing of a DLP system is preceded by the program development and test methodology. It will take from two weeks to a month to identify all the nuances and verify the software reliability. All you have to do in the end is to compare the results and select a DLP which would meet all criteria.

Subscribe to our newsletter and receive a bright and useful tutorial Explaining Information Security in 4 steps!

Subscribe to our newsletter and receive case studies in comics!