A joint study of universities and Illinois and Michigan showed that 48% of people connect accidentally found flash drives to their computers. We have translated the key messages and conclusions that show why it is important to consider user behavior to protect information.
When you attend any security conference, you will inevitably hear white hackers boasting that they can hack any company's security system by scattering flash drives with malicious code in the parking lot of that company. This story is so popular that it was filmed in the sixth episode of Mr Robot. Thoughts involuntarily come to mind - does such an attack actually work or is it just a myth?
In order to test this attack, researchers scattered about 300 flash drives on the territory of the University of Illinois at Champaign-Urbana and calculated how many people connected them to computers. It turned out that users picked up, connected and clicked on files 48% of the flash drives we had scattered. And they did it quickly: the first flash drive was raised in less than 6 minutes.
Experiment
To test whether users are actually picking up flash drives found on the ground, scientists scattered five types of flash drives on the territory of the University of Illinois: flash drives with an "exam" or "confidential" sticker, flash drives with keys attached to them, flash drives with keys and a sticker with a return address , as well as regular flash drives without any stickers.
Files corresponding to the sticker on the flash drive were recorded on each flash drive:
- personal files for flash drives without stickers, flash drives with keys and flash drives with a sticker with a return address;
- business-related files for USB sticks with a confidential sticker;
- files with information on exams for flash drives with the inscription "exams".
All files were actually HTML files with an embedded image from our server. This allowed the researchers, without executing any code on the user's computer, to detect whether the flash drive was connected and whether the file was opened. As soon as the user opened the HTML file, a question appeared: would the user want to take part in the study, answering the question why he connected a USB flash drive, and receive a gift card for this. 62 users (about 20%) agreed to answer.
Placing infected flash drives is very effective for hacking a computer
So how effective is it to throw away USB sticks with malicious code in order to hack computers? It turned out to be very effective: 48% of the scattered flash drives were not only connected to the computer, but also opened by users at least one file on each of them. The surprisingly high rate of success proves the fact that flash drive attacks are a real threat, and underlines the need to educate and educate users about the dangers of connecting unverified flash drives.
Scattering malicious code sticks pay off very quickly
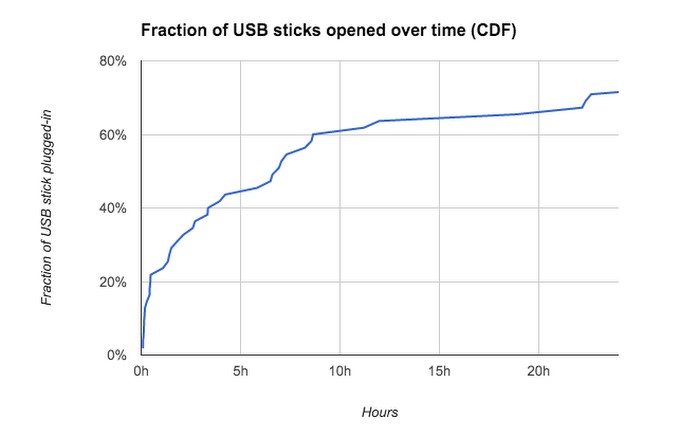
Besides the fact that many people connect USB sticks, they do it very quickly. 20% of the connected flash drives were connected within the first hour, and 50% of the flash drives were connected within 7 hours, as you can see from the graph below.
This means that the time interval for detecting an attack is very short. In this case, the first reports about the presence of strange flash drives on the campus began to appear on Reddit about a day after the first wave, but this did not stop people in their desire to connect decoy USB flash drives.
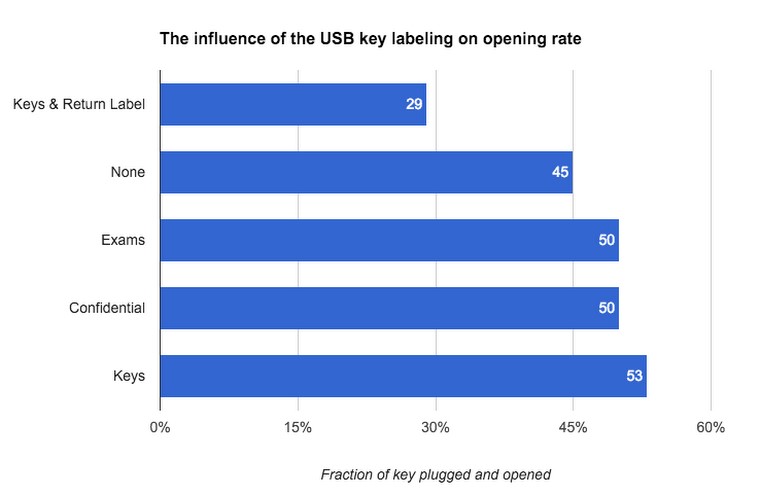
The way the flash drive looks is of some importance.
As you can see in the diagram below, flash drives with curiosity stickers are more likely to be opened than flash drives without any distinctive markings. Surprisingly, attachment of physical keys yields the greatest results - altruistic behavior is the most common reason for browsing flash drives. Keys with the owner's contact information were rarely opened because there was a way to find the owner. Please note that the difference in the frequency of opening is NOT statistically significant, except that flash drives with a return address were connected less often.
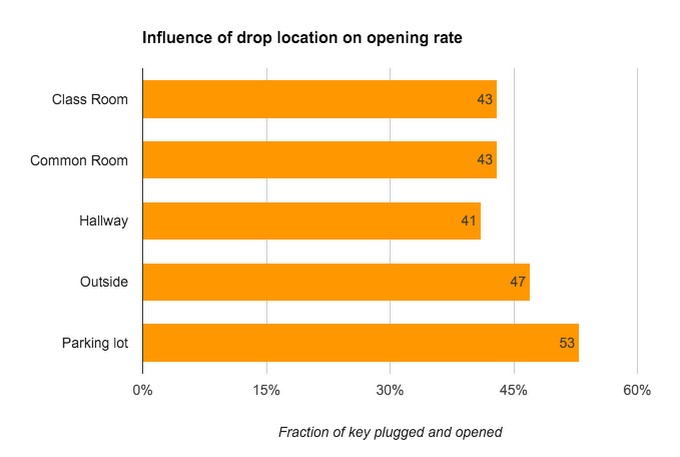
The location for opening the infected flash drive does not matter
As you can see from the chart below, the opening frequency for each location is approximately the same. This confirms the fact that a hacker does not need to penetrate the victim's territory in order to conduct an attack effectively. Placing a USB stick in a parking lot is just as effective as in a secure conference room.
Everyone is vulnerable to attacks via a randomly found flash drive
Everyone is vulnerable to a flash drive attack: the researchers found no difference between demographics, security awareness, and education of users who plugged in the flash drives.
Why the study does not show a negative correlation between education in information security and vulnerability, think for yourself. But the question inevitably arises about the effectiveness of information security training. The subject seems to be worth exploring in order for information security training to really help people be more secure.
User motivation
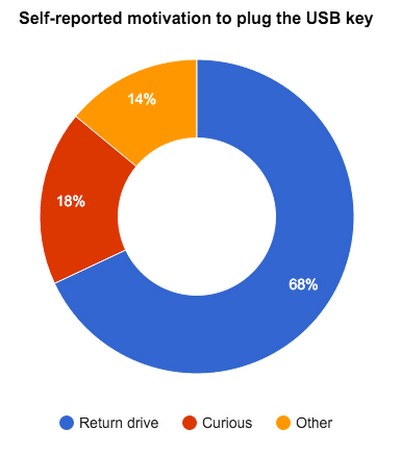
Motivation in the responses of users: when asked why they connected the USB flash drive, the majority of the respondents answered that they did it for altruistic reasons in order to return the flash drive to the owner (68%). As you can see from the chart below, only 18% said they were motivated by curiosity.
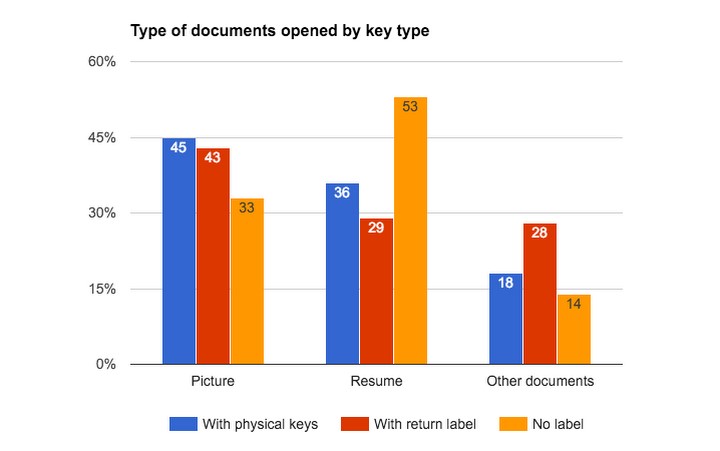
Observed Motivation: As you can see from the diagram below, the motivation in user responses does not match which files were opened. For example, for flash drives with physical keys attached, users were more likely to click on a photo from their winter vacation than on a resume, which could find the owner's contact information. It is noteworthy that the same behavior was observed in relation to flash drives with a return address, but not in relation to flash drives without marking.
The results of this study show that USB security is a real issue and USB stick throwing is a cheap and practical hacker attack tool.
16.12.2020
