Encryption and Decryption in Network Security
Encryption involves a plain text being coded into “encrypted” form using a cipher text and then being “decrypted” with a cipher text by the recipient on the other end. As a rule, encrypted data are processed via an advanced mathematical algorithm with a key that must be acquired in order to access the data contained on the digital medium. Encryption algorithms in network security come with a key that serves as the doorway for all information to be accessed on the medium, drive, disc, or storage structure.
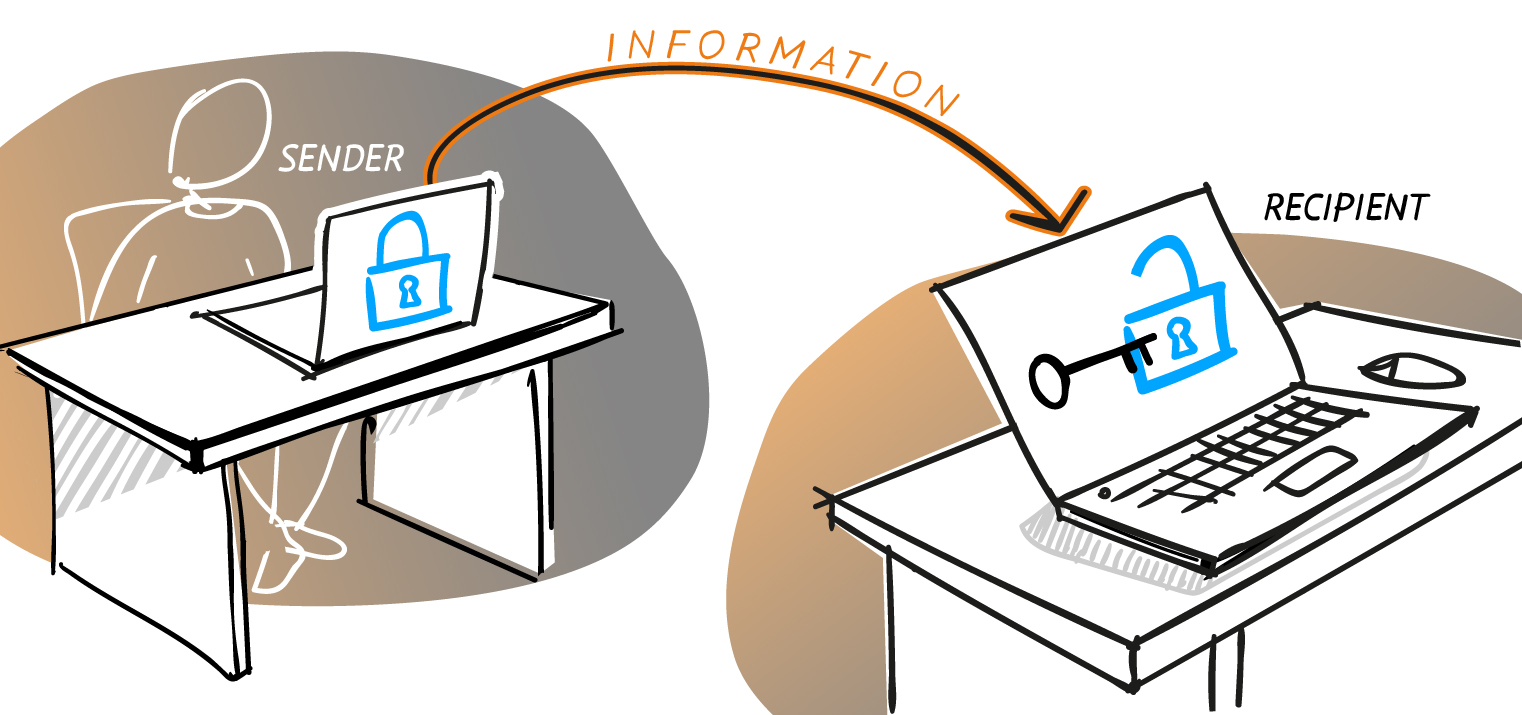
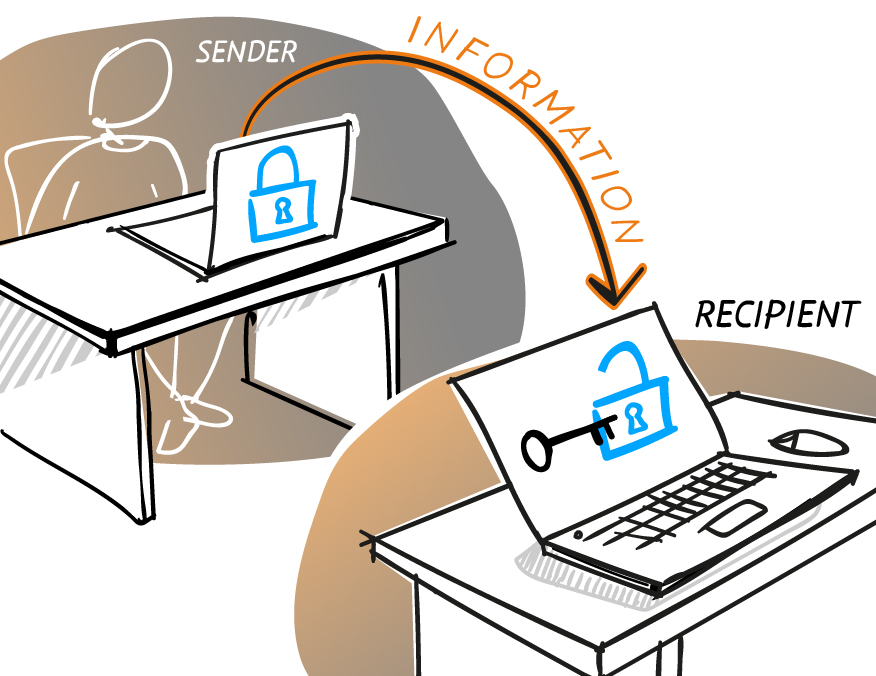
There are two types of encryption: symmetric (or secret key encryption) and asymmetric (or public key encryption). Asymmetric encryption requires two keys – one private key and one public key – rendering it slower to process data access. On the other hand, despite that it protects the majority of data on the Internet, the downside of symmetric encryption is that it requires both parties to have the key in order to decrypt the medium. For the most part, asymmetric encryption is used in ordinary communication channels, particularly via the Internet as well. There are many encryption algorithms used to make messages unavailable to criminals – one such algorithm which is very popular is Advanced Encryption Standard.
Software Solutions
For greater security, there are specially developed data encryption software providers with their own algorithms designed to protect your information and assets based on their best stab to take advantage of how encryption software works. In the past, data security was not as much of an issue with the firewall; however, as of late, due to its flexibility and convenience, companies have begun to store their information on clouds, including copies of their most essential files. This has rendered them vulnerable to data loss, rendering cloud encryption an imperative.
SAFEGUARD DATA UPLOADED TO THE CLOUD
Microsoft Office
Be sure that you encrypt your most important files on your computer. On Microsoft Office, there are some issues with data security that render data less secure than on Apple computers. For instance, data must be encrypted manually, ideally an entire drive, and passwords to access files do not offer sufficient protection. Also, users at times encounter the “encrypt contents to secure data greyed out” problem. That issue has to do with the file’s registry values. You will be able to encrypt contents to secure data after you reset them.
Data at Rest vs. Data in Transit
Many people seem to believe that encryption of data in transit should be their first concern since it is always moving around; however, considering that it is the most valuable information, it is data at rest encryption that should be taken care of first and foremost. After all, that’s what cyber criminals are mostly after. They go where the money is – social security numbers, credit card information, company secrets, financial information, etc. Furthermore, they are well aware that data at rest are often not protected at all and thus prefer to take the path of less resistance anyway.
Sign up for a free trial
SearchInform uses four types of cookies as described below. You can decide which categories of cookies you wish to accept to improve your experience on our website. To learn more about the cookies we use on our site, please read our Cookie Policy.
Necessary Cookies
Always active. These cookies are essential to our website working effectively.
Cookies does not collect personal information. You can disable the cookie files
record
on the Internet Settings tab in your browser.
Functional Cookies
These cookies allow SearchInform to provide enhanced functionality and personalization, such as remembering the language you choose to interact with the website.
Performance Cookies
These cookies enable SearchInform to understand what information is the most valuable to you, so we can improve our services and website.
Third-party Cookies
These cookies are created by other resources to allow our website to embed content from other websites, for example, images, ads, and text.
Please enable Functional Cookies
You have disabled the Functional Cookies.
To complete the form and get in touch with us, you need to enable Functional Cookies.
Otherwise the form cannot be sent to us.

Subscribe to our newsletter and receive a bright and useful tutorial Explaining Information Security in 4 steps!

Subscribe to our newsletter and receive case studies in comics!