SearchInform Solutions’ 2023 Updates: Migration to PostgreSQL, Informative Metrics and Control of FTP Connected Servers
20.09.2023
Back to blog listIn the digest on SearchInform solutions’ updates we’ve gathered details on a few major updates up to date. In the overview you’ll find details on our flagship Risk Monitor and FileAuditor solutions’ new features, including: migration to PostgreSQL; new metrics and blockings; control of corporate FTP-servers and even more.
1. MIGRATION TO PostgreSQL
SearchInform RM and FileAuditor migrated to free open-source database management system PostgreSQL. From now on, all the traffic from users’ PCs, incidents, emails in Quarantine, security policies and reports, data on DLP system configuration, as well as data on file operations, access rights and results of files’ classification by DCAP solution are kept in these databases.
PostgreSQL is the free and open-source database management system (DBMS), which is capable of creation, keeping and extraction of complex data structures.
2. NEW DASHBOARDS IN DATACENTER
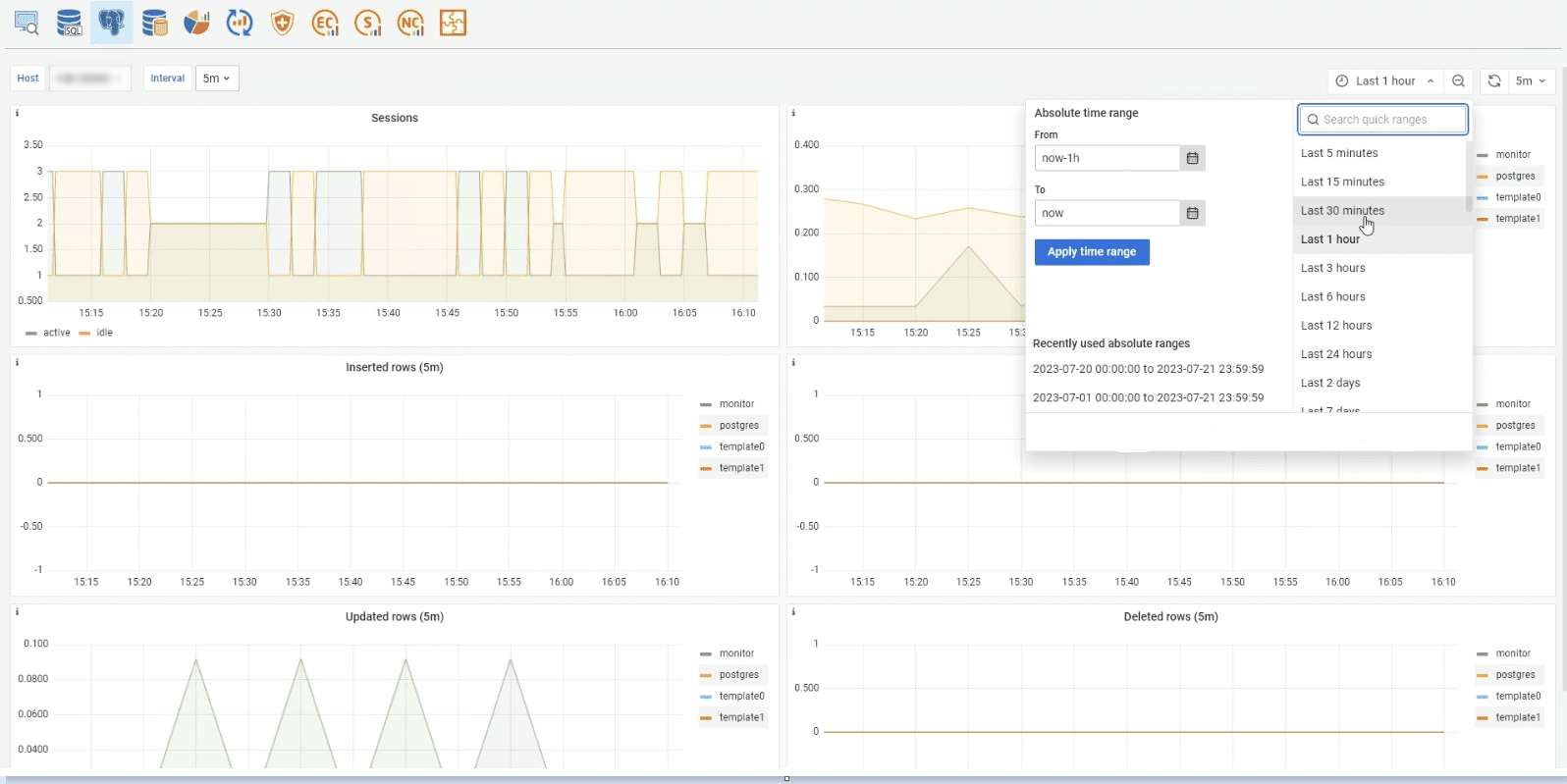
2.1 POSTGRESQL Metrics
It’s possible to trace the PostgreSQL server work process in DataCenter in the Monitoring tab. Metrics show data on databases records; data on transaction; added, updated and deleted strings in the DataBase table, as well as data on transactions rollbacks, which result into cancellation of all changes. IS officer can specify any time interval for displaying data: an hour, 24 hours, month, year etc. What’s more, it’s possible to specify time interval for data recording.
2.2 NetworkController metrics
NetworkController metrics were added to the DataCenter as well. They enable to monitor the server’s main attributes: CPU and memory load, packet processing speed, processing errors, data on mail servers integration and more.
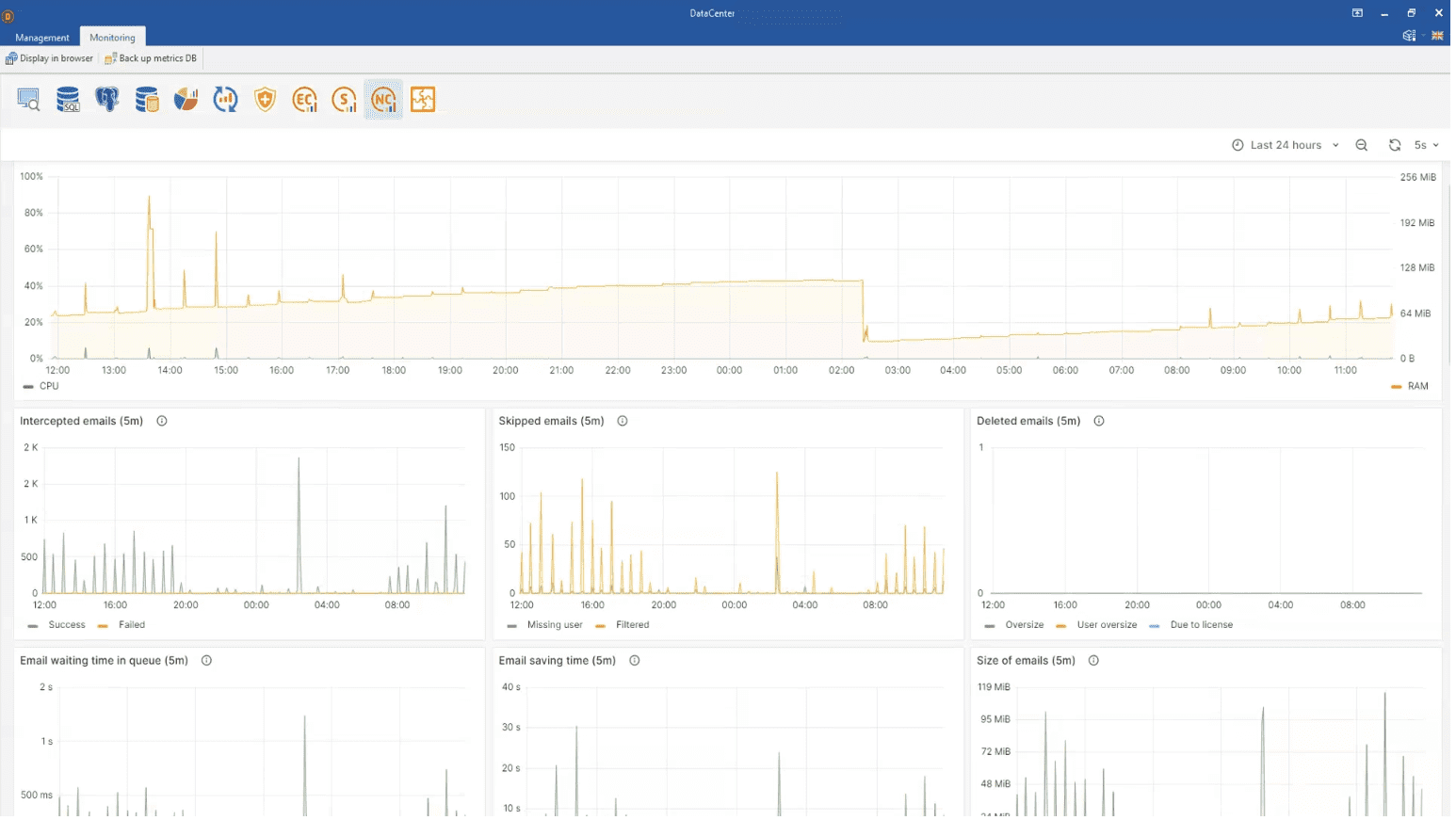
NetworkController is the platform, which performs network interception of data from employees’ workstations. The data gathered is processed by parsers, which deal with the task of extracting useful data (text of a message / attachment / metadata) from the overall data flow and add this data to the DataBase. NetworkController components are included in the EndpointController console.
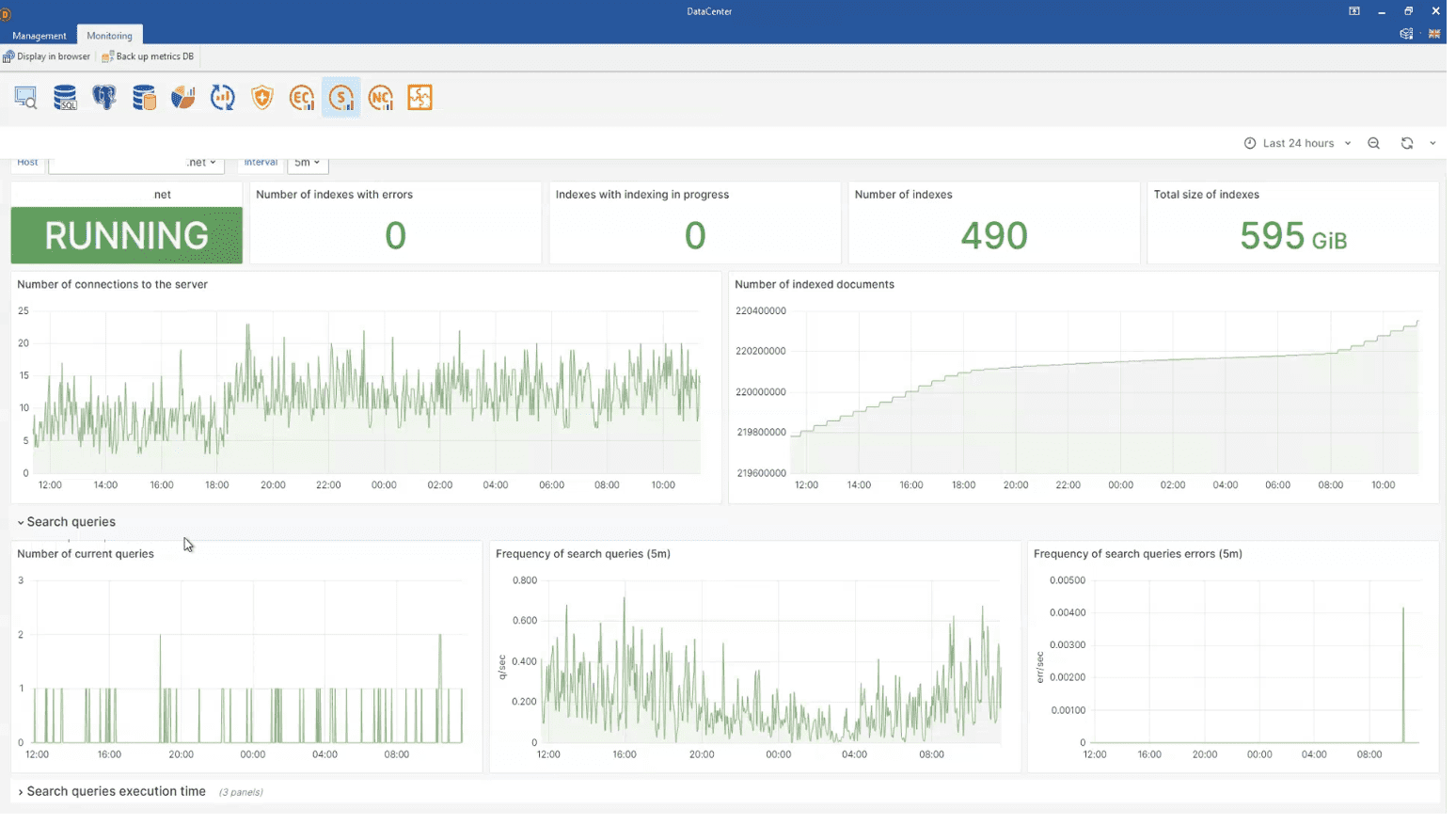
2.3 SearchServer metrics
When data is added to the database, SearchServer proceeds to processing of this data. SearchServer is the SearchInform’s search engine, which performs obtained data indexing and search among the gathered data. With the help of this engine indexes are created for the data, containing text. Simultaneously, data, which initially doesn’t contain text isn’t indexed and is available for search as data bases. This refers to screenshots, audios, operations with files (deleting, renaming etc.) and devices (connecting and disconnecting devices etc.), activated processes and websites visited.
From now on in SearchServer metrics in DataCenter enable to trace:
- Data on resource consumption by indexers.
- Speed of indexing.
- Error counter.
- Search queries and more.
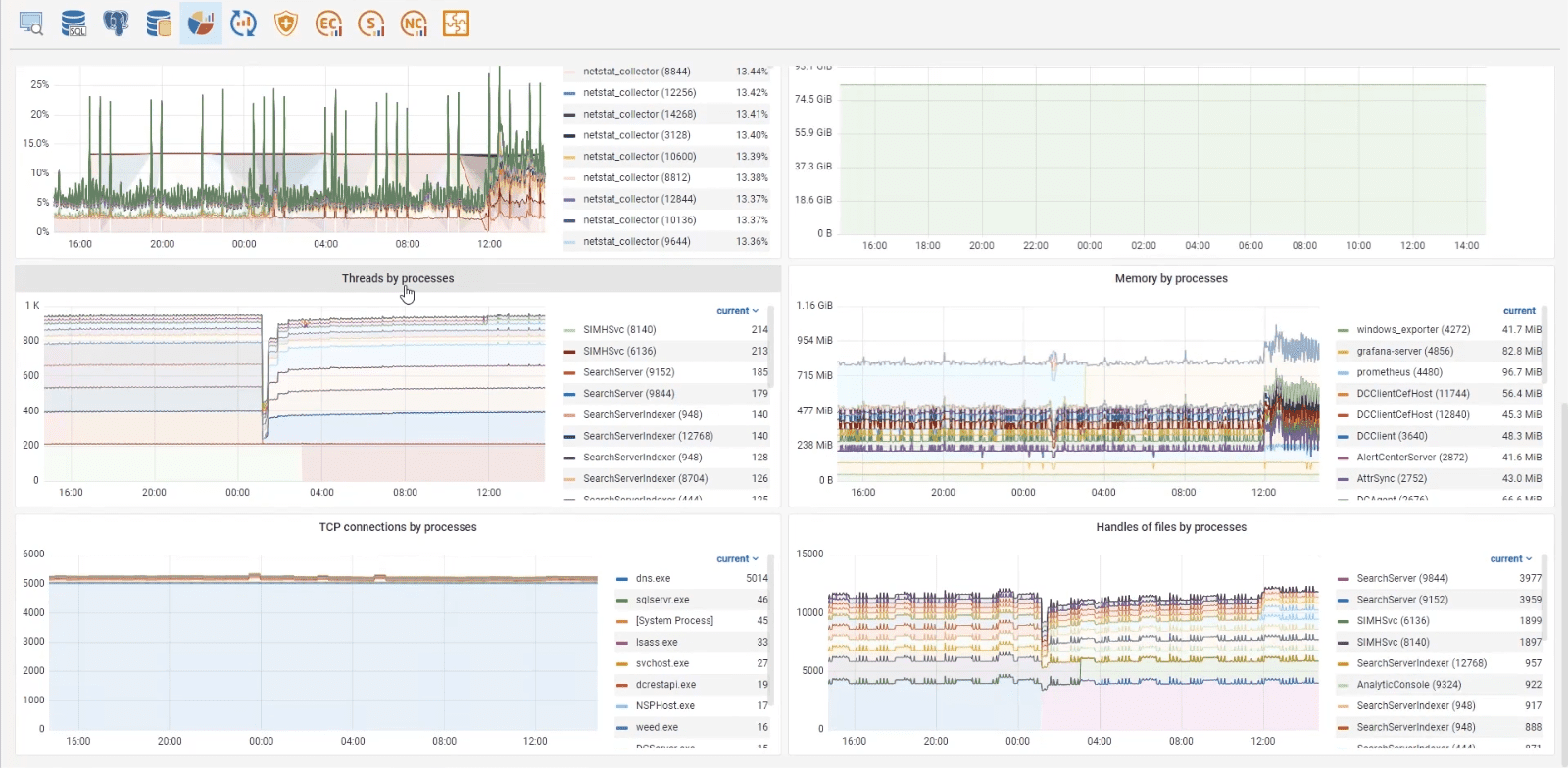
2.4 OS metrics
OS metrics dashboard, available in Monitoring was updated. It shows data on the state of server, on which DLP system is deployed. New widgets show the percent of virtual memory file usage at the present moment and percent of selected disk load as well. Data on the number of active flows, open ports and descriptors of each process is also presented in the form of scales. Metrics enable to trace overloaded resources. For instance, reveal suspicious increase in load on drive C, which may indicate failure of one of the drives in the RAID.
3. EXTENDING OF BLOLCKINGS’ FUNCTIONALITY
3.1 Blocking of printing operations basing on content
Settings of rules for Blocking of printing operations according to the content in Endpoint Controller were updated. Now it’s possible to specify the number of pages, which employees may print. It’s enough to simply tick the required field and choose or input the desired number. For example, this number may be limited to 5 pages.
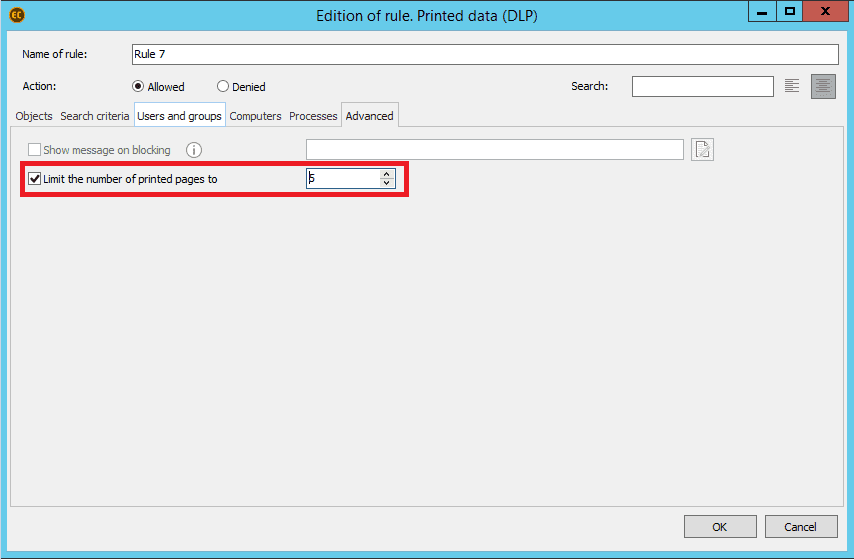
What’s more, from now on it’s possible to notify users about blockings. When configuring blocking rule IS officer can input any phrase or word, which will be shown to user in case he/she attempts to print the restricted file.
3.2 Notification on blocking of operations with files
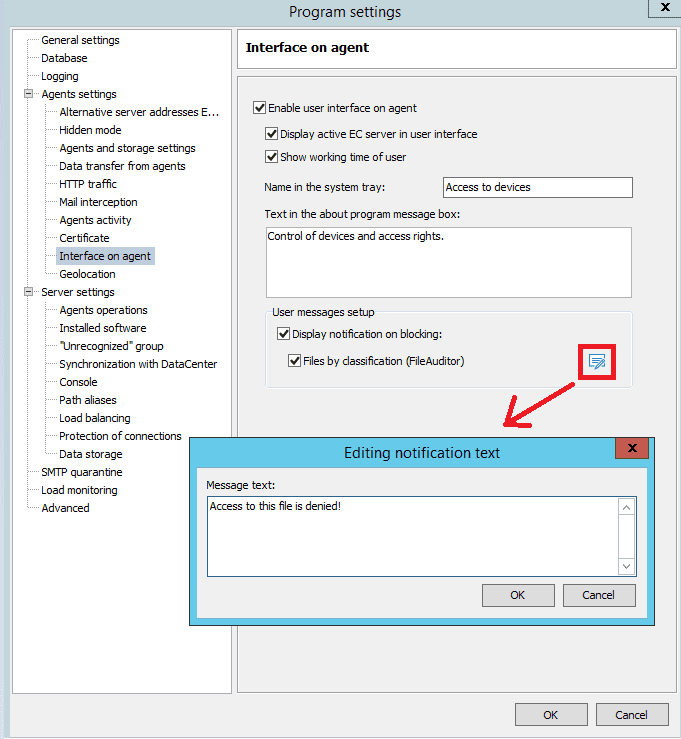
From now on it’s also possible to send user a notification if he/she attempts to open a file, to which employee doesn’t have legitimate access (this functionality is provided by SearchInform FileAuditor). The IS officer can add the required text of notification in EndpointController program settings, in the Interface on agent section. It’s enough to activate notifications for files according to the classification by FileAuditor and add the text of notification. If the interface is activated, a user receives notification, that he/she doesn’t have access rights to work with the file.
3.3 New categories of blocking rules
New categories of blocking rules were also added to the SearchInform RM. Drag and Drop section helps to deal with the task of configuration of rules, which control operations of file capturing and dragging with the mouse.
USB without metadata support enables to control USB devices with file systems, which don’t support Alternate Data Streams: in other words, NTFS file system object’s metadata. Such devices pose a threat for information security because they doesn’t allow to implement automatical and manual classification labels. From now on, it’s possible to prohibit usage of such devices.
From now on IS officers can block usage of browser extensions, for example, VPN-extensions in Chrome. VPN encrypts traffic, thus, when the extension is activated, DLP systems may miss operations of data transmitting. This, obviously, increases the risk of data leak incident occurrence. The function of extensions blocking helps to prevent data leaks.
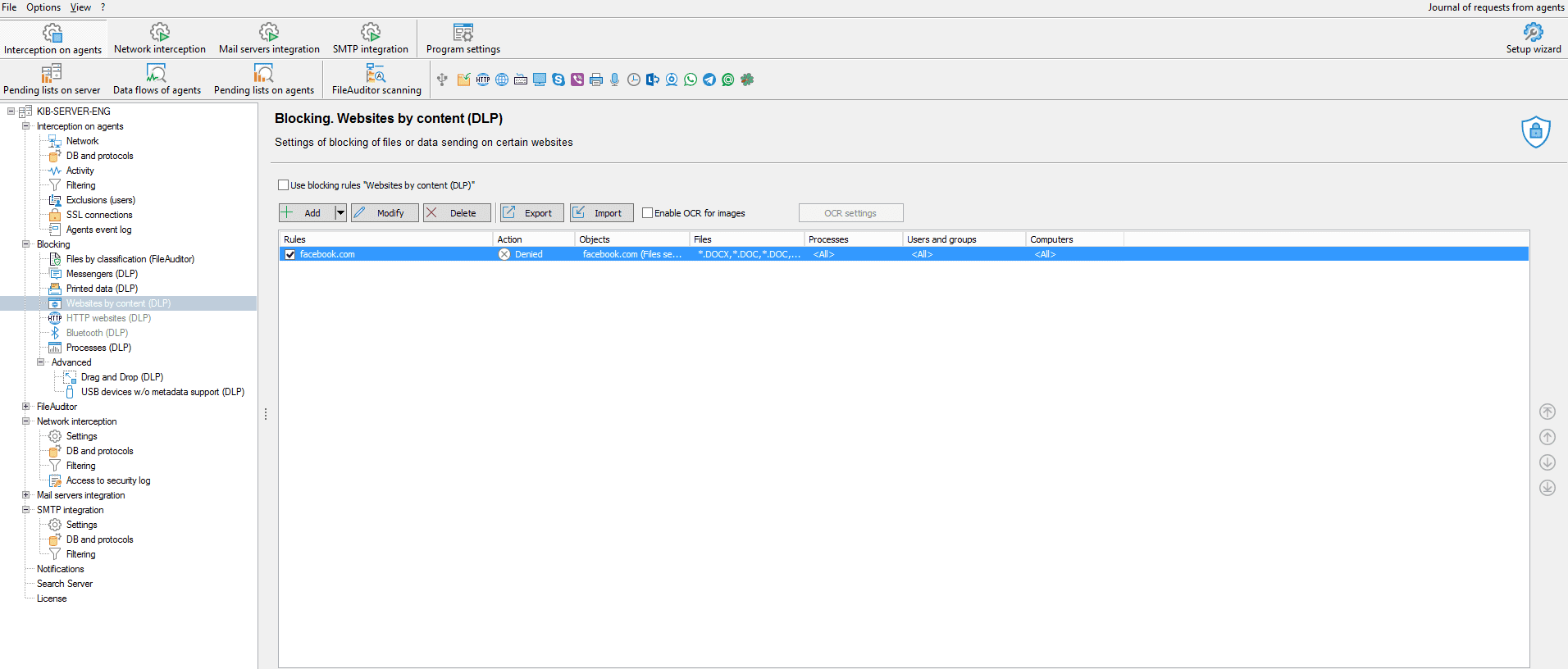
3.4 Blocking of sites according to the content
In the Websites by content section templates for blockings of operations on Facebook were added. This functionality enables to speed up the process of blockings configuration, aimed at control of desktop versions of social networks usage. For rapid configuration of rule it’s required to press the guiding arrow on the right from the Add button and choose the website. If required, it’s also possible to specify additional conditions, e.g. choose the user or the group of users, whom the blocking will be applied to.
4. CONTROL OF DATA, SENT VIA DISCORD
From now on, in IMController it’s possible to control data, transmitted via Discord. The system reveals:
- Who sent the message
- To whom the message was sent
- When the message was sent
- The number of messages sent
- Whether there were any attachments and if files attached contained confidential data.
5. UPDATE OF TASK MANAGEMENT SETTINGS
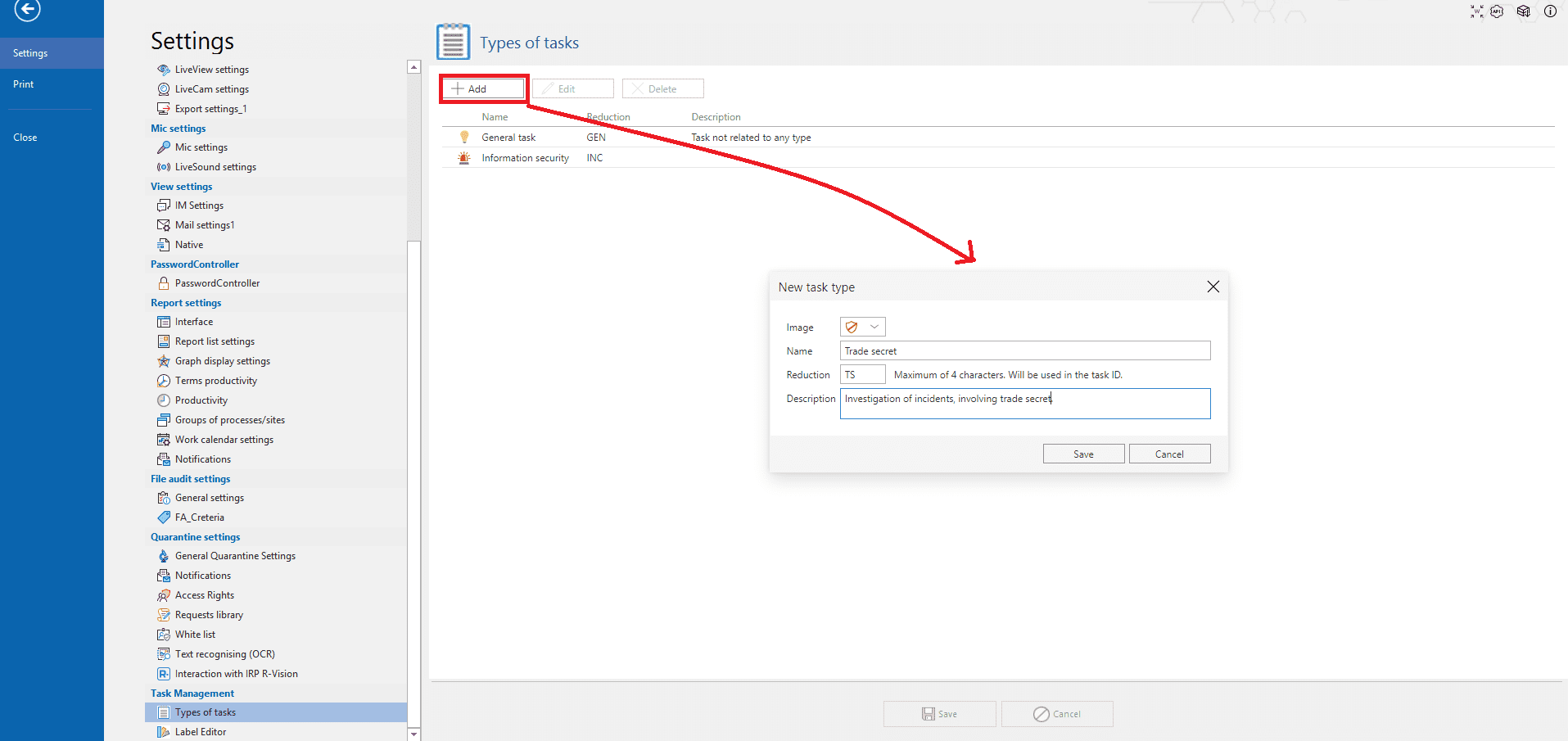
In the Analytic Console settings you can specify new parameters for Task Management. Types of tasks enables to add users’ filters. This enables to divide tasks in the manner which is comfortable for the IS officer, not the way it was initially configured in the system. IS officer can specify such parameters, as Image, Name, Description etc. for the new filter.
The second update of Task Management is editor of user labels. With its help you can create your own labels for illustrative indexation of tasks in the list; specify label’s color and name.
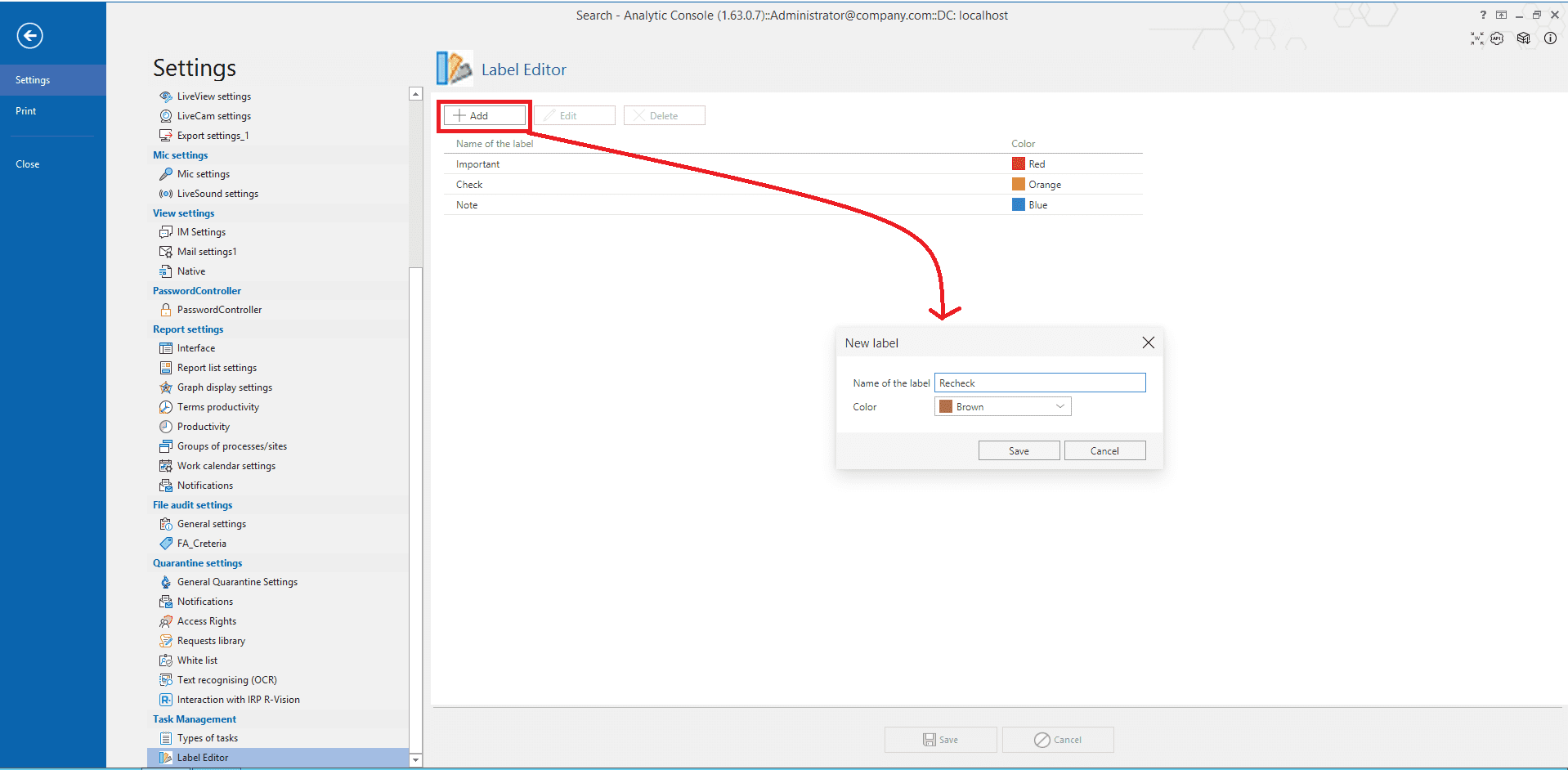
It’s possible to apply the new filters when creating a new task or when editing existing one. Please note: new categories may be added only to active tasks.
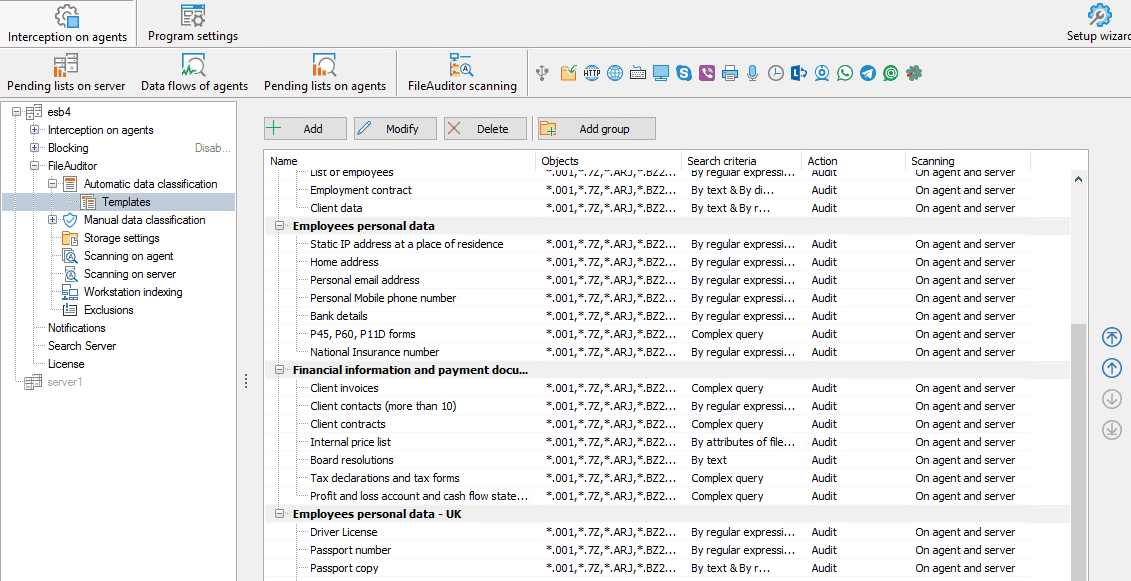
6. RULES FOR AUTOMATED DATA CLASSIFICATION
The process of rules configuration for SearchInform FileAuditor has become even more simple and quick, thanks to the pre-configured data classification rules. For IS officers’ convenience the templates are divided into thematic categories: intellectual property, financial data and payment details, keeping of passwords etc. The list includes, but isn’t limited to:
- Personal data
- Correspondence
- Agreements
- Acts
- Tax documents
- Financial documents.
To start the work process, it is enough to choose the required rule from the list. What’s more, the rules can be configured according to client's own requirements, complemented with client’s own samples, or they may be simply activated – the system will immediately start to work automatically.
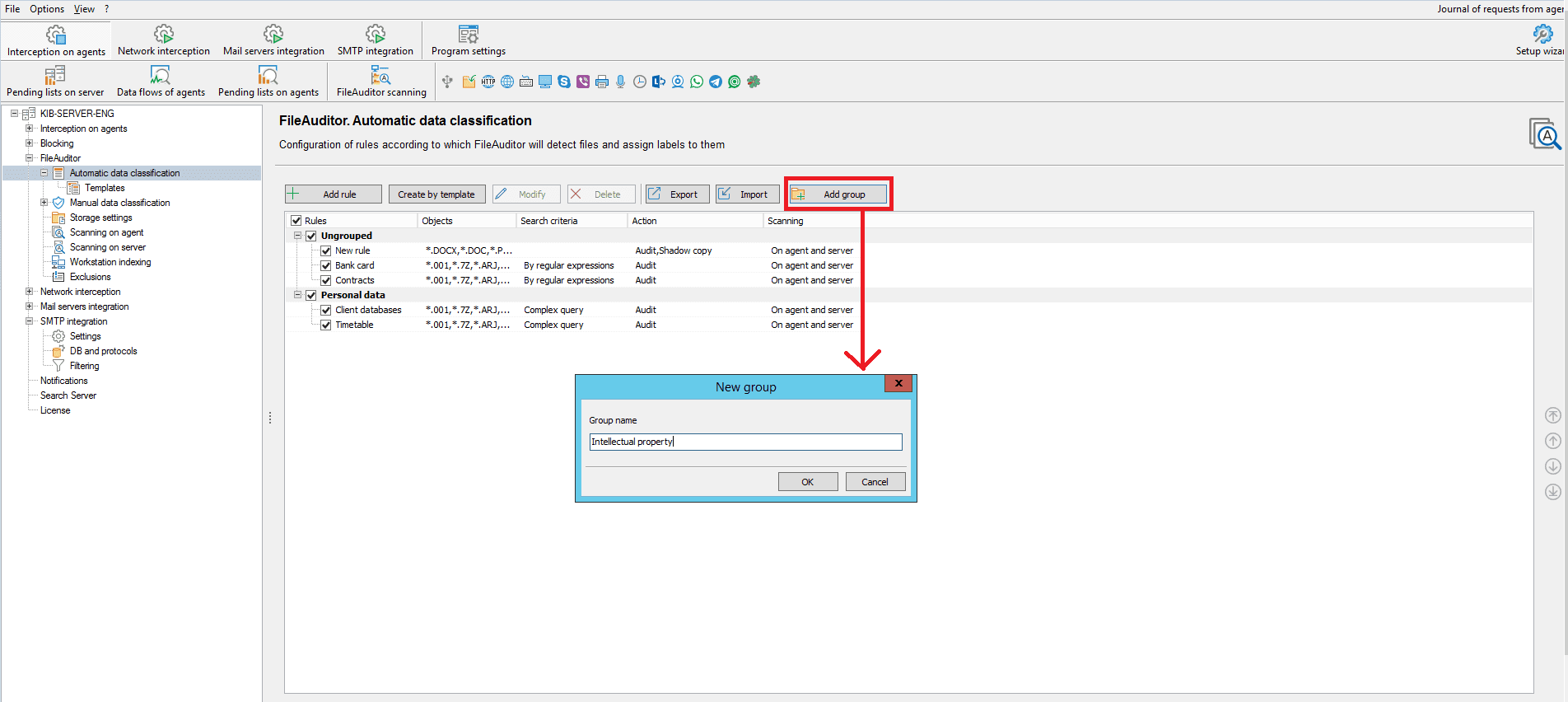
Besides, from now on it’s possible to create logical groups for more detailed representation of the list of rules. It’s required to press the Add group button, input the name in the opened window and save it. You can add the rule to the group when creating the new or editing existing one. To do it it’s required to open the rule editor, choose the required group (to which the rule should be added) and save changes.
7. CONTROL OF FILES, TRANSMITTED VIA FTP
The final update – expanding of FileAuditor’s capabilities for control of network storages. From now on the solution enables to control corporate file servers, connected via FTP. File Transfer Protocol is still quite popular among customers and is used for transmitting large troves of data: archives, documents, data bases, drawings, software and other large files. That’s why it’s crucial to ensure appropriate control of transmition of files via FTP. In terms of functionality, SearchInform FileAuditor scans resources over FTP protocol just like it scans network folders, in other words, OS of the file server doesn´t matter.
It’s useful to perform audit not only in terms of security, but in order to prevent cases of irrational resource usage as well. Sometimes employees overload storages with their personal photos, audios and videos.
Types of protocols used:
- FTP – FileZilla, Serv-U, Windows Server 2016, Windows Server 2022, vsFTPd
- FTPS – Serv-U, vsFTPd.SFTP – Serv-U, freeFTPd, software SFTP Server, vsFTPd.
All in all, thanks to the set of updates:
- Protective solutions' capabilities are extended, e.g. control of new data transfer channel is ensured
- Data on numerous important processes may is easily obtained and visualized in a representative form, what makes sure that important details are always in sight
- Offers new functionality for advanced blockings, aimed to prevention of data related incidents and contributes to the task of enhancing employees' information security awareness.
To learn more about protective solutions by SearchInform please feel free to contact our experts, you may email to: order@searchinform.com.
You may also refer to our Blog and Resources on our website to find more useful information on how to protect your organization and see protective solutions by SearchInform in the most efficient manner.

