Security risk assessments are performed for the purpose of identifying, evaluating, and prioritizing risks associated with a company’s use and operation of information systems to its operations and assets. These risks are quantified in terms of the financial losses they could incur. They are calculated based on what the particular income source of the organization is and how that is affected by the company’s assets and employees. After weighing which of your risks are the highest impact, you can address them in the corresponding order as well as considering upgrading your IT infrastructure in order to minimize potential losses as much as possible. A security risk assessment is performed in several steps: first, the asset must be characterized, then the threat is assessed, followed by assessment of the vulnerability, evaluation of the risk, and finally treatment of the risk.
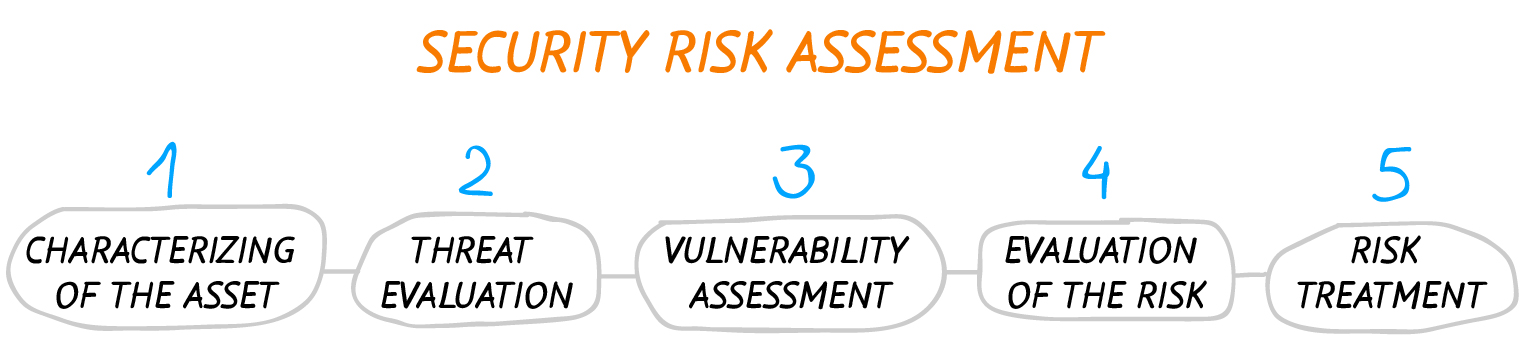
Information Security Risk Assessment Matrix
Prudent security risk management involves a clear, concise representation of the overall risk that a potential event would bear. This can be achieved by using a security risk assessment matrix. A security risk assessment matrix entails a chart with its likelihood as the vertical axis and its potential impact as the horizontal axis, together representing the overall risk of the event. An independent security risk assessment solution is worth the risk of covering your bases in order to boost your company’s resiliency. These companies will provide you with a security risk management system that will not only build you a security risk matrix of all sorts of risks you may not have considered, it will also continually update your system since your company’s technology and operations are not static. Furthermore, the security risk assessment software will suggest additional solutions to you that could make a hacker’s job more difficult. Examples, such as having a security employee sit outside the office, rather than inside have worked wonders in the past. Another one is having your website hosted on a secure cloud.
Perform risk assessment now! Request free trial
When based on the IT security risk matrix you discover risks that are too impactful to leave up to chance, of which there are many, common practices may be employed to mitigate these risks, such as end-user training, making operations more stringent, and policy evaluation. Potential valuable assets of your company that the security risk matrix will display as some of the highest risks for victimization resulting in monetary loss include your servers, website, client contact information, customer credit card data, partner documents, and secrets that give your business a competitive advantage. The security risk assessment and audit will advise you of potential data loss, system or application downtime, and legal consequences, so that you can mitigate them in the event that they do occur. Security risk assessment and management also consider potential natural disasters, the possibility of malicious intentions on employees’ part (fraud, bribery, intentional harm to the company, embezzlement, etc.), or accidental human interference by accident.
SearchInform uses four types of cookies as described below. You can decide which categories of cookies you wish to accept to improve your experience on our website. To learn more about the cookies we use on our site, please read our Cookie Policy.
Necessary Cookies
Always active. These cookies are essential to our website working effectively.
Cookies does not collect personal information. You can disable the cookie files
record
on the Internet Settings tab in your browser.
Functional Cookies
These cookies allow SearchInform to provide enhanced functionality and personalization, such as remembering the language you choose to interact with the website.
Performance Cookies
These cookies enable SearchInform to understand what information is the most valuable to you, so we can improve our services and website.
Third-party Cookies
These cookies are created by other resources to allow our website to embed content from other websites, for example, images, ads, and text.
Please enable Functional Cookies
You have disabled the Functional Cookies.
To complete the form and get in touch with us, you need to enable Functional Cookies.
Otherwise the form cannot be sent to us.

Subscribe to our newsletter and receive a bright and useful tutorial Explaining Information Security in 4 steps!

Subscribe to our newsletter and receive case studies in comics!